Abstract
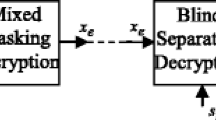
This paper introduces a new speech cryptosystem, which is based on permutation and masking of speech segments using multiple secret keys in both time and transform domains. The main key is generated, randomly, using a Pseudo Noise (PN) sequence generator, and two other keys are generated from the main key to be used in the subsequent rounds of encryption. Either the Discrete Cosine Transform (DCT) or the Discrete Sine Transform (DST) can be used in the proposed cryptosystem to remove the residual intelligibility resulting from permutation and masking in the time domain. In the proposed cryptosystem, the permutation process is performed with circular shifts calculated from the key bits. The utilized mask is also generated from the secret key by circular shifts. The proposed cryptosystem has a low complexity, small delay, and high degree of security. Simulation results prove that the proposed cryptosystem is robust to the presence of noise.
Similar content being viewed by others
References
Abd El-Samie, F. E. (2009). An efficient singular value decomposition algorithm for digital audio watermarking. International Journal of Speech Technology, 12(1), 27–45.
Advanced Encryption System (2001). Federal Information Processing Standards Publication 197.
Andrade, J. F., Campos, M. L., & Apolinario, J. A. (2008). Speech privacy for modern mobile communication systems. In IEEE international conference on acoustics, speech and signal processing.
Anoop (2007). Public key cryptography—applications algorithm and mathematical explanations.
Behnia, S., Akhshani, A., Mahmodi, H., & Akhavan, A. (2006). A novel algorithm for image encryption based on mixture of chaotic maps. Chaos, Solitons and Fractals.
Bradley, E. (1995). Autonomous exploration and control of chaotic systems. IEEE Transactions on Systems, Man, and Cybernetics, 26(5), 499–519.
Daemen, J., & Rijndael, V. R. (2001). The advanced encryption standard. Dr. Dobb’s Journal, 26(3), 137–139.
El-Fishawy, N., & Abu Zaid, O. M. (2007). Quality of encryption measurement of bitmap images with RC6, MRC6, and Rijndael block cipher algorithms. International Journal of Network Security, 5(3), 241–251.
Fridrich, J. (1998). Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos, 8(6), 1259–1284.
Goldburg, B., Sridharan, S., & Dawson, E. (1993). Design and cryptanalysis of transform based analog speech scramblers. IEEE Journal of Selected Areas on Communication, 11, 735–743.
Hassan, E. S., Zhu, X., El-Khamy, S. E., Dessouky, M. I., El-Dolil, S. A., & Abd El-Samie, F. E. (2010). A chaotic interleaving scheme for the continuous phase modulation based single-carrier frequency-domain equalization system. Wireless Personal Communications. doi:10.1007/s11277-010-0047-z.
Koduru, S. C., & Chandrasekaran, V. (2008). Integrated confusion-diffusion mechanisms for chaos based image encryption. In IEEE 8th international conference on computer and information technology workshops.
Kuo, C. J. (1993). Novel image encryption technique and its application in progressive transmission. Journal of Electronic Imaging, 2(4), 345–351.
Mao, Y. B., Chen, G., & Lian, S. G. (2004). A novel fast image encryption scheme based on the 3D chaotic Baker map. International Journal of Bifurcation and Chaos in Applied Sciences and Engineering, 14(10), 3613–3624.
National Bureau of Standards (1977). Data encryption standard. Federal Information Processing Standards Publication no. 46, U.S. Government Printing Office, Washington.
Shannon, C. E. (1949). Communication theory of secrecy system. The Bell System Technical Journal, 28, 656–715.
Thongpon, T., & Sinchai, K. (2009). Accelerating asymmetric-key cryptography using parallel-key cryptographic algorithm (PCA). In 6th international conference on computer and information technology (Vol. 2, pp. 812–815).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mosa, E., Messiha, N.W., Zahran, O. et al. Encryption of speech signal with multiple secret keys in time and transform domains. Int J Speech Technol 13, 231–242 (2010). https://doi.org/10.1007/s10772-010-9081-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10772-010-9081-1