Abstract
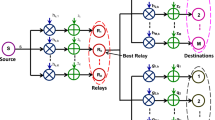
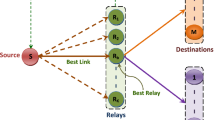
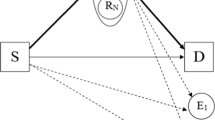
This paper exhibits the confidentiality performance study of a cooperative multicast network consisting of \({\mathcal {K}}\) asymmetric relays over Nakagami-m fading channels, where the communication links face uneven signal-to-noise ratios (SNRs). Although, conventional symmetric deployment of relays are convenient for analysis purposes but this assumption is not always effective in real cooperative network applications. So in this analysis, a cooperative multicast network is considered where a group of asymmetric relays cooperate in communication between a base station and multiple destinations under the nose of multiple eavesdroppers. Based on the given probability density function (PDF) of SNR for a point-to-point communication system, the analytical expressions of the PDF of SNRs are developed for multicast and eavesdroppers channels. Then, using these PDFs, the analytical representations for the probability of non-zero secrecy multicast capacity and the secure outage probability are derived for analyzing the performance of the proposed model. Finally, analytical results are verified with Monte-Carlo simulations.







Similar content being viewed by others
References
S. Chu, X. Wang, Y. Yang, Exploiting cooperative relay for high performance communications in MIMO ad hoc networks, IEEE Transactions on Computers, Vol. 62, No. 4, pp. 716–729, 2012.
J. Crawford, Y. Ko, Cooperative OFDM-IM relay networks with partial relay selection under imperfect CSI, IEEE Transactions on Vehicular Technology, Vol. 67, No. 10, pp. 9362–9369, 2018.
A. Vashistha, A. Sharma, V. A. Bohara, Outage analysis of a multiple antenna cognitive radio system with cooperative decode-and-forward relaying, IEEE Communications Letters, Vol. 4, No. 2, pp. 125–128, 2015.
M. I. Khalil, S. M. Berber, K. W. Sowerby, Bit error rate performance analysis in amplify-and-forward relay networks, Wireless Networks, Vol. 23, pp. 947–957, 2017.
D. Darsena, G. Gelli, F. Melito, F. Verde, Performance analysis of amplify-and-forward multiple-relay MIMO systems with ZF reception, IEEE Transactions on Vehicular Technology, Vol. 64, No. 7, pp. 3274–3280, 2014.
J. Chattha, M. Uppal, Layered multiplexed-coded relaying in wireless multicast using QAM transmissions, IEEE Communications Letters, Vol. 20, No. 4, pp. 760–763, 2016.
X. Wang, M. Tao, Y. Xu, Outage analysis of cooperative secrecy multicast transmission, IEEE Wireless Communications Letters, Vol. 3, No. 2, pp. 161–164, 2014.
D. K. Sarker, M. Z. I. Sarkar, M. S. Anower, Secure wireless multicasting with linear equalization, Physical Communication, Vol. 25, No. 1, pp. 201–213, 2017.
D. K. Sarker, M. Z. I. Sarkar, M. S. Anower, Secure wireless multicasting through AF-cooperative networks with best-relay selection over Generalized fading channels, Wireless Networks, Vol. 26, No. 3, pp. 1717–1730, 2020.
D. K. Sarker, M. Z. I. Sarkar, M. S. Anower, Enhancing Security in Multicasting with Partial Relay Selection over Composite Fading Channels, Wireless Personal Communications, Vol. 121, No. 1, pp. 1067–1084, 2021.
D. K. Sarker, M. Z. I. Sarkar, M. S. Anower, Secure outage performance analysis for multicasting with linear equalization, In Proceedings of the 18th International Conference on Computer and Information Technology (ICCIT). IEEE, pp. 99–104, 2015.
D. Wang, B. Bai, W. Chen, Z. Han, Energy efficient secure communication over decode-and-forward relay channels, IEEE Transactions on Communications, Vol. 63, No. 3, pp. 892–905, 2015.
H. Lei, Z. Dai, K.-H. Park, W. Lei, G. Pan, M.-S. Alouini, Secrecy outage analysis of mixed RF-FSO downlink SWIPT systems, IEEE Transactions on Communications, Vol. 66, No. 12, pp. 6384–6395, 2018.
Y. Zou, J. Zhu, X. Li, L. Hanzo, Relay selection for wireless communications against eavesdropping: A security-reliability tradeoff perspective, IEEE Networks, Vol. 30, No. 5, pp. 74–79, 2016.
Y. Liu, L. Wang, T. Duy, M. Elkashlan, T. Q. Duong, Relay selection for security enhancement in cognitive relay networks, IEEE Wireless Communications Letters, Vol. 4, No. 1, pp. 46–49, 2015.
H. Lei, H. Zhang, I. S. Ansari, Z. Ren, G. Pan, K. A. Qaraqe, M.-S. Alouini, On secrecy outage of relay selection in underlay cognitive radio networks over Nakagami-m fading channels, IEEE Transactions on Cognitive Communications and Networking, Vol. 3, No. 4, pp. 614–627, 2017.
K. Liu, X. Yuan, M. Tao, On the DoF region for the asymmetric MIMO two-way X relay channel, IEEE Transactions on Communications, Vol. 66, No. 1, pp. 119–132, 2018.
Y. Ye, Y. Li, Z. Wang, X. Chu, H. Zhang, Dynamic asymmetric power splitting scheme for SWIPT based two-way multiplicative AF relaying, IEEE Signal Processing Letters, Vol. 25, No. 7, pp. 1–5, 2018.
X. Ji, W.-P. Zhu, D. Massicotte, M. Ahmed-Ouameur, Energy efficient power allocation and relay location for asymmetric bi-directional relaying, In Proceedings of the IEEE Global Conference on Signal and Information Processing (GlobalSIP), pp. 1225–1229, 2015.
Z. Hasan, A. Jamalipour, V. K. Bhargava, Cooperative communication and relay selection under asymmetric information, In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), pp. 2373–2378, 2012.
A. Adinoyi, H. Yanikomeroglu, On the performance of cooperative wireless fixed relays in asymmetric channels, In Proceedings of the IEEE Global Communications Conference (GLOBECOM), pp. 1–5, 2006.
S. Vatedka, N. Kashyap, Nested lattice codes for secure bidirectional relaying with asymmetric channel gains, In Proceedings of the IEEE Information Theory Workshop (ITW), pp. 1–5, 2015.
K. Chopra, R. Bose, A. Joshia, Secure power trading in cooperative relay network with asymmetric cournot duopoly model, In Proceedings of the 12th Annual Symposium On Information Assurance (ASIA’17), pp. 1–6, 2017.
Y. Meziti, H. Wang, Achieving perfect secrecy capacity of an asymmetric bidirectional relay channel, In Proceedings of the IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), pp. 1–6, 2017.
B. Wang, J. Zhang, A. Madsen, On the capacity of MIMO relay channels, IEEE Transactions on Information Theory, Vol. 5, No. 11, pp. 29–43, 2005.
M. Z. I. Sarkar, T. Ratnarajah, Secure wireless multicasting through Nakagami-m fading MISO channel, In Proceedings of the IEEE 45th Asilomar Conf. on Signals, Systems and Computers (ASILOMAR), pp. 300–304, 2011.
I. S. Gradshteyn, I. M. Ryzhik, Table of Integrals, Series, and Products, 7th Edition, Academic, San Diego, CA, 2007.
A. Khisti, D. Zhang, Artificial-noise alignment for secure multicast using multiple antennas, IEEE Communications Letters, Vol. 17, No. 8, pp. 1568–1571, 2013.
C. E. Shannon, Communication theory of secrecy systems, Bell System Technical Journal, Vol. 28, pp. 656–715, 1949.
M. Z. I. Sarkar, T. Ratnarajah, Enhancing security in correlated channel with maximal ratio combining diversity, IEEE Transactions on Signal Processing, Vol. 60, No. 12, pp. 6745–6751, 2012.
C. -K. Toh, Ad Hoc Mobile Wireless Networks: Protocols and Systems, 2nd Edition, Pearson Education and Dorling Kindersley (India) Pvt. Ltd., Delhi, 2009.
L.M. Feeney, B. Ahlgren, A. Westerlund, Spontaneous Networking: An Application-Oriented Approach to Ad Hoc Networking. IEEE Communication Magazene, Vol. 39, No. 6, pp. 0–181, 2001.
C. Bettstetter, G. Resta, P. Santi, The node distribution of the random waypoint mobility model for wireless ad hoc networks. IEEE Transactions on Mobile Computing, Vol. 2, No. 3, pp. 257–269, 2003.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix I
The evaluation of the integral, \({\mathcal {I}}_{1}\) is given as follows:
where \({\mathcal {D}}_{1}=a_{2}!b_{2}^{-(a_{2}+1)}\), \({\mathcal {F}}_{1}=\sum _{\kappa _{1}=0}^{a_{2}}\frac{a_{2}!}{\kappa _{1}!b_{2}^{\eta _{2}}}\), \(\eta _{1}=a_{2}+\kappa _{1}\), \(\eta _{2}=a_{2}-\kappa _{1}+1\) and \(\theta _{1}=2b_{2}\). Performing integration using eqn. (8), we obtain
where \({\mathcal {D}}_{2}=\eta _{1}!\theta _{1}^{-(\eta _{1}+1)}\), \({\mathcal {F}}_{2}=\sum _{\kappa _{2}=0}^{a_{2}}\frac{a_{2}!}{\kappa _{2}!b_{2}^{\eta _{3}}}\), \({\mathcal {F}}_{3}=\sum _{\kappa _{3}=0}^{\eta _{1}}\frac{\eta _{1}!}{\kappa _{3}!\theta _{1}^{\eta _{4}}}\), \(\eta _{3}=a_{2}-\kappa _{2}+1\) and \(\eta _{4}=\eta _{1}-\kappa _{3}+1\).
Appendix II
The evaluation of the integral, \({\mathcal {I}}_{2}\) is given as follows:
Performing integration using the following identity of [27, eq. (3.351.2)],
we obtain
Substituting the value of \(\sigma\) and after some mathematical manipulation, we have
where
Rights and permissions
About this article
Cite this article
Sarker, D.K., Sarkar, M.Z.I., Anower, M.S. et al. Multicast Network Security with Asymmetric Cooperative Relaying. Int J Wireless Inf Networks 29, 303–313 (2022). https://doi.org/10.1007/s10776-022-00566-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10776-022-00566-7