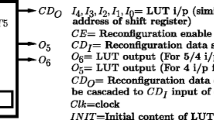
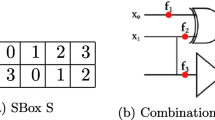
Abstract
Finite state machine (FSM) is a critical part in digital processing devices used in Internet of Things (IoT) applications as it controls complete functionality of the device. The synthesis tool implements deterministic FSM by adding extra don’t care states/transitions during optimization. This additional insertion makes the FSM vulnerable to setup-time violation based fault injection (STVFI) and hardware Trojan attacks. The existing techniques are inefficient to completely mitigate these vulnerabilities and exhibit significant design overhead. Therefore, this paper presents a novel lightweight secure machine design technique that completely mitigates the vulnerabilities with minimum overhead. The paper first proposes a new metric to identify all types of vulnerable transitions (VTs) followed by a trustworthy FSM design algorithm and efficient vulnerability mitigation architecture (EVMA). Though our EVMA completely alleviates the vulnerabilities to STVFI and Trojan attacks, it slightly increases the overhead due to additional multiplexers. Hence, we also propose new secure FSM design algorithm and two new lightweight vulnerability mitigation architectures (LVMA-I and LIVMA-II) that control the FFs using existing clear and/or preset pins instead of multiplexers. The experimental results on AES and RSA encryption modules show that the proposed technique detects 100% VTs. Further, ASIC and FPGA implementation of the proposed LIVMA-II using Cadence RTL and Xilinx Vivado presents on an average 40%, 59.6%, and 51.1% reduced area, power and delay respectively compared to the well-known technique. Due to negligible design overhead, our technique is best suitable for designing secure controller of portable IoT devices.










Similar content being viewed by others
References
Akdemir KD, Wang Z, Karpovsky M, Sunar B (2012) Design of cryptographic devices resilient to fault injection attacks using nonlinear robust codes. In: Fault analysis in cryptography, pp 171– 199. Springer
Baranov S, Levin I, Keren O, Karpovsky M (2009) Designing fault tolerant FSM by nano-PLA. In: Proceedings of 15th IEEE international on-line testing symposium (IOLTS), pp 229–234
Barenghi A, Breveglieri L, Koren I, Naccache D (2012) Fault injection attacks on cryptographic devices theory, practice, and countermeasures. Proc IEEE 100(11):3056–3076
Berg M (2004) Fault tolerant design techniques for asynchronous single event upsets within synchronous finite state machine architectures. In: 7th international military and aerospace programmable logic devices (MAPLD) conference. NASA
Bhunia S, Hsiao MS, Banga M, Narasimhan S (2014) Hardware trojan attacks: threat analysis and countermeasures. Proc IEEE 102(8):1229–1247
Biham E, Shamir A (1997) Differential fault analysis of secret key cryptosystems. Advances in Cryptology—CRYPTO’97, pp 513–525
Chakraborty RS, Bhunia Swarup (2011) Security against hardware trojan attacks using key-based design obfuscation. J Electron Test 27(6):767–785
Cocchi RP, Baukus JP, Chow LW, Wang BJ (2014) Circuit camouflage integration for hardware ip protection. In: Proceedings of 51st IEEE/ACM annual design automation conference (DAC), pp 1–5. ACM
Dofe J, Frey J, Qiaoyan YU (2016) Hardware security assurance in emerging iot applications. In: Proceedings of IEEE international symposium on circuits and systems (ISCAS), pp 2050–2053. IEEE
Dunbar Carson, Gang Q u (2014) Designing trusted embedded systems from finite state machines. ACM Trans Embed Comput Syst 13(5s):153–172
Fan J, Guo XU, Mulder ED, Schaumont P, Preneel B, Verbauwhede I (2010) State-of-the-art of secure ECC implementations: a survey on known side-channel attacks and countermeasures. In: Proceedings of IEEE international symposium on hardware-oriented security and trust (HOST), pp 76–87. IEEE
Farahmandi F, Mishra P (2017) FSM anomaly detection using formal analysis. In: Proceedings of 35th IEEE international conference on computer design (ICCD), pp 313–320
Karaklajić D, Schmidt J-M, Verbauwhede I (2013) Hardware designer’s guide to fault attacks. IEEE Trans Very Large Scale Integr VLSI Syst 21(12):2295–2306
Karpovsky M, Taubin A (2004) New class of nonlinear systematic error detecting codes. IEEE Trans Inf Theory 50(8):1818–1819
Krasniewski A (2008) Concurrent error detection for finite state machines implemented with embedded memory blocks of SRAM-based fpgas. Microprocess Microsyst 32(5-6):303–312
Li M, Lai L, Chandra V, Pan DZ (2017) Cross-level monte carlo framework for system vulnerability evaluation against fault attack. In: Proceedings of 54th annual design automation conference, pp 17–22. ACM
Nahiyan A, Farahmandi F, Mishra P (2018), Domenic Forte, and Mark Tehranipoor. Security-aware fsm design flow for identifying and mitigating vulnerabilities to fault attacks. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems
Nahiyan A, Xiao K, Yang K, Jin Y, Forte D, Tehranipoor M (2016) AVFSM: a framework for identifying and mitigating vulnerabilities in FSMs. In: Proc. 53rd ACM/IEEE design automation conference (DAC), pp 1–6. IEEE
Niranjan Shailesh, Frenzel James F (1996) A comparison of fault-tolerant state machine architectures for space-borne electronics. IEEE Trans Reliab 45(1):109–113
Rahman F, Farmani M, Tehranipoor M, Jin Y (2017) Hardware-assisted cybersecurity for iot devices. In: Proceedings of 18th international workshop on microprocessor and SOC test and verification (MTV), pp 51–56. IEEE
Rathor VS, Garg B, Sharma GK (2017) New light weight threshold voltage defined camouflaged gates for trustworthy designs. J Electron Test 33(5):657–668
Rathor VS, Garg B, Sharma GK (2018) An energy-efficient trusted fsm design technique to thwart fault injection and trojan attacks. In: Proceedings of 31st IEEE international conference on VLSI design (VLSID), pp 73–78. IEEE
Rathor VS, Garg B, Sharma GK (2018) A novel low complexity logic encryption technique for design-for-trust. IEEE Transactions on Emerging Topics in Computing
Rostami M, Koushanfar F, Karri R (2014) A primer on hardware security Models, methods, and metrics. Proc IEEE 102(8):1283–1295
Salmani H, Tehranipoor M (2013) Analyzing circuit vulnerability to hardware trojan insertion at the behavioral level. In: Proceedings IEEE international symposium on defect and fault tolerance in VLSI and nanotechnology systems (DFT), pp 190–195
Sunar B, Gaubatz G, Savas E (2008) Sequential circuit design for embedded cryptographic applications resilient to adversarial faults. IEEE Trans Comput 57(1):126–138
Wang Z, Karpovsky M (2010) Robust FSMs for cryptographic devices resilient to strong fault injection attacks. In: Proceedings of 16th IEEE international on-line testing symposium (IOLTS), pp 240–245. IEEE
Wang Z, Karpovsky M, Sunar B (2009) Multilinear codes for robust error detection. In: Proc. 15th IEEE international on-line testing symposium (IOLTS), pp 164–169. IEEE
Xiao K, Forte D, Jin Y, Karri R, Bhunia S, Tehranipoor M (2016) Hardware trojans: lessons learned after one decade of research. ACM Transactions on Design Automation of Electronic Systems (TODAES) 22(1):6
Yuce B, Ghalaty NF, Schaumont P (2015) TVVF Estimating the vulnerability of hardware cryptosystems against timing violation attacks. In: Proceedings of IEEE international symposium on hardware oriented security and trust (HOST), pp 72–77
Author information
Authors and Affiliations
Corresponding author
Additional information
Responsible Editor: C. A. Papachristou
Rights and permissions
About this article
Cite this article
Rathor, V.S., Garg, B. & Sharma, G.K. New Lightweight Architectures for Secure FSM Design to Thwart Fault Injection and Trojan Attacks. J Electron Test 34, 697–708 (2018). https://doi.org/10.1007/s10836-018-5762-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10836-018-5762-5