Abstract
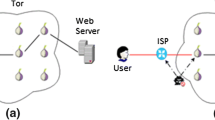
The website fingerprinting attack is one of the most important traffic analysis attacks that is able to identify a visited website in an anonymizing network such as Tor. It is shown that the existing defense methods against website fingerprinting attacks are inappropriate. In addition, they use large bandwidth and time overhead. In this study, we show that the autocorrelation property is the most important success factor of the website fingerprinting attack. We offer a new effective defense model to resolve this security vulnerability of the Tor anonymity network. The proposed defense model prevents information leakage from the passing traffic. In this regard, a novel mechanism is developed to make the traffic analysis a hard task. This mechanism is based on decreasing the entropy of instances by minimizing the autocorrelation property of them. By applying the proposed defense model, the accuracy of the most effective website fingerprinting attack reduces from 98% to the lowest success rate of the website fingerprinting attack, while the maximum bandwidth overhead of the network traffic remains on about 8%. Recall that the current best defense mechanisms reduce the accuracy of the attack to 23% with a minimum bandwidth overhead of more than 44%. Hence, the proposed defense model significantly reduces the accuracy of the website fingerprinting attack, while the bandwidth overhead increases very slightly (i.e., up to 8%).








Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Notes
k-Nearest Neighbors
Fast Fourier Transformation
Direct Target Sampling
Traffic Morphing
Buffered Fixed-Length Obfuscator
Congestion Sensitive BUFLO
Adaptive Padding
Distance Matrix represents a matrix that its rows correspond to instances of different websites and columns correspond to websites, while cell i,j indicate the similarity distance between instance i and website j.
Maximum transmission unit
This function permutes the components of input vector in a random manner.
The source code of known WF-attacks are provided at URL:“https://www.cse.ust.hk/%7Etaow/wf/attacks/”.
References
Cai, X., Zhang, X.C., Joshi, B., Johnson, R. (2012). Touching from a distance: Website fingerprinting attacks and defenses. In: Proceedings of the 2012 ACM conference on Computer and communications security, pp 605–616.
Cai, X., Nithyanand, R., Johnson, R. (2014). Cs-buflo: A congestion sensitive website fingerprinting defense. In: Proceedings of the 13th workshop on privacy in the electronic society, pp. 121–130.
Cai, X., Nithyanand, R., Wang, T., Johnson, R., Goldberg, I. (2014). A systematic approach to developing and evaluating website fingerprinting defenses. In: Proceedings of the 2014 ACM SIGSAC conference on computer and communications security, pp. 227–238.
Cherubin, G., Hayes, J., Juarez, M. (2017). Website fingerprinting defenses at the application layer. Proceedings on Privacy Enhancing Technologies, 2017, 186–203.
Dingledine, R., Mathewson, N., Syverson, P. (2004). Tor: The second-generation onion router, DTIC Document.
Dingledine, R., Mathewson, N., Syverson, P. (2008). Tor: anonymity online, ed,.
Dyer, K.P., Coull, S.E., Ristenpart, T., Shrimpton, T. (2012). Peek-a-boo, i still see you: Why efficient traffic analysis countermeasures fail. In: 2012 IEEE symposium on security and privacy, pp. 332–346.
Golomb, S.W. (1967). Shift register sequences. Aegean Park Press.
Gu, X., Yang, M., Luo, J. (2015). A novel Website Fingerprinting attack against multi-tab browsing behavior. In: 2015 IEEE 19th international conference on computer supported cooperative work in design (CSCWD), pp. 234–239.
Hayes, J., & Danezis, G. (2016). k-fingerprinting: A robust scalable website fingerprinting technique. In: USENIX security symposium, pp 1187–1203.
He, G., Yang, M., Gu, X., Luo, J., Ma, Y. (2014). A novel active website fingerprinting attack against Tor anonymous system. In: Proceedings of the 2014 IEEE 18th international conference on computer supported cooperative work in design (CSCWD), pp. 112–117.
Herrmann, D., Wendolsky, R., Federrath, H. (2009). Website fingerprinting: attacking popular privacy enhancing technologies with the multinomial naïve-bayes classifier. In: Proceedings of the 2009 ACM workshop on Cloud computing security, pp. 31–42.
Hintz, A. (2002). Fingerprinting websites using traffic analysis. In: International workshop on privacy enhancing technologies, pp. 171–178.
Jahani, H., & Jalili, S. (2016). A novel passive website fingerprinting attack on tor using fast fourier transform. Computer Communications, 96, 43–51.
Juarez, M., Afroz, S., Acar, G., Diaz, C., Greenstadt, R. (2014). A critical evaluation of website fingerprinting attacks. In: Proceedings of the 2014 ACM SIGSAC conference on computer and communications security, pp 263–274.
Juarez, M., Imani, M., Diaz, C., Perry, M., Wright, M. (2016). Toward an efficient website fingerprinting defense for Tor. In: Lecture notes in computer science, pp. 27–46.
Luo, X., Zhou, P., Chan, E.W., Lee, W., Chang, R.K., Perdisci, R. (2011). HTTPOS: Sealing information leaks with browser-side obfuscation of encrypted flows. In: NDSS.
Murdoch, S.J., & Zieliski, P. (2007). Sampled traffic analysis by internet-exchange-level adversaries. In: International workshop on privacy enhancing technologies, 167–183.
Panchenko, A., Lanze, F., Pennekamp, J., Engel, T., Zinnen, A., Henze, M., et al. (2016). Website fingerprinting at internet scale. In: NDSS.
Panchenko, A., Niessen, L., Zinnen, A., Engel, T. (2011). Website fingerprinting in onion routing based anonymization networks. In: Proceedings of the 10th annual ACM workshop on Privacy in the electronic society, pp. 103–114.
Perry, M. (2011). Experimental defense for website traffic fingerprinting, Tor project Blog.” https://blog.torproject.org/blog/experimental-defense-website-traffic-fingerprinting.
Shi, Y., & Matsuura, K. (2009). Fingerprinting attack on the tor anonymity system. In: Information and communications security, ed: Springer, pp. 425–438.
Sun, Q., Simon, D.R., Wang, Y.-M., Russell, W., Padmanabhan, V.N., Qiu, L. (2002). Statistical identification of encrypted web browsing traffic. In: Proceedings IEEE symposium, security and privacy, pp. 19-30.
Wang, T., Cai, X., Nithyanand, R., Johnson, R., Goldberg, I. (2014). Effective attacks and provable defenses for website fingerprinting. In: 23rd USENIX Security Symposium (USENIX Security 14), pp. 143–157.
Wang, T., & Goldberg, I. (2013). Improved website fingerprinting on tor. In: Proceedings of the 12th ACM workshop on Workshop on privacy in the electronic society, pp. 201–212.
Wang, T., & Goldberg, I. (2014). Comparing website fingerprinting attacks and defenses, Technical Report 2013-30, CACR, 2013. http://cacr.uwaterloo.ca/techreports/2013/cacr2013-30.pdf.
Wang, T., & Goldberg, I. (2015). Walkie-talkie: An effective and efficient defense against website fingerprinting.
Wright, C.V., Coull, S.E., Monrose, F. (2009). Traffic morphing: An efficient defense against statistical traffic analysis. In: NDSS.
Zhu, Y., Fu, X., Graham, B., Bettati, R., Zhao, W. (2005). On flow correlation attacks and countermeasures in mix networks. In: Privacy enhancing technologies, pp. 207–225.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jahani, H., Jalili, S. Effective defense against fingerprinting attack based on autocorrelation property minimization approach. J Intell Inf Syst 54, 341–362 (2020). https://doi.org/10.1007/s10844-019-00553-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10844-019-00553-0