Abstract
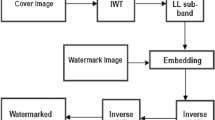
Due to the recent explosion of ‘identity theft’ cases, the safeguarding of private data has been the focus of many scientific efforts. Medical data contain a number of sensitive attributes, whose access the rightful owner would ideally like to disclose only to authorized personnel. One way of providing limited access to sensitive data is through means of encryption. In this work we follow a different path, by proposing the fusion of the sensitive metadata within the medical data. Our work is focused on medical time-series signals and in particular on Electrocardiograms (ECG). We present techniques that allow the embedding and retrieval of sensitive numerical data, such as the patient’s social security number or birth date, within the medical signal. The proposed technique not only allows the effective hiding of the sensitive metadata within the signal itself, but it additionally provides a way of authenticating the data ownership or providing assurances about the origin of the data. Our methodology builds upon watermarking notions, and presents the following desirable characteristics: (a) it does not distort important ECG characteristics, which are essential for proper medical diagnosis, (b) it allows not only the embedding but also the efficient retrieval of the embedded data, (c) it provides resilience and fault tolerance by employing multistage watermarks (both robust and fragile). Our experiments on real ECG data indicate the viability of the proposed scheme.














Similar content being viewed by others
References
da Silva, P. P., McGuinness, D. L., & McCool, R. (2003). Knowledge provenance infrastructure. Data Eng. Bull. 26(4), 26–32.
Cox, I. J., Kilian, J., Leighton, F. T., & Shamoon, T. (1997). Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 6(12), 1673–1687.
Mihcak, M. K., Venkatesan, R., & Liu, T. (2005). Watermarking via optimization algorithms for quantizing randomized semi-global image statistics. ACM J. Multimedia Syst. 11(2), 185–200.
Kong, X. (2001). Watermarking medical signals for telemedicine. IEEE Trans. Inf. Technol. Biomed. 5(3), 195–201.
Engin, M., Cidam, O., & Engin, E. Z. (2005). Wavelet transformation based watermarking technique for human electrocardiogram. J. Med. Syst. 29(6), 589–594.
Mihcak, M. K., Venkatesan, R., & Kesal, M. (2002). Cryptanalysis of discrete-sequence spread spectrum watermarks. In Proc. of the 5th Int. Workshop Inform. Hiding.
Sion, R., Atallah, M. J., & Prabhakar, S. (2006). Rights protection for discrete numeric streams. IEEE Trans. Knowl. Data Eng. 18(5), 699–714.
Agrawal, R., & Kiernan, J. (2002). Watermarking relational databases. In Proc. of VLDB, (pp. 155–166).
Sion, R., Atallah, M., & Prabhakar, S. (2003). Rights protection for relational data. In Proc. of SIGMOD, (pp. 98–109).
Bertino, E., Ooi, B.-C., Yang, Y., & Deng, R. H. (2005). Privacy and ownership preserving of outsourced medical data. In Proc. of ICDE, (pp. 521–532).
Kargupta, H., Datta, S., Wang, Q., & Sivakumar, K. (2003) On the privacy preserving properties of random data perturbation techniques. In Proc. of ICDM, (pp. 99–106).
Liu, L., Kantarcioglu, M., & Thuraisingham, B. (2006). The applicability of the perturbation model-based privacy preserving data mining for real-world data. In Intl Workshop on Privacy Aspects of Data-Mining.
Oliveira, S., & Zaiane, O. (2003). Privacy preserving clustering by data transformation. In Proc. of SBBD, (pp. 304–318).
Vaidya, J., & Clifton, C. (2003). Privacy-preserving K-means clustering over vertically partitioned data. In Proc. of SIGKDD, (pp. 206–215).
Vaidya, J., & Clifton, C. (2004). Privacy preserving naive bayes classifier for vertically partitioned data. In Proc. of SDM.
Oppenheim, A. V., Willsky, A. S., & Nawab, S. H. (1997). Signals and systems, 2nd Edition. Englewood Cliffs: Prentice Hall.
Vincent Poor, H. (1994). An introduction to signal detection and estimation (2nd ed.). New York: Springer.
Fridrich, J. (1998). Image watermarking for tamper detection. In Proc. ICIP, (pp. 404–408).
Wong, P. (1998). A public key watermark for image verification and authentication. In Proc. of Int. Conf. on Image Processing, (pp. 455–459).
Wolfgang, R. B., & Delp, E. J. (1999). Fragile watermarking using the VW2D watermark. In Proc. SPIE/IS T Inter. Conf. Security and Watermarking of Multimedia Contents, (pp. 204–213).
Moulin, P., Mihcak, M. E., & Lin, G.-I. (2000). An information-theoretic model for image watermarking and data hiding. In IEEE Int. Conf. on Image Processing.
Kozat, S. S., Venkatesan, R., & Mihcak, M. K. (2004). Robust hashing via matrix-invariances. In Proc. of IEEE Conf. on Image Processing.
MIT-BIH Arrhythmia Database. http://www.physionet.org/physiobank/database/mitdb/.
Petrucci, E., Balian, V., Filippini, G., & Mainardi, L. T. (2005). Atrial fibrillation detection algorithms for very long term ECG monitoring. In Computers in Cardiology.
Vlachos, M., Yu, P. S., & Castelli, V. (2005). On Periodicity detection and structural periodic Similarity. In Proc. of SDM.
Chiranjivi, G., Madasu, V. K., Hanmandlu, M., & Lovell, B. C. (2005). Arrhythmia detection in human electrocardiogram. In APRS Workshop on Digital Image Computing, (pp. 189–192).
Papoulis, A. (1977). Signal analysis. New York: McGraw-Hill.
Author information
Authors and Affiliations
Corresponding author
Additional information
Claudio Lucchese’s work partially supported by the IST FP6 project SAPIR (Contract no. 45128)
Rights and permissions
About this article
Cite this article
Kozat, S.S., Vlachos, M., Lucchese, C. et al. Embedding and Retrieving Private Metadata in Electrocardiograms. J Med Syst 33, 241–259 (2009). https://doi.org/10.1007/s10916-008-9185-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10916-008-9185-1