Abstract
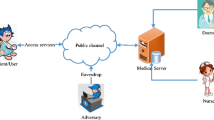
Connected health care has several applications including telecare medicine information system, personally controlled health records system, and patient monitoring. In such applications, user authentication can ensure the legality of patients. In user authentication for such applications, only the legal user/patient himself/herself is allowed to access the remote server, and no one can trace him/her according to transmitted data. Chang et al. proposed a uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care (Chang et al., J Med Syst 37:9902, 2013). Their scheme uses the user’s personal biometrics along with his/her password with the help of the smart card. The user’s biometrics is verified using BioHashing. Their scheme is efficient due to usage of one-way hash function and exclusive-or (XOR) operations. In this paper, we show that though their scheme is very efficient, their scheme has several security weaknesses such as (1) it has design flaws in login and authentication phases, (2) it has design flaws in password change phase, (3) it fails to protect privileged insider attack, (4) it fails to protect the man-in-the middle attack, and (5) it fails to provide proper authentication. In order to remedy these security weaknesses in Chang et al.’s scheme, we propose an improvement of their scheme while retaining the original merit of their scheme. We show that our scheme is efficient as compared to Chang et al.’s scheme. Through the security analysis, we show that our scheme is secure against possible attacks. Further, we simulate our scheme for the formal security verification using the widely-accepted AVISPA (Automated Validation of Internet Security Protocols and Applications) tool to ensure that our scheme is secure against passive and active attacks. In addition, after successful authentication between the user and the server, they establish a secret session key shared between them for future secure communication.






Similar content being viewed by others
References
Aumasson, J. P., Henzen, L., Meier, W., and Plasencia, M. N., Quark: A lightweight hash. In: Workshop on Cryptographic Hardware and Embedded Systems (CHES 2010), LNCS. Vol. 6225, pp. 1–15, 2010.
AVISPA, Automated Validation of Internet Security Protocols and Applications. http://www.avispa-project.org/. Accessed on January 2013.
AVISPA: AVISPA Web Tool. http://www.avispa-project.org/web-interface/expert.php/. Accessed on January 2013.
Basin, D., Modersheim, S., and Vigano, L., OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 4(3):181–208, 2005.
Chang, Y.-F., Yu, S.-H., and Shiao, D.-R., An uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37:9902, 2013.
Das, A.K., A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Netw. Sci., 2012. doi:10.1007/s13119-012-0009-8.
Das, A.K., Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Inf. Secur. 5(3):145–151, 2011.
Das, A.K., A random key establishment scheme for multi-phase deployment in large-scale distributed sensor networks. Int. J. Inf. Secur. 11(3):189–211, 2012.
Das, A.K., Massand, A., and Patil, S., A novel proxy signature scheme based on user hierarchical access control policy. J. King Saud Univ.—Comput. Inform. Sci., 2013. doi:10.1016/j.jksuci.2012.12.001.
Das, M.L., Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 8(3):1086–1090, 2009.
Dolev, D., and Yao, A., On the security of public key protocols. IEEE Trans. Inf. Theory 29(2):198–208, 1983.
Hwang, M.S., and Liu, C.-Y., Authenticated encryption schemes: Current status and key issues. Int. J. Netw. Secur. 1(2):61–73, 2005.
Jina, A.T.B., Linga, D.N.C., and Goh, A., Biohashing: Two factor authentication featuring fingerprint data and tokenised random number. Pattern Recogn. 37(11):2245–2255, 2004.
Khan, M.K., Zhang, J., and Wang, X., Chaotic hash-based fingerprint biometric remote user authentication scheme on mobile devices. Chaotic Solitons Fractals 35(3):519–524, 2008.
Kocher, P., Jaffe, J., and Jun, B., Differential power analysis. In: Proceedings of Advances in Cryptology—CRYPTO’99, LNCS. Vol. 1666, pp 388–397, 1999.
Lee, N.-Y., and Chiu, Y.-C., Improved remote authentication scheme with smart card. Comput. Stand. Interfaces 27(2):177–180, 2005.
Li, C.-T., and Hwang, M.-S., An efficient biometric-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 33:1–5, 2010.
Li, X., Niu, J.-W., Ma, J., Wang, W.-D., and Liu, C.-L., Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 34:73–79, 2011.
Lumini, A., and Nanni, L., An improved BioHashing for human authentication. Pattern Recogn. 40(3):1057–1065, 2007.
Manuel, S., Classification generation of disturbance vectors for collision attacks against SHA-1. Des. Codes Crypt. 59(1–3):247–263, 2011.
Messerges, T.S., Dabbish, E.A., and Sloan, R.H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Stallings, W., Cryptography and network security: Principles and practices. Prentice Hall, 3rd edition, 2003.
Secure Hash Standard, FIPS PUB 180-1, National Institute of Standards and Technology (NIST), U.S. Department of Commerce, 1995.
Acknowledgments
The authors would like to acknowledge the helpful suggestions of the anonymous reviewers, which have improved the content and the presentation of this paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Das, A.K., Goswami, A. A Secure and Efficient Uniqueness-and-Anonymity-Preserving Remote User Authentication Scheme for Connected Health Care. J Med Syst 37, 9948 (2013). https://doi.org/10.1007/s10916-013-9948-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9948-1