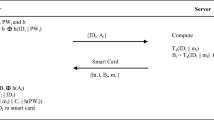
Abstract
Secure user authentication schemes in many e-Healthcare applications try to prevent unauthorized users from intruding the e-Healthcare systems and a remote user and a medical server can establish session keys for securing the subsequent communications. However, many schemes does not mask the users’ identity information while constructing a login session between two or more parties, even though personal privacy of users is a significant topic for e-Healthcare systems. In order to preserve personal privacy of users, dynamic identity based authentication schemes are hiding user’s real identity during the process of network communications and only the medical server knows login user’s identity. In addition, most of the existing dynamic identity based authentication schemes ignore the inputs verification during login condition and this flaw may subject to inefficiency in the case of incorrect inputs in the login phase. Regarding the use of secure authentication mechanisms for e-Healthcare systems, this paper presents a new dynamic identity and chaotic maps based authentication scheme and a secure data protection approach is employed in every session to prevent illegal intrusions. The proposed scheme can not only quickly detect incorrect inputs during the phases of login and password change but also can invalidate the future use of a lost/stolen smart card. Compared the functionality and efficiency with other authentication schemes recently, the proposed scheme satisfies desirable security attributes and maintains acceptable efficiency in terms of the computational overheads for e-Healthcare systems.


Similar content being viewed by others
References
Bergamo, P., Arco, P., Santis, A., and Kocarev, L., Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst. I 52(7):1382–1393, 2005.
Chaturvedi, A., Mishra, D., and Mukhopadhyay, S.: An enhanced dynamic ID-based authentication scheme for telecare medical information systems, Journal of King Saud University - Computer and Information Sciences. doi:10.1016/j.jksuci.2014.12.007 (2015)
Farash, M. S., and Attari, M. A., Cryptanalysis and improvement of a chaotic map-based key agreement protocol using Chebyshev sequence membership testing. Nonlinear Dyn. 76(2):1203–1213, 2014.
Farash, M. S., Turkanović, M., Kumari, S., and Hölbl, M., An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment. Ad Hoc Netw. 36(1):152–176, 2016.
Hao, X., Wang, J., Yang, Q., Yan, X., and Li, P., A chaotic map-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(2):9919, 2013.
Han, S., Security of a key agreement protocol based on chaotic maps. Chaos, Solitons Fractals 38(3):764–768, 2008.
He, D., and Zeadally, S., Authentication protocol for ambient assisted living system. IEEE Commun. Mag. 35(1):71–77, 2015.
He, D., Kumar, N., and Chen, J., Robust anonymous authentication protocol for healthcare applications using wireless medical sensor networks. Multimedia Systems 21(1):49–60, 2015.
He, D., Zeadally, S., Kumar, N., and Lee, J. H.: Anonymous authentication for wireless body area networks with provable security, IEEE Systems Journal. doi:10.1109/JSYST.2016.2544805 10.1109/JSYST.2016.2544805 (2016)
He, D., Kumar, N., Shen, H., and Lee, J. H.: One-to-many authentication for access control in mobile pay-TV systems, Science China Information Sciences. doi:10.1007/s11432-015-5469-5 (2016)
Huang, B., Khan, M. K., Wu, L., Muhaya, F. T. B., and He, D., An efficient remote user authentication with key agreement scheme using elliptic curve cryptography. Wirel. Pers. Commun. 85(1):225–240, 2015.
Jiang, Q., Ma, J., Li, G., and Li, X., Improvement of robust smart-card-based password authentication scheme. Int. J. Commun. Syst. 28(2):383–393, 2015.
Jiang, Q., Ma, J., Lu, X., and Tian, Y., An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 8(6):1070–1081, 2015.
Jiang, Q., Wei, F., Fu, S., Ma, J., Li, G., and Alelaiwi, A., Robust extended chaotic maps-based three-factor authentication scheme preserving biometric template privacy. Nonlinear Dyn. 83(4):2085–2101, 2016.
Jiang, Q., Ma, J., and Wei, F.: On the security of a privacy-aware authentication scheme for distributed mobile cloud computing services IEEE Systems Journal. doi:10.1109/JSYST.2016.2574719 (2016)
Kalra, S., and Sood, S. K., Secure authentication scheme for IoT and cloud servers. Pervasive Mob. Comput. 24:210–223, 2015.
Lee, C. C., Li, C. T., Chiu, S. T., Lai, Y. M., A new three-party authenticated key agreement scheme based on chaotic maps without password table. Nonlinear Dyn. 79(4):2485–2495, 2015.
Li, C. T., and Hwang, M. S., An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 33(1):1–5, 2010.
Li, C. T., and Lee, C. C., A novel user authentication and privacy preserving scheme with smart cards for wireless communications. Math. Comput. Model. 55(1-2):35–44, 2012.
Li, C. T., A new password authentication and user anonymity scheme Based on elliptic curve cryptography and smart card. IET Inf. Secur. 7(1):3–10, 2013.
Li, C. T., Lee, C. C., and Weng, C. Y., An extended chaotic maps based user authentication and privacy preserving scheme against DoS attacks in pervasive and ubiquitous computing environments. Nonlinear Dyn. 74(4): 1133–1143, 2013.
Li, C. T., Lee, C. C., Weng, C. Y., and Fan, C. I., A secure dynamic identity based authentication protocol with smart cards for multi-server architecture. J. Inf. Sci. Eng. 31(6):1975–1992, 2015.
Li, C. T., A secure chaotic maps based privacy-protection scheme for multi-server environments. Secur. Commun. Netw. 9(14):2276–2290, 2016.
Liu, C. H., and Chung, Y. F.: Secure user authentication scheme for wireless healthcare sensor networks, Computers & Electrical Engineering, article in press (2016)
Maitra, T., Amin, R., Giri, D., and Srivastava, P. D., An efficient and robust user authentication scheme for hierarchical wireless sensor networks without tamper-proof smart card. Int. J. Netw. Secur. 18(3):553–564, 2016.
Mason, J. C., and Handscomb, D. C.: Chebyshev Polynomials, Chapman & Hall CRC press (2003)
Messerges, T. S., Dabbish, E. A., and Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
RFC 2104 − HMAC: Keyed-hashing for message authentication. http://www.ietf.org/rfc/rfc2104.txt
Wang, X. Y., and Luan, D. P., A secure key agreement protocol based on chaotic maps. Chin. Phys. B 22 (11):110503, 2013.
Wang, Y., Zhong, H., Xu, Y., and Cui, J., ECPB: Efficient conditional privacy-preserving authentication scheme supporting batch verification for VANETs. Int. J. Netw. Secur. 18(2):374–382 , 2016.
Yeh, K. H., An anonymous and lightweight authentication scheme for mobile devices. Inf. Technol. Control 44(2):206–215, 2015.
Zeng, S., Huang, Y., and Liu, X., Privacy-preserving communication for VANETs with conditionally anonymous ring signature. Int. J. Netw. Secur. 17(2):135–141, 2015.
Zhang, L., Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons Fractals 37(3):669–674, 2008.
Acknowledgments
The authors would like to thank the anonymous reviewers and the Editor for their constructive and generous feedback on this paper. In addition, this research was partially supported and funded by the Ministry of Science and Technology, Taiwan, R.O.C., under contract no.: MOST 105-2221-E-165-005 and MOST 105- 2221-E-030-012.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Li, CT., Lee, CC., Weng, CY. et al. A Secure Dynamic Identity and Chaotic Maps Based User Authentication and Key Agreement Scheme for e-Healthcare Systems. J Med Syst 40, 233 (2016). https://doi.org/10.1007/s10916-016-0586-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0586-2