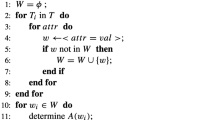Abstract
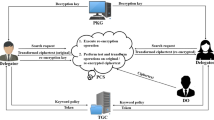
The migration of e-health systems to the cloud computing brings huge benefits, as same as some security risks. Searchable Encryption(SE) is a cryptography encryption scheme that can protect the confidentiality of data and utilize the encrypted data at the same time. The SE scheme proposed by Cash et al. in Crypto2013 and its follow-up work in CCS2013 are most practical SE Scheme that support Boolean queries at present. In their scheme, the data user has to generate the search tokens by the counter number one by one and interact with server repeatedly, until he meets the correct one, or goes through plenty of tokens to illustrate that there is no search result. In this paper, we make an improvement to their scheme. We allow server to send back some information and help the user to generate exact search token in the search phase. In our scheme, there are only two round interaction between server and user, and the search token has \((n-1) \times |I_{w_{1}}|\) elements, where n is the keywords number in query expression, and \(|I_{w_{1}}|\) is the minimum documents number that contains one of keyword in query expression, and the computation cost of server is \((n-1) \times |I_{w_{1}}|\) modular exponentiation operation.

Similar content being viewed by others
Notes
1 handle arbitrary Boolean query expressions is decribed in [6]
2 Acturally, let us view the elements in the inverted index as a pair of keyword and document identifier, by exchange the order of the pair, we can get a new pair of document identifier and keyword, then the new pair is just the element in the forward index.
References
Agrawal, R., Kiernan, J., Srikant, R., and Xu, Y., Order preserving encryption for numeric data. In: Proceedings of the ACM SIGMOD international conference on Management of data, p. 2004 (2004)
Ballard, L., Kamara, S., and Monrose, F., Achieving efficient conjunctive keyword searches over encrypted data. In: International Conference on Information and Communications Security, pages 414–426. Springer (2005)
Boneh, D., Di Crescenzo, G., Ostrovsky, R., and Persiano, G., Public key encryption with keyword search. In: International Conference on the Theory and Applications of Cryptographic Techniques, pages 506–522. Springer (2004)
Bösch, C., Hartel, P., Jonker, W., and Peter, A., A survey of provably secure searchable encryption. ACM Comput. Surv. (CSUR) 47(2):18, 2015.
Byun, J.W., Lee, D.H., and Lim, J., Efficient conjunctive keyword search on encrypted data storage system. In: European Public Key Infrastructure Workshop, pages 184–196. Springer (2006)
Cash, D., Jarecki, S., Jutla, C., Krawczyk, H., Roşu, M. -C., and Steiner, M., Highly-scalable searchable symmetric encryption with support for boolean queries. In: Advances in Cryptology–CRYPTO 2013, pages 353–373. Springer (2013)
Chor, B., Kushilevitz, E., Goldreich, O., and Sudan, M., Private information retrieval. J. the ACM (JACM) 45(6):965–981, 1998.
Curtmola, R., Garay, J., Kamara, S., and Ostrovsky, R., Searchable symmetric encryption: Improved definitions and efficient constructions (2006)
Fu, Z., Ren, K., Shu, J., Sun, X., and Huang, F., Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans. Parallel Distrib. Syst. 27(9):2546–2559, Sept 2016.
Gentry, C., A fully homomorphic encryption scheme. Phd thesis Stanford University (2009)
Golle, P., Staddon, J., and Waters, B., Secure conjunctive keyword search over encrypted data. In: International Conference on Applied Cryptography and Network Security, pages 31–45. Springer (2004)
He, D., Kumar, N., Wang, H., Wang, L., Choo, K. K. R., and Vinel, A., A provably-secure cross-domain handshake scheme with symptoms-matching for mobile healthcare social network IEEE Transactions on Dependable and Secure Computing, PP(99), 1–1 2016. doi:10.1109/TDSC.2016.2596286.
He, D., Zeadally, S., Kumar, N., and Lee, J. H., Anonymous authentication for wireless body area networks with provable security IEEE Systems Journal, PP(99), 1–12, 2016. doi:10.1109/JSYST.2016.2544805.
He, D., Zeadally, S., and Wu, L., Certificateless public auditing scheme for cloud-assisted wireless body area networks IEEE Systems Journal, PP(99), 1–10, 2015. doi:10.1109/JSYST.2015.2428620.
Jarecki, S., Jutla, C., Krawczyk, H., Rosu, M., and Steiner, M., Outsourced symmetric private information retrieval. In: Proceedings of the ACM SIGSAC conference on Computer & communications security, pages 875–888, p. 2013 (2013)
Liu, Z., Huang, X., Hu, Z., Khan, M.K., Seo, H., and Zhou, L., On emerging family of elliptic curves to secure internet of things: Ecc comes of age. IEEE Transactions on Dependable and Secure Computing, 99 (2016)
Liu, Z., Seo, H., Großschäl, J., and Kim, H., Efficient implementation of NIST-compliant elliptic curve cryptography for 8-bit avr-based sensor nodes. IEEE Trans. Inf. Forensics Secur. 11(7):1385–1397, 2016.
Naveed, M., Kamara, S., and Wright, C. V., Inference attacks on property-preserving encrypted database. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, pages 644–655 ACM (2015)
Ostrovsky, R., Efficient computation on oblivious rams. In: Proceedings of the twenty-second annual ACM symposium on Theory of computing, pages 514–523 ACM (1990)
Popa, R. A., Redfield, C., Zeldovich, N., and Balakrishnan, H., Cryptdb: protecting confidentiality with encrypted query processing. In: Proceedings of the Twenty-Third ACM Symposium on Operating Systems Principles, pages 85–100 ACM (2011)
Song, D. X., Wagner, D., and Perrig, A., Practical techniques for searches on encrypted data. In: Security and Privacy, 2000. S&P 2000. Proceedings IEEE Symposium on, pages 44–55, IEEE, p. 2000 (2000)
Xia, Z., Wang, X., Sun, X., and Wang, Q., A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 27(2):340–352 , 2016.
Zhangjie, F., Xingming, S., Qi, L., Lu, Z., and Jiangang, S., Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans. Commun. 98(1):190–200, 2015.
Acknowledgments
This work is supported by the National Natural Science Foundation of China under grant No. 61572294, and the Fundamental Research Funds of Shandong University under grant No.2016JC029.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Jiang, H., Li, X. & Xu, Q. An Improvement to a Multi-Client Searchable Encryption Scheme for Boolean Queries. J Med Syst 40, 255 (2016). https://doi.org/10.1007/s10916-016-0610-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0610-6