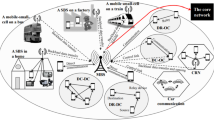
Abstract
In the growing area of Internet of Things (IoT), mobility management protocols become necessary because in today’s environment everything is movable so there is no dominance of static nodes. Mobility is a key aspect for the next-generation wireless network. So, mobility management mechanism is necessary for providing the seamless handoff to end user regardless of their location. Thus, Internet Engineering Task Force (IETF) has developed the Mobile IPv6 (MIPv6) for providing the mobility facility. But MIPv6 is not able to provide the mobility for next-generation wireless network due to large packet loss and high latency. Thus, Proxy MIPv6 (PMIPv6) is developed for providing the mobility for the next-generation network, but it has some limitation as well. In this paper, firstly a survey of various types of protocols based on PMIPv6 protocol is given. Then protocol is selected based on the Quality of Service (QoS) and signaling cost parameters. Two applications are considered i.e. streaming and background traffic class. For streaming traffic class, QoS (handoff latency) parameter is preferred and for background traffic class, signaling cost is preferred. Analytical Hierarchical Process (AHP) method is used for assigning the weight of different traffic class because user`s preferences play an important role in the decision-making process as it enhances the quality of experience of the user. Then multi-attribute decision making (MADM) and prospect theory are used for selection of protocols. Results show that different protocols are selected for different applications. The performance of MADM and prospect theory is shown in terms of accuracy.









Similar content being viewed by others
References
Duan, X., Wang, X.: Authentication handover and privacy protection in 5G hetnets using software-defined networking. IEEE Commun. Mag. 53(4), 28–35 (2015)
Astorga, J., Jacob, E., Toledo, N., Aguado, M.: Analytical evaluation of a time- and energy-efficient security protocol for IP-enabled sensors. Comput. Electr. Eng. 40(2), 539–550 (2014)
Ko, H., Lee, G., Pack, S., Member, S., Kweon, K.: Timer-Based Bloom Filter Aggregation for Reducing Signaling Overhead in Distributed Mobility Management. IEEE Trans. Mob. Comput. 15(2), 516–529 (2016)
Fernandez, P., Santa, J., Bernal, F., Gomez-Skarmeta, A.F.: Securing Vehicular IPv6 Communications. IEEE Trans. Dependable Secur. Comput. 13(1), 46–58 (2016)
Makaya, C., Pierre, S.: An Analytical Framework for Performance Evaluation of IPv6-Based Mobility Management Protocols. IEEE Trans. Wirel. Commun. 7(3), 972–983 (2008)
Kim, M.-S., Lee, S., Cypher, D., Golmie, N.: Performance analysis of fast handover for proxy Mobile IPv6. Inf. Sci. (Ny) 219, 208–224 (2013)
Lee, J.-H., Ernst, T., Chilamkurti, N.: Performance Analysis of PMIPv6-Based Network Mobility for Intelligent Transportation Systems. IEEE Trans. Veh. Technol. 61(1), 74–85 (2012)
J.-E. Kang, D.-W. Kum, Y. Li, and Y.-Z. Cho, “Seamless Handover Scheme for Proxy Mobile IPv6,” IEEE Int. Conf. Wirel. Mob. Comput. Netw. Commun., pp. 410–414, 2008
Makaya, C., Pierre, S.: Emerging Wireless Networks:Concepts, Techniques, and Applications. CRC Press, New York (2012)
Bouaziz, M., Rachedi, A.: A survey on mobility management protocols in Wireless Sensor Networks based on 6LoWPAN technology. Comput. Commun. 74, 3–15 (2016)
Saaty, T.L.: The Analytic Hierarchy and Analytic Network Measurement Processes: applications to Decisions under Risk. Eur. J. Pure Appl. Math. 1(1), 122–196 (2008)
Wang, L., Kuo, G.G.S.: Mathematical Modeling for Network Selection in Heterogeneous Wireless Networks – A Tutorial. IEEE Commun. Surv. Tutorials 15(1), 271–292 (2013)
J. D. Martínez-Morales, U. Pineda-Rico, and E. Stevens-Navarro, “Performance comparison between MADM algorithms for vertical handoff in 4G networks,” in 7th International Conference on Electrical Engineering, Computing Science and Automatic Control, CCE, 2010, pp. 309–314
Qin, J., Liu, X., Pedrycz, W.: An extended VIKOR method based on prospect theory for multiple attribute decision making under interval type-2 fuzzy environment. Knowledge-Based Syst. 86, 116–130 (2015)
Sgora, A., Gizelis, C.A., Vergados, D.D.: Network selection in a WiMAX–WiFi environment. Pervasive Mob. Comput. 7(5), 584–594 (2011)
Wang, L., Zhang, Z., Wang, Y.: A prospect theory-based interval dynamic reference point method for emergency decision making. Expert Syst. Appl. 42(23), 9379–9388 (2015)
Zhou, L., Zhong, S., Ma, S., Jia, N.: Prospect theory based estimation of drivers’ risk attitudes in route choice behaviors. Accid. Anal. Prev. 73, 1–11 (2014)
Cho, C., Kang, J.-J., Jeong, J.: Performance analysis of DNS-assisted global mobility management scheme in cost-optimized proxy mobile IPv6 Networks. Inf. Syst. 48, 226–235 (2015)
T. Y. Wu, W. K. Liu, and W. T. Lee, “Advanced handover enhancement for 6LoWPAN PMIPv6 by HF-PMIPv6,” Proc. - 2014 Int. Conf. Inf. Sci. Electron. Electr. Eng. ISEEE 2014, vol. 3, pp. 1770–1774, 2014
Ryu, S., Kim, G.Y., Kim, B., Mun, Y.: A scheme to reduce packet loss during PMIPv6 handover considering authentication. Proceedings - The International Conference on Computational Sciences and its Applications, ICCSA 6, 47–51 (2008)
M. Gohar, S. Il Choi, and S. J. Koh, “Fast handover using multicast handover agents in PMIPv6-based wireless networks,” in International Conference on Information Networking, ICOIN, 2011, pp. 367–372
W. Xu, Wu, Daneshmand, Liu, “Smart Buffering for seamless handover in Proxy Mobile IPv6,” Wirel. Commun. Mob. Comput., vol. 11, no. 4, pp. 491–499, 2011
Kwon, N., Kim, H., Oh, S., Choo, H.: Fast handover scheme based on mobility management of head MAG in PMIPv6. Springer ICCSA 6, 181–192 (2011)
M. C. Chuang and J. F. Lee, “FH-PMIPv6: A fast handoff scheme in Proxy Mobile IPv6 networks,” in International Conference on Consumer Electronics, Communications and Networks, CECNet, 2011, pp. 1297–1300
Yan, Z., Zhou, H., Wang, H.C., Zhang, H., Zhang, S.: Design and implementation of a hybrid MIPv6/PMIPv6-based mobility management architecture. Math. Comput. Model. 53(3–4), 421–442 (2011)
I. Al-Surmi, M. Othman, N. A. W. A. Hamid, and B. M. Ali, Latency low handover mechanism considering data traffic lost preventing for proxy mobile IPv6 over WLAN, vol. 70, no. 1. 2013
S. Ryu and Y. Mun, “Scheme to prevent packet loss during PMIPv6 handover,” in Transactions on Computational Science VI, 2009, pp. 131–142
I. Al-Surmi, M. Othman, and B. M. Ali, “Review on mobility management for future-IP-based next generation wireless networks,” in 12th International Conference on Advanced Communication Technology (ICACT), 2010, vol. 2, pp. 989–994
Koh, S.J., Gohar, M.: Multicast Handover Agents for Fast Handover in Wireless Multicast Networks. IEEE Commun. Lett. 14(7), 676–678 (2010)
H. Choi, K. Kim, H. Lee, and S. Min, “Reactive Smart Buffering Scheme for Seamless Handover in PMIPv6,” in International Conference On Principles Of Distributed Systems, 2008, pp. 568–571
Modares, H., Moravejosharieh, A., Lloret, J., Bin Salleh, R.: A survey on proxy mobile IPv6 handover. IEEE Syst. J. 10(1), 208–217 (2016)
Jabir, A.J., Subramaniam, S.K., Ahmad, Z.Z., Asilah, N., Hamid, W.A.: A cluster-based proxy mobile IPv6 for IP-WSNs. EURASIP J. Wirel. Commun. Netw. 173(1), 1–17 (2012)
Meenakshi and N. P. Singh, “A comparative study of cooperative and non-cooperative game theory in network selection,” in IEEE International Conference on Computational Techniques in Information and Communication Technologies (ICCTICT), 2016, pp. 612–617
M. Munjal and N. P. Singh, “Utility aware network selection in small cell,” Wirel. Networks, 2018
F. Bari and V. Leung, “Multi-Attribute Network Selection by Iterative TOPSIS for Heterogeneous Wireless Access,” in 4th IEEE Consumer Communications and Networking Conference, 2007, pp. 808–812
Verma, R., Singh, N.P.: GRA Based Network Selection in Heterogeneous Wireless Networks. Wirel. Pers. Commun. 72(2), 1437–1452 (2013)
Kahneman, D., Tversky, A.: Prospect Theory: an Analysis of Decision under Risk. Econometrica 47(2), 263–292 (1979)
Rosenfeld, A., Kraus, S.: Predicting Human Decision-Making: from Prediction to Action. Synth. Lect. Artif. Intell. Mach. Learn. 12(1), 1–150 (2018)
M. Munjal and N. P. Singh, “Improved network selection for multimedia applications,” Trans. Emerg. Telecommun. Technol., vol. 28, no. 5, 2017
Tversky, A., Kahneman, D.: Advances in Prospect-Theory - Cumulative Representation of Uncertainty. J. Risk Uncertain. 5(4), 297–323 (1992)
Nilsson, H., Rieskamp, J., Wagenmakers, E.J.: Hierarchical Bayesian parameter estimation for cumulative prospect theory. J. Math. Psychol. 55(1), 84–93 (2011)
Rieger, M.O., Wang, M., Hens, T.: Estimating cumulative prospect theory parameters from an international survey. Theory Decis. 82(4), 567–596 (2017)
Zhang, X., Liu, P.: Method for Multiple Attribute Decision-making under Risk with Interval Numbers. Int. J. Fuzzy Syst. 12(3), 237–242 (2010)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Munjal, M., Singh, N.P. QoS and Cost-Aware Protocol Selection for Next Generation Wireless Network. J Netw Syst Manage 27, 327–350 (2019). https://doi.org/10.1007/s10922-018-9467-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10922-018-9467-y