Abstract
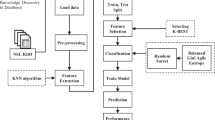
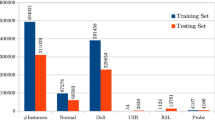
The development and expansion of the Internet and cyberspace have increased computer systems attacks; therefore, Intrusion Detection Systems (IDSs) are needed more than ever. Machine learning algorithms have recently been used as successful IDSs; however, due to the high dimensions in IDSs, Feature Selection (FS) plays an essential role in these systems' performance. In this paper, a binary version of the Farmland Fertility Algorithm (FFA) called BFFA is presented to FS in the classification of IDSs. In the proposed method, the V-shaped function is used to move the FFA processes in the binary space, as a result of which the V-shaped function changes the continuous position of the solutions in the FFA algorithm to binary mode. A hybrid approach to classifiers and the BFFA is presented as a fast and robust IDS. The proposed method is tested on two valid IDSs datasets, namely NSL-KDD and UNSW-NB15, and is compared in Accuracy, Precision, Recall, and F1_Score criteria with K-Nearest Neighbor (KNN), Support Vector Machine (SVM), Decision Tree (DT), Random Forest (RF), Adaboost (ADA_BOOST), and Naive Bayes (NB) classifiers. The simulation results showed that the proposed method performed better than the classifiers in Accuracy, Precision, and Recall criteria; moreover, the proposed method has a better run time in the FS operation.





















Similar content being viewed by others
References
Khammassi, C., Krichen, S.: A GA-LR wrapper approach for feature selection in network intrusion detection. Comput. Secur. 70, 255–277 (2017)
Samadi Bonab, M., et al.: A wrapper‐based feature selection for improving performance of intrusion detection systems. Int. J. Commun. Syst. 33, e4434 (2020)
Aldweesh, A., Derhab, A., Emam, A.Z.: Deep learning approaches for anomaly-based intrusion detection systems: a survey, taxonomy, and open issues. Knowl.-Based Syst. 189, 105124 (2020)
Husain, M.S.: Nature inspired approach for intrusion detection systems. In: Design and Analysis of Security Protocol for Communication, pp. 171–182 (2020)
Jiang, K., et al.: Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access 8, 32464–32476 (2020)
Nadimi-Shahraki, M.H., et al.: Migration-based Moth-flame optimization algorithm. Processes 9(12), 2276 (2021)
Zamani, H., Nadimi-Shahraki, M.H., Gandomi, A.H.: QANA: Quantum-based avian navigation optimizer algorithm. Eng. Appl. Artif. Intell. 104, 104314 (2021)
Nadimi-Shahraki, M.H., et al.: An improved Moth-flame optimization algorithm with adaptation mechanism to solve numerical and mechanical engineering problems. Entropy 23(12), 1637 (2021)
Ghafori, S., Gharehchopogh, F.S.: Advances in spotted hyena optimizer: a comprehensive survey. Arch. Comput. Methods Eng. 1, 1–22 (2021). https://doi.org/10.1007/s11831-021-09624-4
Zamani, H., Nadimi-Shahraki, M.H., Gandomi, A.H.: CCSA: conscious neighborhood-based crow search algorithm for solving global optimization problems. Appl. Soft Comput 85, 105583 (2019)
Nadimi-Shahraki, M.H., et al.: B-MFO: a binary moth-flame optimization for feature selection from medical datasets. Computers 10(11), 136 (2021)
Gharehchopogh, F.S., Shayanfar, H., Gholizadeh, H.: A comprehensive survey on symbiotic organisms search algorithms. Artif. Intell. Rev. 53, 2265–2312 (2019)
Gharehchopogh, F.S., Gholizadeh, H.: A comprehensive survey: whale optimization algorithm and its applications. Swarm Evol. Comput. 48, 1–24 (2019)
Garcia-Teodoro, P., et al.: Anomaly-based network intrusion detection: techniques, systems and challenges. Comput. Secur. 28(1–2), 18–28 (2009)
Rajamohana, S., Umamaheswari, K.: Hybrid approach of improved binary particle swarm optimization and shuffled frog leaping for feature selection. Comput. Electr. Eng. 67, 497–508 (2018)
Liao, T.W., Kuo, R.: Five discrete symbiotic organisms search algorithms for simultaneous optimization of feature subset and neighborhood size of knn classification models. Appl. Soft Comput. 64, 581–595 (2018)
Abdel-Basset, M., et al.: A new fusion of grey wolf optimizer algorithm with a two-phase mutation for feature selection. Exp. Syst. Appl. 139, 112824 (2020)
Shayanfar, H., Gharehchopogh, F.S.: Farmland fertility: a new metaheuristic algorithm for solving continuous optimization problems. Appl. Soft Comput. 71, 728–746 (2018)
Gharehchopogh, F.S., Abdollahzadeh, B.: An efficient harris hawk optimization algorithm for solving the travelling salesman problem. Clust. Comput. (2021). https://doi.org/10.1007/s10586-021-03304-5
Abdollahzadeh, B., Gharehchopogh, F.S.: A multi-objective optimization algorithm for feature selection problems. Eng. Comput. (2021). https://doi.org/10.1007/s00366-021-01369-9
Wei, W., et al.: A multi-objective immune algorithm for intrusion feature selection. Appl. Soft Comput. 95, 106522 (2020)
Alazzam, H., Sharieh, A., Sabri, K.E.: A feature selection algorithm for intrusion detection system based on Pigeon Inspired Optimizer. Exp. Syst. Appl. 148, 113249 (2020)
Nazir, A., Khan, R.A.: A novel combinatorial optimization based feature selection method for network intrusion detection. Comput. Secur. 102, 102164 (2021)
Eesa, A.S., Orman, Z., Brifcani, A.M.A.: A novel feature-selection approach based on the cuttlefish optimization algorithm for intrusion detection systems. Expert Syst. Appl. 42(5), 2670–2679 (2015)
Mohammadi, S., et al.: Cyber intrusion detection by combined feature selection algorithm. J. Inf. Secur. Appl. 44, 80–88 (2019)
Aghdam, M.H., Kabiri, P.: Feature selection for intrusion detection system using ant colony optimization. Int. J. Netw. Secur. 18(3), 420–432 (2016)
Ghanem, W., Jantan, A.: Novel multi-objective artificial bee Colony optimization for wrapper based feature selection in intrusion detection. Int. J. Adv. Soft Comput. Appl. 8(1) (2016)
Guo, C., et al.: A two-level hybrid approach for intrusion detection. Neurocomputing 214, 391–400 (2016)
Farnaaz, N., Jabbar, M.: Random forest modeling for network intrusion detection system. Procedia Comput. Sci. 89, 213–217 (2016)
Manzoor, I., Kumar, N.: A feature reduced intrusion detection system using ANN classifier. Expert Syst. Appl. 88, 249–257 (2017)
Aburomman, A.A., Reaz, M.B.I.: A survey of intrusion detection systems based on ensemble and hybrid classifiers. Comput. Secur. 65, 135–152 (2017)
Khorram, T., Baykan, N.A.: Feature selection in network intrusion detection using metaheuristic algorithms. Int. J. Adv. Res. Ideas Innov. Technol. 4(4), 704–710 (2018)
Acharya, N., Singh, S.: An IWD-based feature selection method for intrusion detection system. Soft. Comput. 22(13), 4407–4416 (2018)
Papamartzivanos, D., Mármol, F.G., Kambourakis, G.: Dendron: genetic trees driven rule induction for network intrusion detection systems. Future Gener. Comput. Syst. 79, 558–574 (2018)
Selvakumar, B., Muneeswaran, K.: Firefly algorithm based feature selection for network intrusion detection. Comput. Secur. 81, 148–155 (2019)
Alzubi, Q.M., et al.: Intrusion detection system based on a modified binary grey wolf optimisation. Neural Comput. Appl. 32, 6125–6137 (2019)
Garg, L., Aggarwal, N.: A hybrid feature reduced approach for intrusion detection system. In: Computing and Network Sustainability, pp. 179–186. Springer, Berlin (2019)
Su, T., et al.: BAT: deep learning methods on network intrusion detection using NSL-KDD dataset. IEEE Access 8, 29575–29585 (2020)
Benyamin, A., Farhad, S.G., Saeid, B.: Discrete farmland fertility optimization algorithm with metropolis acceptance criterion for traveling salesman problems. Int. J. Intell. Syst. 36(3), 1270–1303 (2021)
Gharehchopogh, F.S., Farnad, B., Alizadeh, A.: A modified farmland fertility algorithm for solving constrained engineering problems. Concurr. Comput.: Pract. Exp. 33(17), e6310 (2021)
Hosseinalipour, A., et al.: A novel binary farmland fertility algorithm for feature selection in analysis of the text psychology. Appl. Intell. 51, 4824–4859 (2021)
Kevric, J., Jukic, S., Subasi, A.: An effective combining classifier approach using tree algorithms for network intrusion detection. Neural Comput. Appl. 28(1), 1051–1058 (2017)
Dhanabal, L., Shantharajah, S.: A study on NSL-KDD dataset for intrusion detection system based on classification algorithms. Int. J. Adv. Res. Comput. Commun. Eng. 4(6), 446–452 (2015)
Moustafa, N., Slay, J.: UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In: 2015 Military Communications and Information Systems Conference (MilCIS). IEEE (2015)
Mirjalili, S., Lewis, A.: S-shaped versus V-shaped transfer functions for binary particle swarm optimization. Swarm Evol. Comput. 9, 1–14 (2013)
Arora, S., Anand, P.: Binary butterfly optimization approaches for feature selection. Expert Syst. Appl. 116, 147–160 (2019)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Naseri, T.S., Gharehchopogh, F.S. A Feature Selection Based on the Farmland Fertility Algorithm for Improved Intrusion Detection Systems. J Netw Syst Manage 30, 40 (2022). https://doi.org/10.1007/s10922-022-09653-9
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10922-022-09653-9