Abstract
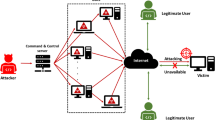
The IoT network is unique due to heterogeneous IoT nodes and resource-constrained devices; the approach for securing IoT networks needs to be different from the security measures implemented for traditional network communication. In IoT networks, various security vulnerabilities are exploited by an attacker to generate a variety of DDoS attacks. In this paper, the authors propose a unique approach for securing IoT networks using an SDN-enabled framework that incorporates a dynamic counter-based approach and deep learning models. The aim is to detect and mitigate various security vulnerabilities that attackers exploit to generate DDoS attacks in IoT networks. Specifically, the proposed framework is tested using the CICDDoS2019 dataset to identify reflection attacks and exploitation attacks in TCP, UDP, and ICMP. The framework is also analyzed by varying network parameters such as the number of IoT attack nodes and payload to measure the performance of the SDN controller workload, CPU utilization, and attack detection time. The experimental results demonstrate that the proposed framework can efficiently detect and mitigate DDoS attacks while utilizing CPU resources effectively and in a shorter time compared to existing approaches.





















Similar content being viewed by others
Data Availability
CIC-DDoS2019 dataset is utilised from https://www.unb.ca/cic/datasets/ddos-2019.html.
References
Taylor, R., Schmidt, D.B.: The world in 2025—predictions for the next ten years. In: Paper Presented at the 10th International Microsystems, Packaging, Assembly and Circuits Technology Conference (IMPACT). https://doi.org/10.1109/IMPACT.2015.7365193 (2015).
Abbasinezhad-Mood, D., Nikooghadam, M.: An anonymous ECC-based self-certified key distribution scheme for the smart grid. IEEE Trans. Ind. Electron. 65(10), 7996–8004 (2018). https://doi.org/10.1109/TIE.2018.2807383
Abbasinezhad-Mood, D., Ostad-Sharif, A., Nikooghadam, M.: Novel anonymous key establishment protocol for isolated smart meters. IEEE Trans. Ind. Electron. 67(4), 2844–2851 (2019). https://doi.org/10.1109/TIE.2019.2912789
Abbasinezhad-Mood, D., Nikooghadam, M.: Efficient design of a novel ECC-based public key scheme for medical data protection by utilization of NanoPi fire. IEEE Trans. Reliab. 67(3), 1328–1339 (2018). https://doi.org/10.1109/TR.2018.2850966
Ge, Y., Zhang, X., Han, B.: Complex IoT control system modeling from perspectives of environment perception and information security. Mobile Netw. Appl. 22(4), 683–691 (2017). https://doi.org/10.1007/s11036-017-0846-5
Yin, D., Zhang, L., Yang, K.: A DDOS attack detection and mitigation with software-defined internet of things framework. IEEE Access 6, 24694–24705 (2018). https://doi.org/10.1109/ACCESS.2018.2831284
Yang, Y., Wu, L., Yin, G., Li, L., Zhao, H.: A survey on security and privacy issues in internet-of-things. IEEE Internet Things J. 4(5), 1250–1258 (2017). https://doi.org/10.1109/JIoT.2017.2694844
Zhang, J., Chen, H., Gong, L., Cao, J., Gu, Z.: The current research of IoT security. In: 2019 IEEE Fourth International Conference on Data Science in Cyberspace (DSC), pp. 346–353. IEEE, New York. https://doi.org/10.1109/DSC.2019.00059 (2019).
Miettinen, M., Marchal, S., Hafeez, I., Asokan, N., Sadeghi, A.-R., Tarkoma, S.: IoT sentinel: automated device-type identification for security enforcement in IoT. In: 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), pp. 2177–2184. IEEE, New York. https://doi.org/10.1109/ICDCS.2017.283 (2017).
Galluccio, L., Milardo, S., Morabito, G., Palazzo, S.: SDN-wise: design, prototyping and experimentation of a stateful SDN solution for wireless sensor networks. In: 2015 IEEE Conference on Computer Communications (INFOCOM), pp. 513–521. IEEE, New York. https://doi.org/10.1109/INFOCOM.2015.7218418 (2015).
Kalkan, K., Zeadally, S.: Securing internet of things with software defined networking. IEEE Commun. Mag. 56(9), 186–192 (2017). https://doi.org/10.1109/MCOM.2017.1700714
Chen, Y.-W., Sheu, J.-P., Kuo, Y.-C., Van Cuong, N.: Design and implementation of IoT DDOS attacks detection system based on machine learning. In: 2020 European Conference on Networks and Communications (EuCNC), pp. 122–127. IEEE, New York. https://doi.org/10.1109/EuCNC48522.2020.9200909 (2020).
AbdelAzim, N.M., Fahmy, S.F., Sobh, M.A., Eldin, A.M.B.: A hybrid entropy-based DoS attacks detection system for software defined networks (SDN): a proposed trust mechanism. Egypt. Inform. J. 22(1), 85–90 (2021). https://doi.org/10.1016/j.eij.2020.04.005
Kumar, N., Mittal, N., Thakur, P., Srivastava, R.: Analysis of different detection and mitigation algorithm of DDoS attack in software-defined internet of things framework: A review. Recent Trends Adv. Artif. Intell. Internet Things (2020). https://doi.org/10.1007/978-3-030-32644-9_39
Zarca, A.M., Bernabe, J.B., Skarmeta, A., Calero, J.M.A.: Virtual IoT honeynets to mitigate cyberattacks in SDN/NFV-enabled IoT networks. IEEE J. Sel. Areas Commun. 38(6), 1262–1277 (2020). https://doi.org/10.1109/JSAC.2020.2986621
Giotis, K., Argyropoulos, C., Androulidakis, G., Kalogeras, D., Maglaris, V.: Combining openflow and sflow for an effective and scalable anomaly detection and mitigation mechanism on SDN environments. Comput. Netw. 62, 122–136 (2014). https://doi.org/10.1016/j.bjp.2013.10.014
Wani, A., Revathi, S.: DDoS detection and alleviation in IoT using SDN (SDIoT-DDoS-DA). J. Inst. Eng. India Ser. B 101(2), 117–128 (2020). https://doi.org/10.1007/s40031-020-00442-z
Bhayo, J., Hameed, S., Shah, S.A.: An efficient counter-based DDoS attack detection framework leveraging software defined IoT (SD-IoT). IEEE Access 8, 221612–221631 (2020). https://doi.org/10.1109/ACCESS.2020.3043082
Galeano-Brajones, J., Carmona-Murillo, J., Valenzuela-Valdés, J.F., Luna-Valero, F.: Detection and mitigation of DoS and DDoS attacks in IoT-based stateful SDN: an experimental approach. Sensors 20(3), 816 (2020). https://doi.org/10.3390/s20030816
Yang, Y., Wang, J., Zhai, B., Liu, J.: IoT-based DDoS attack detection and mitigation using the edge of SDN. In: International Symposium on Cyberspace Safety and Security, pp. 3–17. Springer, New York. https://doi.org/10.1007/978-3-030-37352-8_1 (2019).
Yin, D., Zhang, L., Yang, K.: A DDoS attack detection and mitigation with software-defined internet of things framework. IEEE Access 6, 24694–24705 (2018). https://doi.org/10.1109/ACCESS.2018.2831284
Silveira, F.A.F., Lima-Filho, F., Silva, F.S.D., Junior, A.d.M.B., Silveira, L.F.: Smart detection-IoT: a DDoS sensor system for internet of things. In: 2020 International Conference on Systems, Signals and Image Processing (IWSSIP), pp. 343–348. IEEE, New York. https://doi.org/10.1109/IWSSIP48289.2020.9145265 (2020).
Bull, P., Austin, R., Popov, E., Sharma, M., Watson, R.: Flow based security for IoT devices using an SDN gateway. In: 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), pp. 157–163. IEEE, New York. https://doi.org/10.1109/FiCloud.2016.30 (2016).
Ninikrishna, T., Sarkar, S., Tengshe, R., Jha, M.K., Sharma, L., Daliya, V., Routray, S.K.: Software defined IoT: issues and challenges. In: 2017 International Conference on Computing Methodologies and Communication (ICCMC), pp. 723–726. IEEE, New York. https://doi.org/10.1109/ICCMC.2017.8282560 (2017).
Yungaicela-Naula, N.M., Vargas-Rosales, C., Perez-Diaz, J.A.: SDN-based architecture for transport and application layer DDoS attack detection by using machine and deep learning. IEEE Access 9, 108495–108512 (2021). https://doi.org/10.1109/ACCESS.2021.3101650
Sarica, A.K., Angin, P.: A novel SDN dataset for intrusion detection in IoT networks. In: 2020 16th International Conference on Network and Service Management (CNSM), pp. 1–5. IEEE, New York. https://doi.org/10.23919/CNSM50824.2020.9269042 (2020).
Idhammad, M., Afdel, K., Belouch, M.: Semi-supervised machine learning approach for DDoS detection. Appl. Intell. 48(10), 3193–3208 (2018). https://doi.org/10.1007/s10489-018-1141-2
Priyadarshini, R., Barik, R.K.: A deep learning based intelligent framework to mitigate DDoS attack in fog environment. J. King Saud Univ.-Comput. Inf. Sci. (2019). https://doi.org/10.1016/j.jksuci.2019.04.010
Novaes, M.P., Carvalho, L.F., Lloret, J., Proença, M.L.: Long short-term memory and fuzzy logic for anomaly detection and mitigation in software-defined network environment. IEEE Access 8, 83765–83781 (2020). https://doi.org/10.1109/ACCESS.2020.2992044
Tuan, N.N., Hung, P.H., Nghia, N.D., Tho, N.V., Phan, T.V., Thanh, N.H.: A DDoS attack mitigation scheme in ISP networks using machine learning based on SDN. Electronics 9(3), 413 (2020). https://doi.org/10.3390/electronics9030413
Gumaste, S., Shinde, S., et al.: Detection of DDoS attacks in openstack-based private cloud using apache spark. J. Telecommun. Inf. Technol. (2020). https://doi.org/10.26636/jtit.2020.146120
Tan, L., Pan, Y., Wu, J., Zhou, J., Jiang, H., Deng, Y.: A new framework for DDoS attack detection and defense in SDN environment. IEEE Access 8, 161908–161919 (2020). https://doi.org/10.1109/ACCESS.2020.3021435
Cherian, M.M., Varma, S.L.: Mitigation of DDoS and MITM attacks using belief based secure correlation approach in SDN-based IoT networks. Int. J. Comput. Netw. Inf. Secur. (2022). https://doi.org/10.1007/978-3-030-37352-8_1
Bouzidi, E.H., Outtagarts, A., Langar, R., Boutaba, R.: Dynamic clustering of software defined network switches and controller placement using deep reinforcement learning. Comput. Netw. 207, 108852 (2022). https://doi.org/10.1016/j.comnet.2022.108852
Cil, A.E., Yildiz, K., Buldu, A.: Detection of DDoS attacks with feed forward based deep neural network model. Expert Syst. Appl. 169, 114520 (2021). https://doi.org/10.1016/j.eswa.2020.114520
Kandoi, R., Antikainen, M.: Denial-of-service attacks in openflow SDN networks. In: 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), pp. 1322–1326. IEEE, New York (2015).
Sharafaldin, I., Lashkari, A.H., Hakak, S., Ghorbani, A.A.: Developing realistic distributed denial of service (DDoS) attack dataset and taxonomy. In: 2019 International Carnahan Conference on Security Technology (ICCST), pp. 1–8. IEEE, New York (2019).
Kachavimath, A.V., Narayan, D.: A deep learning-based framework for distributed denial-of-service attacks detection in cloud environment. In: Advances in Computing and Network Communications: Proceedings of CoCoNet 2020, vol 1, pp. 605–618. Springer, New York. https://doi.org/10.1007/978-981-33-6977-1_44 (2021)
Ahanger, T.A., Aljumah, A., Atiquzzaman, M.: State-of-the-art survey of artificial intelligent techniques for IoT security. Comput. Netw. (2022). https://doi.org/10.1016/j.comnet.2022.108771
Wang, S., Gomez, K., Sithamparanathan, K., Asghar, M.R., Russello, G., Zanna, P.: Mitigating DDoS attacks in SDN-based IoT networks leveraging secure control and data plane algorithm. Appl. Sci. 11(3), 929 (2021). https://doi.org/10.3390/app11030929
Shurman, M.M., Khrais, R.M., Yateem, A.A., et al.: DoS and DDoS attack detection using deep learning and IDS. Int. Arab J. Inf. Technol. 17(4A), 655–661 (2020). https://doi.org/10.34028/iajit/17/4A/10
Kumar, K., Behal, S., et al.: Distributed denial of service attack detection using deep learning approaches. In: 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom), pp. 491–495. IEEE, New York (2021).
Sha, M., Boukerche, A.: Performance evaluation of CNN-based pedestrian detectors for autonomous vehicles. Ad Hoc Netw. 128, 102784 (2022). https://doi.org/10.1016/j.adhoc.2022.102784
Kousar, H., Mulla, M.M., Shettar, P., Narayan, D.: Detection of DDoS attacks in software defined network using decision tree. In: 2021 10th IEEE International Conference on Communication Systems and Network Technologies (CSNT), pp. 783–788. IEEE, New York. https://doi.org/10.1109/CSNT51715.2021.9509634 (2021).
Le, T., Shetty, S.: Artificial intelligence-aided privacy preserving trustworthy computation and communication in 5G-based IoT networks. Ad Hoc Netw. 126, 102752 (2022). https://doi.org/10.1016/j.adhoc.2021.102752
Ali, J., Lee, S., Roh, B.-H.: Performance analysis of Pox and Ryu with different SDN topologies. In: Proceedings of the 2018 International Conference on Information Science and System, pp. 244–249. https://doi.org/10.1145/3209914.3209931 (2018).
Prasad, A., Chandra, S.: VMFCVD: an optimized framework to combat volumetric DDoS attacks using machine learning. Arab. J. Sci. Eng. (2022). https://doi.org/10.1007/s13369-021-06484-9
Kushwah, G.S., Ranga, V.: Optimized extreme learning machine for detecting DDoS attacks in cloud computing. Comput. Secur. 105, 102260 (2021). https://doi.org/10.1016/j.cose.2021.102260
Elsayed, M.S., Le-Khac, N.-A., Dev, S., Jurcut, A.D.: Ddosnet: a deep-learning model for detecting network attacks. In: 2020 IEEE 21st International Symposium On“ A World of Wireless, Mobile and Multimedia Networks”(WoWMoM), pp. 391–396. IEEE, New York. https://doi.org/10.1109/WoWMoM49955.2020.00072 (2020)
Bolodurina, I., Shukhman, A., Parfenov, D., Zhigalov, A., Zabrodina, L.: Investigation of the problem of classifying unbalanced datasets in identifying distributed denial of service attacks. J. Phys. Conf. Ser. (IOP Publishing) 1679, 042020 (2020). https://doi.org/10.1088/1742-6596/1679/4/042020
Author information
Authors and Affiliations
Contributions
M.C. and S.L.V. have equally contributed.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Ethical Approval
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Cherian, M., Varma, S.L. Secure SDN–IoT Framework for DDoS Attack Detection Using Deep Learning and Counter Based Approach. J Netw Syst Manage 31, 54 (2023). https://doi.org/10.1007/s10922-023-09749-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10922-023-09749-w