Abstract
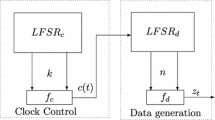
This paper considers security implications of k-normal Boolean functions when they are employed in certain stream ciphers. A generic algorithm is proposed for cryptanalysis of the considered class of stream ciphers based on a security weakness of k-normal Boolean functions. The proposed algorithm yields a framework for mounting cryptanalysis against particular stream ciphers within the considered class. Also, the proposed algorithm for cryptanalysis implies certain design guidelines for avoiding certain weak stream cipher constructions. A particular objective of this paper is security evaluation of stream cipher Grain-128 employing the developed generic algorithm. Contrary to the best known attacks against Grain-128 which provide complexity of a secret key recovery lower than exhaustive search only over a subset of secret keys which is just a fraction (up to 5%) of all possible secret keys, the cryptanalysis proposed in this paper provides significantly lower complexity than exhaustive search for any secret key. The proposed approach for cryptanalysis primarily depends on the order of normality of the employed Boolean function in Grain-128. Accordingly, in addition to the security evaluation insights of Grain-128, the results of this paper are also an evidence of the cryptographic significance of the normality criteria of Boolean functions.
Similar content being viewed by others
References
A. Biryukov and A. Shamir, Cryptanalytic time/memory/data tradeoffs for stream ciphers, ASIACRYPT 2000, Lecture Notes in Computer Science, 1976, 2000, 1–13.
A. Biryukov, A. Shamir and D. Wagner, Real time cryptanalysis of A5/1 on a PC, FSE 2001, Lecture Notes in Computer Science, 1978, 2008, 37–44.
T. E. Bjørstad, Cryptanalysis of Grain using time/memory/data tradeoffs, 2008, http://www.ecrypt.eu.org/stream/grainp3.html.
P. Camion, C. Carlet, P. Charpin and N. Sendrier, On correlation immune functions, CRYPTO’91, Lecture Notes in Computer Science, 576, 1991, 86–100.
A. Canteaut, M. Daum, H. Dobbertin and G. Leander, Finding nonnormal bent functions, Discrete Appl. Math., 154 (2006), 202–218.
C. Carlet, More correlation immune and resilient functions over Galois fields and Galois rings, EUROCRYPT’97, Lecture Notes in Computer Science, 1233, 1997, 422–433.
C. Carlet, The complexity of Boolean functions from cryptographic viewpoint, Dagstuhl Seminar Proceedings 06111: Complexity of Boolean Functions (2006), paper #604; http://drops.dagstuhl.de/opus/volltexte/2006/604.
P. Charpin, Normal Boolean functions, J. Complexity, 20 (2004), 245–265.
N. Courtois and W. Meier, Algebraic attacks on stream ciphers with linear feedback, EUROCRYPT 2003, Lecture Notes in Computer Science, 2656, 2003, 345–359.
I. Dinur, T. Güneysu, C. Paar, A. Shamir and R. Zimmermann, An experimentally verifed attack on full Grain-128 using dedicated reconfgurable hardware, ASI-ACRYPT 2011, Lecture Notes in Computer Science, Cryptology ePrint Archive, Report 282, 2011, to appear.
I. Dinur and A. Shamir, Cube attacks on tweakable black box polynomials, EU-ROCRYPT 2009, Lecture Notes in Computer Science, 5479, 2009, 278–299.
I. Dinur and A. Shamir, Breaking Grain-128 with dynamic cube attacks, FSE 2011, Cryptology ePrint Archive, Report 570, 2010.
H. Dobbertin, Construction of bent functions and balanced Boolean functions with high nonlinearity, FSE’94, Lecture Notes in Computer Science, 1008, 1995, 61–74.
O. Dunkelman and N. Keller, Treatment of the initial value in time-memory-data tradeoff attacks on stream ciphers, Information Processing Letters, 107 (2008), 133–137.
ECRYPT, The eSTREAM Project — Phase 3, http://www.ecrypt.eu.org/stream/grainpf.html.
ESTREAM, Portfolio of ECRYPT project, http://www.ecrypt.eu.org/stream/announcements.html.
S. Fischer, S. Khazaei and W. Meier, Chosen IV statistical analysis for key recovery attacks on stream ciphers, AFRICACRYPT 2008, Lecture Notes in Computer Science, 5023, 2008, 236–245.
M. Fossorier, M. J. Mihaljević and H. Imai, Modeling block encoding approaches for fast correlation attack, IEEE Transactions on Information Theory, 53: 12 (2007), 4728–4737.
M. Hell, T. Johansson, A. Maximov and W. Meier, A stream cipher proposal: Grain-128, Proc. 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, July 9–14, 2006, 1614–1618.
M. Hell, T. Johansson, A. Maximov and W. Meier, The Grain family of stream ciphers, New Stream Ciphers Design, Lecture Notes in Computer Science, 4986, 2008, 179–190.
M. Hell, T. Johansson and W. Meier, Grain — A Stream Cipher for Constrained Environments, eSTREAM, ECRYPT Stream Cipher Project, 2006, http://www.ecrypt.eu.org/stream/grainp3.html.
M. E. Hellman, A cryptanalytic time-memory trade-off, IEEE Transactions on Information Theory, 26 (1980), 401–406.
G. Leander and G. Mcguire, Construction of bent functions from near-bent functions, J. Combin. Theory, Ser. A, 116 (2009), 960–970.
Y. Lee, K. Jeong, J. Sung and S. Hong, Related-key chosen IV attacks on Grainv1 and Grain-128, ACISP 2008, Lecture Notes in Computer Science, 5107, 2008, 321–335.
S. Maitra and P. Sarkar, Highly nonlinear resilient functions optimizing Siegnethaler’s Inequality, CRYPTO’99, Lecture Notes in Computer Science, 1666, 1999, 198–215.
M. J. Mihaljević, Decimation based correlation and algebraic attacks and design of Boolean functions, Boolean Functions in Cryptology and Information Security (eds. B. Preneel and O. A. Logachev), NATO Science for Peace and Security Series D: Information and Communication Security, 18, IOS Press, Amsterdam, The Netherlands, 2008, 183–199.
M. J. Mihaljević, S. Gangopadhyay, G. Paul and H. Imai, Internal state recovery of Grain-v1 employing normality order of the filter function, IET Information Security, 6 (2012), 55–64.
E. Pasalić, On guess and determine cryptanalysis of LFSR-based stream ciphers, IEEE Transaction on Information Theory, 55 (2009), 3398–3406.
P. Sarkar and S. Maitra, Nonlinearity bounds and constructions of resilient Boolean functions, CRYPTO’00, Lecture Notes in Computer Science, 1880, 2000, 515–532.
T. Siegenthaler, Decrypting a class of stream ciphers by using ciphertext only, IEEE Trans. Computers, C-34 (1985), 81–85.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mihaljević, M.J., Gangopadhyay, S., Paul, G. et al. Generic cryptographic weakness of k-normal Boolean functions in certain stream ciphers and cryptanalysis of grain-128. Period Math Hung 65, 205–227 (2012). https://doi.org/10.1007/s10998-012-4631-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10998-012-4631-8