Abstract
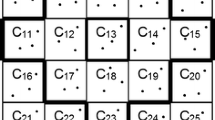
We propose a probabilistic key predistribution scheme for wireless sensor networks, where keying materials are distributed to sensor nodes for secure communication. We use a two-tier approach in which there are two types of nodes: regular nodes and agent nodes. Agent nodes are more capable than regular nodes. Our node deployment model is zone-based such that the nodes that may end up with closer positions on ground are grouped together. The keying material of nodes that belong to different zones is non-overlapping. However, it is still possible for nodes that belong to different zones to communicate with each other via agent nodes when needed. We give a comparative analysis of our scheme through simulations and show that our scheme provides good connectivity figures at reasonable communication cost by using minimal flooding in key distribution. Moreover, we show that our scheme is scalable such that no extra overhead in incurred in case of increased number of nodes and sensor field size. Most importantly, simulation results show that our scheme is highly resilient to node captures.


















Similar content being viewed by others
Notes
In this paper, we use restricted flooding in which a query is broadcasted by a node only once; when the same query is received again by the same node, it is simply dropped and not broadcasted. In this way, the communication cost caused by flooding is reduced as compared to unrestricted flooding in which a particular node unnecessarily broadcasts duplicate queries.
References
Eschenauer L, Gligor VD (2002) A key-management scheme for distributed sensor networks. Proceedings of the 9th ACM Conference on Computer and Communications Security, November 2002, pp 41–47
Blom R (1985) An optimal class of symmetric key generation system. Advances in Cryptology—Eurocrypt’84. LNCS, 209, 335–338. Springer
Akyildiz IF, Su W, Sankarasubramaniam Y, Cayirci E (2002) A survey on sensor networks. IEEE Commun Mag 40(8):102–114. doi:10.1109/MCOM.2002.1024422
Malan D (2004) Crypto for tiny objects. Harvard University Technical Report TR-04-04
Gaubatz G, Kaps J, Sunar B (2004) Public keys cryptography in sensor networks—revisited. Proceedings of the 1st European Workshop on Security in Ad-Hoc and Sensor Networks (ESAS), LNCS 3313:2–18, Springer
Watro R, Kong D, Cuti S, Gardiner C, Lynn C, Kruus P (2004) Securing sensor networks with public key technology. Proceedings of the 2nd ACM Workshop on Security of Ad hoc and Sensor Networks, October 2004
Chan H, Perrig A, Song D (2003) Random key predistribution schemes for sensor networks. IEEE Symposium on Research in Security and Privacy 197–213
Du W, Deng J, Han YS, Chen S, Varshney P (2004) A key management scheme for wireless sensor networks using deployment knowledge. Proceedings of IEEE INFOCOM’04, March 2004
Du W, Deng J, Han YS, Varshney P (2003) A pairwise key predistribution scheme for wireless sensor networks. Proceedings of 10th ACM Conference on Computer and Communications Security (CCS’03), pp 42–51
Liu D, Ning P (2003) Establishing pairwise keys in distributed sensor networks. Proceedings of 10th ACM Conference on Computer and Communications Security (CCS’03), pp. 52–61, October 2003
Liu D, Ning P (2003) Location-based pairwise key establishments for static sensor networks. 2003 ACM Workshop on Security in Ad Hoc and Sensor Networks (SASN ’03), pp. 72–82
Zhu S, Setia S, Jajodia S (2003) LEAP: Efficient security mechanisms for large-scale distributed sensor networks. Proceedings of 10th ACM Conference on Computer and Communications Security (CCS’03), pp. 62–72.
Anderson R, Kuhn M (1996) Tamper resistance—a cautionary note. Proceedings of the Second Usenix Workshop on Electronic Commerce, pp. 1–11
Lin HY, Pan DJ, Zhao XX, Qiu ZR (2008) A rapid and efficient pre-deployment key scheme for secure data transmissions in sensor networks using lagrange interpolation polynomial. International Journal of Security and its Applications 2(3):49–55
Liu D, Ning P, Du W (2005) Group-based key pre-distribution in wireless sensor networks, Proceedings of 2005 ACM Workshop on Wireless Security, September 2, 2005, Cologne, Germany pp. 11–20
Huang D, Mehta M, Medhi D, Harn L (2004) Location-aware key management scheme for wireless sensor networks, Proceedings of the 2nd ACM Workshop on Security of Ad hoc and Sensor Networks, October 2004, Washington, DC, USA, pp. 29–42
Zhou L, Ni J, Ravishankar CV (2005) Efficient key establishment for group-based wireless sensor deployments. Proceedings of 2005 ACM Workshop on Wireless Security, Sept. 2005, Cologne, Germany pp. 1–10
Shi E, Perrig A (2004) Designing secure sensor networks. IEEE Wirel Commun 11(6):38–43. doi:10.1109/MWC.2004.1368895
Unlu A, Levi A (2008) Two-tier, location-aware and highly resilient key predistribution scheme for wireless sensor networks, Proceedings of Visions of Computer Science—BCS International Academic Conference, London, UK, September 2008, pp. 355–366
Perrig A, Szewcyzk R, Wen V, Culler D, Tygar JD (2002) Spins: security protocols for sensor networks. Wirel Netw 8(5):521–534. doi:10.1023/A:1016598314198
Dressler F (2008) Authenticated Reliable and Semi-reliable Communication in Wireless Sensor Networks. International Journal of Network Security 7(1):61–68
Levi A, Tasci SE, Lee YJ, Lee YJ, Bayramoglu E, Ergun M (2009) Simple, extensible and flexible random key predistribution schemes for wireless sensor networks using reusable key pools. Journal of Intelligent Manufacturing, accepted for publication. http://dx.doi.org/10.1007/s10845-009-0256-z
Acknowledgements
This work is supported by Scientific and Technological Research Council of Turkey (TÜBİTAK) under grant 104E071
Author information
Authors and Affiliations
Corresponding author
Additional information
This paper is extended version of [19].
Rights and permissions
About this article
Cite this article
Ünlü, A., Levi, A. Two-Tier, Scalable and Highly Resilient Key Predistribution Scheme for Location-Aware Wireless Sensor Network Deployments. Mobile Netw Appl 15, 517–529 (2010). https://doi.org/10.1007/s11036-009-0188-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-009-0188-z