Abstract
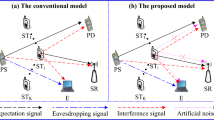
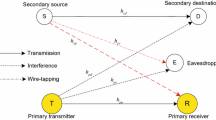
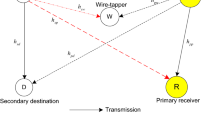
Interference from primary transmitters in underlay cognitive networks is practically neither neglected nor integrated into noise terms although most literature inversely addressed. This paper firstly employs a helpful jammer to secure information transmission of a secondary transmitter. Then, its efficacy through secrecy outage probability under practical considerations consisting of exponentially distributed interference from primary transmitter, peak transmission power limitation, interference power limitation, and Rayleigh fading channels are analytically assessed. Finally, results are provided to illustrate significant security performance improvement thanks to exploiting the jammer while considerable security performance degradation due to interference from primary transmitter.




Similar content being viewed by others
Notes
This can be alternatively interpreted that jamming signal is transmitted in the null space to SD or shared with SD (e.g., use the seed of the jamming signal generator in a secure manner). Such interpretations are widely accepted in open literature (e.g., [17,18,19,20, 22, 27,28,29] and references therein).
References
Panwar N, Sharma S, Singh AK (2016) A survey on 5G: the next generation of mobile communication. Elsevier Physical Communication 18(2):64–84
Tavana M, Rahmati A, Shah-Mansouri V, Maham B (2017) Cooperative sensing with joint energy and correlation detection in cognitive radio networks. IEEE Commun Lett 21(1):132–135
Ho-Van K (2016) Exact outage probability analysis of proactive relay selection in cognitive radio networks with MRC receivers. IEEE/KICS Journal of Communications and Networks 18(3):288–298
Darsena D, Gelli G, Verde F (2017) An opportunistic spectrum access scheme for multicarrier cognitive sensor networks. IEEE Sensors J 17(8):2596–2606
Liu Y, Chen H, Wang L (2017) Physical layer security for next generation wireless networks: theories, technologies, and challenges. IEEE Commun Surv Tutorials 19(1):347–376. First Quarter
Sharma R, Rawat D (2015) Advances on security threats and countermeasures for cognitive radio networks: a survey. IEEE Commun Surv Tutorials 17(2):1023–1043
Gan Z, Li-Chia C, Kai-Kit W (2011) Optimal cooperative jamming to enhance physical layer security using relays. IEEE Trans Sig Processing 59(3):1317–1322
Zhihui S, Yi Q, Song C (2013) On physical layer security for cognitive radio networks. IEEE Netw 27:28–33
Yulong Z, Jia Z, Liuqing Y, Ying-chang L, Yu-dong Y (2015) Securing physical-layer communications for cognitive radio networks. IEEE Commun Mag 53:48–54
Li J, Feng Z, Feng Z, Zhang P (2015) A survey of security issues in cognitive radio networks. China Communications 12:132– 150
Zheng TX, Wang HM (2016) Optimal power allocation for artificial noise under imperfect CSI against spatially random eavesdroppers. IEEE Trans Veh Tech 65(10):8812–8817
Hu J, Cai Y, Yang N, Zhou X, Yang W (2017) Artificial-noise-aided secure transmission scheme with limited training and feedback overhead. IEEE Trans Wire Commun 16(1):193–205
Wang C, Wang HM (2014) On the secrecy throughput maximization for MISO cognitive radio network in slow fading channels. IEEE Trans Inf Forensics Secur 9(11):1814–1827
Ho-Van K (2015) Outage analysis in cooperative cognitive networks with opportunistic relay selection under imperfect channel information. Int J Electron Commun 69(11):1700–1708
Wang D, Ren P, Du Q, Sun L, Wang Y (2016) Cooperative relaying and jamming for primary secure communication in cognitive two-way networks. In: Proceedings of IEEE VTC. Nanjing, China, pp 1–5
Fang B, Qian Z, Zhong W, Shao W (2015) AN-Aided secrecy precoding for SWIPT in cognitive MIMO broadcast channels. IEEE Commun Lett 19(9):1632–1635
Nguyen VD, Duong TQ, Dobre OA, Shin OS (2016) Joint information and jamming beamforming for secrecy rate maximization in cognitive radio networks. IEEE Trans Inf Forensics Secur 11(11):2609–2623
Fang B, Qian Z, Shao W, Zhong W (2016) Precoding and artificial noise design for cognitive MIMOME wiretap channels. IEEE Trans Veh Tech 65(8):6753–6758
Wu Y, Chen X, Chen X (2015) Secure beamforming for cognitive radio networks with artificial noise. In: Proceedings of IEEE WCSP. Nanjing, China, pp 1–5
Hu X, Zhang X, Huang H, Li Y (2016) Secure transmission via jamming in cognitive radio networks with possion spatially distributed eavesdroppers. In: Proceedings of IEEE PIMRC. Valencia, Spain, pp 1–6
Cai Y, Xu X, Yang W (2016) Secure transmission in the random cognitive radio networks with secrecy guard zone and artificial noise. IET Commun. 10(15):1904–1913
Li Z, Jing T, Cheng X, Huo Y, Zhou W, Chen D (2015) Cooperative jamming for secure communications in MIMO cooperative cgnitive radio networks. In: Proceedings of IEEE ICC. London, UK, pp 7609–7614
Liu W, Guo L, Kang T, Zhang J, Lin J (2015) Secure cognitive radio system with cooperative secondary networks. In: Proceedings IEEE ICT. Sydney, Australia, pp 6–10
He T, Chen H, Liu Q (2013) Qos-based beamforming with cooperative jamming in cognitive radio networks. In: Proceedings of ICCCAS. Chengdu, China, pp 42–45
Liu W, Sarkar MZI, Ratnarajah T (2014) On the security of cognitive radio networks: cooperative jamming with relay selection. In: Proceedings of EUCNC. Bologna, Italy, pp 1–5
Liu W, Sarkar MZI, Ratnarajah T, Du H (2017) Securing cognitive radio with a combined approach of beamforming and cooperative jamming. IET Commun 11(1):1–9
Zou Y (2017) Physical-layer security for spectrum sharing systems. IEEE Trans Wire Commun 16(2):1319–1329
Liu Y, Wang L, Duy TT, Elkashlan M, Duong TQ (2015) Relay selection for security enhancement in cognitive relay networks. IEEE Wire Commun Lett 4(1):46–49
Chakraborty P, Prakriya S (2017) Secrecy performance of an idle receiver assisted underlay secondary network. IEEE Trans Veh Tech 66(10):9555–9560
Ho-Van K, Sofotasios PC, Freear S (2014) Underlay cooperative cognitive networks with imperfect Nakagami-m fading channel information and strict transmit power constraint: interference statistics and outage probability analysis. IEEE/KICS Journal of Communications and Networks 16(1):10–17
Biglieri E, Proakis J, Shamai S (1998) Fading channels: information-theoretic and communications aspects. IEEE Trans Inf Theory 44(6):2619–2692
Wyner AD (1975) The wire-tap channel. Bell Syst Tech Journ 54(8):1355–1387
Gradshteyn IS, Ryzhik IM (2000) Table of integrals, series and products, 6th edn. Academic, San Diego
Zou Y, Wang X, Shen W (2013) Physical-layer security with multiuser scheduling in cognitive radio networks. IEEE Trans Commun 61(12):5103–5113
Ahmed N, Khojastepour M, Aazhang B (2004) Outage minimization and optimal power control for the fading relay channel. In: Proceedings of IEEE information theory workshop. San Antonio, pp 458–462
Press WH, Teukolsky SA, Vetterling WT, Flannery BP (1992) Numerical recipes in C: the art of scientific computing, 2nd edn. Cambridge University Press, Cambridge
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.01
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Proof of Lemma 1
The conditional CDF of γd given Es is defined as
Plugging (3) into (43) and performing some algebraic manipulations, one obtains
Due to \({g_{\texttt {tr}}} \sim \mathcal {C}\mathcal {N}\left ({0,{\alpha _{\texttt {tr}}}} \right )\), |gtr|2 follows the exponential distribution. Therefore, its CDF and PDF are respectively given by \({F_{{{\left | {{g_{\texttt {tr}}}} \right |}^{2}}}}\left (x \right ) = 1 - {e^{- x/{\alpha _{\texttt {tr}}}}}\) and \({f_{{{\left | {{g_{\texttt {tr}}}} \right |}^{2}}}}\left (x \right ) = {e^{- x/{\alpha _{\texttt {tr}}}}}/{\alpha _{\texttt {tr}}}\), x ≥ 0. Given this fact, one can simplify Eq. 44 as
Taking the derivative of \({F_{{\gamma _d}}}\left ({\left . x \right |{E_{s}}} \right )\) with respect to x, simplifying the result and using compact notations in Eqs. 23, 24, 25, one obtains \({f_{{\gamma _d}}}\left ({\left . x \right |{E_{s}}} \right ) = \frac {d}{{dx}}{F_{\gamma _{d}}}\left ({\left . x \right |{E_{s}}} \right )\) as exactly shown in Eq. 22, completing the proof.
Appendix B: Proof of Lemma 2
The conditional CDF of γw given Es according to its definition is
Plugging Eq. 4 into Eq. 46 and performing some algebraic manipulations, one obtains
Quantities (κ, μ, ζ) are computed as follows. First of all, κ can be expressed in closed-form as
Imitating the procedure of deriving κ, one can straightforwardly infer that
By inserting Eq. 14 into Eq. 48 and then statistically averaging the result over a random variable |gjp|2, one obtains the exact closed form of ζ as
The first term in Eq. 50 is easily solved as
while the second term is further simplified as
The first integrand in Eq. 52 is easily computed and the second one can be expressed in terms of the Ei(⋅) function, resulting in
Plugging Eqs. 51 and 53 into Eq. 50 and then inserting the result together with Eq. 49 into Eq. 47, one can reduce Eqs. 47 to 26 after using notations in Eqs. 27, 28, 29, 30, 31. This finishes the proof of Lemma 2.
Appendix C: Closed-form representations of some special integrands
Start with the integrand in Eq. 36. By changing variable y = x + b and then applying the definition of the Ei(⋅) function, the closed-form representation of Eq. 36 is
Performing the integral by part to Eq. 37 and then using the result of Eq. 54, the closed-form representation of Eq. 37 is
By using the approximation of the Ei(⋅) function in [36, Eq. (6.3.11)] as \(Ei\left (x \right ) \approx \frac {{{e^x}}}{x}\), one can obtain the closed form of Eq. 38 after some algebraic manipulations as
It is noted that the integrands in the second equality of Eq. 56 are obtained with the help of Eq. 54.
Again using the approximation of the Ei(⋅) function as \(Ei\left (x \right ) \approx \frac {{{e^x}}}{x}\), one can simplify (39) as
Performing the partial fraction decomposition to \(\frac {1}{{{{\left ({x + c} \right )}^{2}}\left ({x + l/g} \right )}}\), one represents (57) in a more compact form as
Finally, exploiting the results in Eqs. 54 and 55, the closed-form representation of Eq. 39 is
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Security Performance Analysis of Underlay Cognitive Networks with Helpful Jammer Under Interference from Primary Transmitter. Mobile Netw Appl 25, 4–15 (2020). https://doi.org/10.1007/s11036-018-1185-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1185-x