Abstract
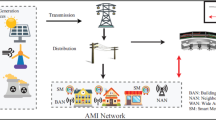
Smart meters provide strong data support for the intelligent construction of power grids but expose users’ privacy-sensitive information to adversaries. Thus, several mechanisms have been proposed for smart meter privacy protection. However, these existing mechanisms either lack consideration of the protection for customer power consumption mode or focus only on data security and ignore the data availability for intelligent services of smart meters. In this study, we propose a temporal perturbation-based privacy-preserving mechanism to achieve a balance between privacy security and data availability. The time disturbance model improves privacy security by staggering the acquisition and release time of smart meter data, destructs the load characteristics hidden in the power waveform, and realizes the fuzzification of real consumption events. Moreover, data availability for metering and billing, electronic scheduling and management, and value-added services is guaranteed. We analyze data availability and privacy security from theoretical and experimental perspectives, deduce a data availability analysis model, and introduce a non-intrusive load monitoring algorithm as a testing method for evaluating security performance. Evaluation results show that the proposed scheme performs well in protecting users’ consumption pattern and is resistant to attacks by load detection; it also ensures data availability when used for intelligent services.















Similar content being viewed by others
References
Fang X, Misra S, Xue G et al (2012) Smart grid — the new and improved power grid: a survey[J]. IEEE Commun Surv Tutor 14(4):944–980
Bayindir R, Hossain E, Vadi S (2016) The path of the smart grid -the new and improved power grid[C]// smart grid workshop and certificate program. IEEE :1–8
Kalogridis G, Cepeda R, Denic SZ et al (2011) ElecPrivacy: evaluating the privacy protection of electricity management algorithms[J]. IEEE Trans Smart Grid 2(4):750–758
Sankar L, Rajagopalan SR, Mohajer S et al (2013) Smart meter privacy: a theoretical framework[J]. IEEE Trans Smart Grid 4(2):837–846
Li X, Liang X, Lu R et al (2012) Securing smart grid: cyber attacks, countermeasures, and challenges[J]. Commun Mag IEEE 50(8):38–45
Asghar MR, Dán G, Miorandi D, et al. (2017) Smart meter data privacy: a survey[J]. IEEE Communications Surveys & Tutorials (99):1–1
Vuković O, Dán G, Bobba RB (2013) Confidentiality-preserving obfuscation for cloud-based power system contingency analysis[C]// IEEE international conference on smart grid communications. IEEE :432–437
Zhang Z, Qin Z, Zhu L, et al. (2017) Cost-friendly differential privacy for smart meters: exploiting the dual roles of the noise[J]. IEEE Transactions on Smart Grid (99):1–1
Kursawe K, Danezis G, Kohlweiss M (2011) Privacy-friendly aggregation for the smart-grid[C]// international conference on privacy enhancing technologies. Springer-Verlag :175–191
Varodayan D, Khisti A (2011) Smart meter privacy using a rechargeable battery: minimizing the rate of information leakage[C]// IEEE international conference on acoustics, speech and signal processing. IEEE :1932–1935
Li S, Khisti A, Mahajan A (2016) Privacy-optimal strategies for smart metering systems with a rechargeable battery[C]// American control conference. IEEE
Backes M, Meiser S (2014) Differentially private smart metering with battery recharging[M]// data privacy management and autonomous spontaneous security. Springer, Berlin Heidelberg, pp 194–212
Dwork C, Mcsherry F, Nissim K (2006) Calibrating noise to sensitivity in private data analysis[M]// theory of cryptography. Springer, Berlin Heidelberg, pp 637–648
Dwork C (2008) Differential privacy: a survey of results[C]// international conference on theory and applications of MODELS of computation. Springer-Verlag :1–19
Ni J, Zhang K, Alharbi K et al. (2017) Differentially private smart metering with fault tolerance and range-based filtering[J]. IEEE Transactions on Smart Grid (99):1–1
Zhao J, Jung T, Wang Y et al. (2014) Achieving differential privacy of data disclosure in the smart grid[C]// IEEE INFOCOM. IEEE, :504–512
Shuai L, Mengye L, Gaocheng L et al (2017) A novel distance metric: generalized relative entropy[J]. Entropy 19(6):269
Acs G, Castelluccia C (2011) I have a DREAM!(differentially private smartmetering)[C]//proceedings of the 13th international conference on information hiding.[s.l.]. Springer, Berlin Heidelberg, pp 118–132
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes[C]// advances in cryptology - EUROCRYPT '99, international conference on the theory and application of cryptographic techniques, Prague, Czech Republic, may 2-6, 1999, proceeding. DBLP :223–238
Lu R, Liang X, Li X et al (2012) EPPA: an efficient and privacy-preserving aggregation scheme for secure smart grid communications[J]. IEEE Trans Parallel Distrib Syst 23(9):1621–1631
Ruj S, Nayak A (2013) A decentralized security framework for data aggregation and access control in smart grids[J]. IEEE Trans Smart Grid 4(1):196–205
Lin HY, Tzeng WG, Shen ST et al. (2012) A practical smart metering system supporting privacy preserving billing and load monitoring[J]
Liu S, Z Pan WF, Cheng* X (2017) Fractal generation method based on asymptote family of generalized Mandelbrot set and its application [J]. J Nonlinear Sci Appl 10(3):1148–1161
Liu S, Fu W, He L et al (2017) Distribution of primary additional errors in fractal encoding method[J]. Multimed Tools Appl 76(4):5787–5802
Beckel C, Kleiminger W, Cicchetti R, et al. (2014) The ECO data set and the performance of non-intrusive load monitoring algorithms[C]// ACM conference on embedded Systems for Energy-Efficient Buildings. ACM :80–89
Zhen X, Jinlong W, Guoru D et al. (2018) Device-to-device communications underlying UAV-supported social networking[J]. IEEE Access:1
Zhang Z, Guo X, Lin Y (2018) Trust management method of D2D communication based on RF fingerprint identification[J]. IEEE Access :1
Batra N, Kelly J, Parson O, et al. (2014) NILMTK:an open source toolkit for non-intrusive load monitoring[C]// international conference on future energy systems. ACM :265–276
Zeifman M, Roth K (2011) Nonintrusive appliance load monitoring: review and outlook[J]. IEEE Trans Consum Electron 57(1):76–84
Lin Y, Zhu X, Zheng Z, et al. (2017) The individual identification method of wireless device based on dimensionality reduction and machine learning[J]. J Supercomput (5):1–18
Tan O, Gunduz D, Poor HV (2013) Increasing smart meter privacy through energy harvesting and storage devices[J]. IEEE J Select Areas Commun 31(7):1331–1341
Fan L, Xiong L (2013) Adaptively sharing real-time aggregate with differential privacy. IEEE Trans Knowledge Data Eng (TKDE) 26(9):2094–2106
Ma X, Wang T, Lin Y et al. (2018) Parallel iterative inter-carrier interference cancellation in underwater acoustic orthogonal frequency division multiplexing[J]. Wirel Pers Commun
Bhotto MZA, Makonin S, Bajic I (2017) Load disaggregation based on aided linear integer programming[J]. IEEE Trans Circ Syst II Express Briefs (99):1
Tu Y, Lin Y, Wang J et al (2015) Semi-supervised learning with generative adversarial networks on digital signal modulation classification[J]. Comput Mater Continua 55(2):243–254
Yun L, Chao W, Jiaxing W et al (2016) A novel dynamic Spectrum access framework based on reinforcement learning for cognitive radio sensor networks[J]. Sensors 16(10):1675
Zoha A, Gluhak et al. (2012) Sensors, Vol. 12, Pages 16838–16866: Non-intrusive load monitoring approaches for disaggregated energy sensing: a survey[J]
Weiss M, Helfenstein A, Mattern F et al Leveraging smart meter data to recognize home appliances[C]// IEEE international conference on pervasive computing and communications. IEEE 2012:190–197
Acknowledgements
The research work reported in this paper is supported by the National Natural Science Foundation of China (41671443, 61701453), Fundamental Research Funds for the Central Universities (2042017kf0044), and LIESMARS Special Research Funding.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, X., Xu, Z., Cai, Z. et al. Novel Temporal Perturbation-Based Privacy-Preserving Mechanism for Smart Meters. Mobile Netw Appl 25, 1548–1562 (2020). https://doi.org/10.1007/s11036-019-01359-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01359-8