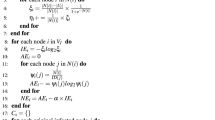Abstract
Nowadays, the spread of Internet rumors and viruses has caused great hidden dangers to the safety of human life. It is particularly important to identify the source of network threat, especially when there are multiple sources in the network. At present, the research on multi-source propagation is mostly based on SI model, but there is little work on multi-source propagation under SIR model. Based on SIR propagation model, this paper proposes a novel PRIA algorithm to locate multiple propagation sources. Firstly, we propose a new partitioning method based on effective distance, which transforms the source problem into a single source problem in multiple partitions. Secondly, we propose a single source algorithm based on SIR propagation model, which uses reverse infection algorithm to locate suspicious sources. Finally, we evaluate our approach in real network topology. The simulation results show that our method can effectively identify the real source and estimate the propagation time. And it has great accuracy in the number of identification sources.








Similar content being viewed by others
References
Xu G, Cao Y, Ren Y, Li X, Feng Z (2017) Network security situation awareness based on semantic ontology and user-defined rules for internet of things. IEEE Access 5:21046–21056. https://doi.org/10.1109/ACCESS.2017.2734681
Pinto PC, Thiran P, Vetterli M (Aug 2012) Locating the source of diffusion in large-scale networks. Phys Rev Lett 109
Shah D, Zaman T (2011) Rumors in a network: Who’s the culprit? IEEE Trans Inf Theory 57:5163–5181
Luo W, Tay WP, Leng M (2013) Identifying infection sources and regions in large networks. Signal Process IEEE Trans 61(11):2850–2865
Zhu K, Ying L (2013) Information source detection in the SIR model: a sample path based approach. In Information Theory and Applications Workshop (ITA), pp 1–9
Karamchandani N, Franceschetti M (2013) Rumor source detection under probabilistic sampling. In Information Theory Proceedings (ISIT), 2013 IEEE International Symposium on, pp 2184–2188
Shah D, Zaman T (2010) Detecting sources of computer viruses in net-works: theory and experiment. In Proc. ACM SIGMETRICS, New York, NY, pp 203–214
Shah D, Zaman T (2011) Rumors in a network: Who’s the culprit? IEEE Trans Inf Theory 57(8):5163–5181
Shah D, Zaman T (2012) Rumor centrality: a universal source detector. In Proc. ACM SIGMETRICS, London, pp 199–210
Easley D, Kleinberg J (2010) Networks, crowds, and markets: Rea-soning about a highly connected world. Cambridge University Press, Cambridge
Brockmann D, Helbing D (2013) The hidden geometry of complex, network-driven contagion phenomena. Science 342(6164):1337–1342
Yang K, Shekhar AH, Oliver D, Shekhar S (2013) Capacity constrained network-voronoi diagram: a summary of results. In: Advances in spatial and temporal databases. Springer, Heidelberg, pp 56–73
Jiang JJ, Wen S, Yu S, Xiang Y, Zhou W (2015) K-Center: An Approach on the Multi-Source Identification of Information Diffusion. IEEE Trans Inf Forensics Secur 10(12):2616–2626
Leskovec J, Kleinberg J, Faloutsos C (Mar 2007) Graph evolution:Densification and shrinking diameters. ACM Trans Knowl Discov Data 1(1):2
Viswanath B, Mislove A, Cha M, Gummadi KP (2009) On the evolution of user interaction in facebook. In Proceedings of the 2nd ACM workshop on online social networks, pp 37–42
Bakshy E, Hofman JM, Mason WA, Watts DJ (2011) Everyone’s an influencer: quantifying influence on Twitter. In Proc. ACM Int Conf Web Search Data Min, pp 65–74
Aral S, Walker D (2012) Identifying influential and susceptible members of social networks. Science 337(6092):337–341
Tay WP (2012) The value of feedback in decentralized detection. IEEE Trans Inf Theory 58(12):7226–7239
Fioriti V, Chinnici M, Palomo J (2014) Predicting the sources of an outbreak with a spectral technique. Appl Math Sci 8(135):6775–6782
Restrepo JG, Ott E, Hunt BR (2006) Characterizing the dynamical importance of network nodes and links. Phys Rev Lett 97:094102
Luo W, Tay WP, Leng M (2013) Identifying infection sources and regions in large networks. Signal Process IEEE Trans 61(11):2850–2865
Hakimi SL, Labb’e ML, Schmeichel E (1992) The voronoi partition of a network and its implications in location theory. ORSA J Comput 4(4):412–417
Lokhov AY, Mézard M, Ohta H, Zdeborová L (2013) Inferring the origin of an epidemy with dynamic message-passing algorithm. arXiv preprint arXiv:1303.5315
Karrer B, Newman MEJ (2010) Message passing approach for general epidemic models. Phys Rev E 82:016101
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ding, Y., Cui, X., Wang, H. et al. PRIA: a Multi-source Recognition Method Based on Partial Observation in SIR Model. Mobile Netw Appl 26, 1514–1522 (2021). https://doi.org/10.1007/s11036-019-01487-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01487-1