Abstract
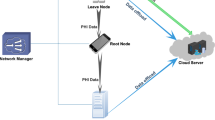
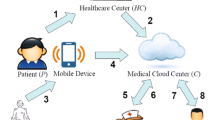
Wearable electronic equipments and wireless communications provide convenience to the patients. Wireless body area network has entered our lives, helping in making medical diagnosis. Despite various benefits brought by wireless body area network, some security challenges still restrict its application, like identity protection and mutual authentication. Certificateless authentication is a good solution to solve these issues. Recently, it has been seen that several authentication schemes that can get rid of restricts from security challenges. In this paper, we find security risks in a cloud-assisted authentication protocol and design a new anonymous certificateless authentication scheme based on the issue. The scheme can ensure secure and communication between the wearable devices and the cloud server. As for the security of the protocol, we give a description of security attributes and a security proof. Finally, the performance analysis of the scheme is shown at the end of the paper.






Similar content being viewed by others
References
Bellare M, Pointcheval D, Rogaway P (2000) Authenticated key exchange secure against dictionary attacks. In: Advances in Cryptology - EUROCRYPT 2000. Springer, pp 139–155
Bonneau J, Herley C, Oorschot P, Stajano F (2012) The quest to replace passwords: A framework for comparative evaluation of web authentication schemes
Chatterjee S, Das AK, Sing JK (2014) A novel and efficient user access control scheme for wireless body area sensor networks. Journal of King Saud University - Computer and Information Sciences 26:181–201
Chen R, Peng D (2019) Analysis and improvement of a mutual authentication scheme for wireless body area networks. J Med Sys 43(2):19:1–19:10
Das AK, Chatterjee S, Sing JK (2015) A new biometric-based remote user authentication scheme in hierarchical wireless body area sensor networks. Ad Hoc and Sensor Wireless Networks 28(3-4):221–256
Elgamal T (1985) A public-key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans Inf Theory 31(4):469–472
He D, Wang D (2015) Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J 9(3):816–823
He D, Zeadally S, Kumari N, Lee J (2017) Anonymous authentication for wireless body area networks with provable security. IEEE Syst J 11(4):2590–2601
Huang X, Xiang Y, Bertino E, Zhou J (2014) Robust multi-factor authentication for fragile communications. IEEE Trans Dependable Secure Comput 11(6):568–581
Huang X, Xiang Y, Chonka A, Zhou J, Deng R (2011) A generic framework for three-factor authentication: preserving security and privacy in distributed systems. IEEE Trans Parallel Distrib Sys 22(8):1390–1397
Ibrahim MH, Kumari S, Das AK, Wazid M, Odelu V (2016) Secure anonymous mutual authentication for star two-tier wireless body area networks. Comput Methods Programs Biomed 135:37–50
Jiang Q, Lian X, Wang C, Ma J, Tian Y, Yang Y (2016) A bilinear pairing based anonymous authentication scheme in wireless body area networks for mHealth. J Med Sys 40(11):231:1–231:10
Kumar M, Chand S (2020) A lightweight cloud-assisted identity-based anonymous authentication and key agreement protocol for secure wireless body area network. IEEE Systems Journal
Li X, Peng J, Kumari S, Wu F, Karuppiah M, Choo KR (2017) An enhanced 1-round authentication protocol for wireless body area networks. Comput Electr Eng 61:238–249
Liu B, Yan Z, Chen C (2013) Mac protocol in wireless body area networks for e-health Challenges and a context-aware design. IEEE Wirel Commun 20(4):64–72
Liu J, Zhang Z, Chen X, Kwak KS (2014) Certificateless remote anonymous authentication schemes for wirelessbody area networks. IEEE Trans Parallel Distrib Sys 25(2):332–342
Liu X, Jin C, Li F (2018) An improved two-layer authentication scheme for wireless body area networks. J Med Sys 42(8):143:1–143:14
Liu Y, Liang Y, Wu Y, Nie X (2020) Revisit of certificateless signature scheme used to remote authentication schemes for wireless body area networks. IEEE Internet Things J 7(3):2160–2168
Qiu S, Wang D, Xu G, Kunari S (2020) Practical and provably secure three-factor authentication protocol based on extended chaotic-maps for mobile lightweight devices. IEEE Transactions on Dependable and Secure Computing
Rivest R, Shamir A, Adleman LM (1978) A method for obtaining digital signatures and public-key cryptosystems. Commun ACM 21(2):120–126
Shamir A (1984) Identity-based cryptosystems and signature schemes
Shen J, Chang S, Shen J, Liu Q, Sun X (2016) A lightweight multi-layer authentication protocol for wireless body area networks. Futur Gener Comput Syst 78:956–963
Shen J, Gui Z, Ji S, Shen J, Tan H, Tang Y (2018) Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. J Netw Comput Appl 106:117–123
Shuai M, Lui B, Yu N, Xiong L, Wang C (2020) Efficient and privacy-preserving authentication scheme for wireless body area networks. J Inf Secur Appl 52:102499:1–102499:10
Sowjanya K, Dasgupta M, Ray S (2020) An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems. Int J Inf Secur 19(1):129–146
Wang C, Zhang Y (2015) New authentication scheme for wireless body area networks using the bilinear pairing. J Med Sys 39(11):136:1–136:8
Wang D, Cheng H, He D, Wang P (2018) On the challenges in designing identity-based privacy-preserving authentication schemes for mobile devices. IEEE Syst J 12(1):916– 925
Wang D, Li W, Wang P (2018) Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans Industr Inform 14(9):4081– 4092
Wang D, stone P. Wang. (2018) Two birds with one Two-factor authentication with security beyond conventional bound. IEEE Trans Dependable Secure Comput 15(4):708–722
Wazid M, Das AK, Vasilakos A (2018) Authenticated key management protocol for cloud-assisted body area sensor networks. J Netw Comput Appl 123:112–126
Wu L, Zhang Y, Li L, Shen J (2016) Efficient and anonymous authentication scheme for wireless body area networks. J Med Sys 40(6):134:1–134:12
Xiong H (2014) Cost-effective scalable and anonymous certificateless remote authentication protocol. IEEE Trans Inf Forensics Secur 9(12):2327–2339
Xiong H, Qin Z (2015) Revocable and scalable certificateless remote authentication protocol with anonymity for wireless body area networks. IEEE Trans Inf Forensics Secur 10(7):1442– 1455
Zhao Z (2014) An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J Med Syst 38(2):13–20
Zimmerman T (1996) Personal area networks: Near-field intrabody communication. IBM Syst J 35(3):609–617
Acknowledgment
This work was supported by the National Natural Science Foundation of China (Grant Nos. 61872449, U1708262, U1736203, 62072093).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Cheng, Q., Li, Y., Shi, W. et al. A Certificateless Authentication and Key Agreement Scheme for Secure Cloud-assisted Wireless Body Area Network. Mobile Netw Appl 27, 346–356 (2022). https://doi.org/10.1007/s11036-021-01840-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-021-01840-3