Abstract
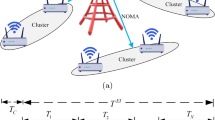
In this paper, we study the physical layer security (PLS) of a radio frequency energy harvesting (RF EH) non-orthogonal multiple access (NOMA) relaying network where relay-user selection scheme and secrecy performance optimization are investigated. Specifically, we consider a scenario, where the energy-constrained users from two different user clusters harvest RF energy from the selected relay to transmit their messages to a destination with the help of a relay cluster in the presence of a passive eavesdropper. To enhance the PLS performance of the considered system, we propose a relay and user selection scheme and an optimal algorithm to find the best system parameter set including time switching ratio and power allocation ratio, which can bring the best secrecy performance for the system. Accordingly, to evaluate the secrecy performance, the closed-form expressions of secrecy outage probability are derived. Moreover, the impacts of the network parameters on the secrecy performance are investigated to achieve more insight into the behavior of NOMA relaying network with RF EH. Finally, the accuracy of our analysis is verified by Monte-Carlo simulation results.











Similar content being viewed by others
References
Ding Z, Liu Y, Choi J, Sun Q, Elkashlan M, Chih-Lin I, Poor HV (2017) Application of non-orthogonal multiple access in lte and 5g networks. IEEE Commun Mag 55(2):185–191
Akpakwu GA, Silva BJ, Hancke GP, Abu-Mahfouz AM (2017) A survey on 5g networks for the internet of things: Communication technologies and challenges. IEEE access 6:3619–3647
Kabalci Y (2019) 5g mobile communication systems: Fundamentals, challenges, and key technologies. In: Smart grids and their communication systems. Springer, pp 329–359
Ullah Z, Al-Turjman F, Mostarda L (2020) Cognition in uav-aided 5g and beyond communications: a survey. IEEE Trans Cogn Commun Netw 6(3):872–891
Fourati H, Maaloul R, Chaari L (2021) A survey of 5g network systems: challenges and machine learning approaches. Int J Mach Learn Cybern 12(2):385–431
Makki B, Chitti K, Behravan A, Alouini MS (2020) A survey of noma: Current status and open research challenges. IEEE Open J Commun Soc 1:179–189
Chen Z, Ding Z, Dai X, Zhang R (2017) An optimization perspective of the superiority of noma compared to conventional oma. IEEE Trans Signal Process 65(19):5191–5202
Liu Y, Pan G, Zhang H, Song M (2016) On the capacity comparison between mimo-noma and mimo-oma. IEEE Access 4:2123–2129
Wei Z, Guo J, Ng DWK, Yuan J (2017) Fairness comparison of uplink noma and oma. In: 2017 IEEE 85th vehicular technology conference (VTC Spring). IEEE, pp 1–6
Vaezi M, Baduge GAA, Liu Y, Arafa A, Fang F, Ding Z (2019) Interplay between noma and other emerging technologies: a survey. IEEE Trans Cogn Commun Netw 5(4):900–919
Tran DD, Ha DB, So-In C, Tran H, Nguyen TG, Baig ZA, Sanguanpong S, et al. (2018) Performance analysis of df/af cooperative miso wireless sensor networks with noma and swipt over nakagami-m fading. IEEE access 6:56142–56161
Rauniyar A, Engelstad PE, Østerbø ON (2020) On the performance of bidirectional noma-swipt enabled iot relay networks. IEEE Sensors J 21(2):2299–2315
Lu X, Wang P, Niyato D, Kim DI, Han Z (2014) Wireless networks with RF energy harvesting: a contemporary survey. IEEE Commun Surv Tutor 17(2):757–789
Ha DB, Tran DD, Tran-Ha V, Hong EK (2015) Performance of amplify-and-forward relaying with wireless power transfer over dissimilar channels. Elektronika ir Elektrotechnika J 21(5):90–95
Al-kahtani MS, Ferdouse L, Karim L (2020) Energy efficient power domain non-orthogonal multiple access based cellular device-to-device communication for 5g networks. Electronics 9(2):237
Ha DB, Nguyen QS (2017) Outage performance of energy harvesting DF relaying NOMA networks. Mobile Networks and Applications
Truong VT, Ha DB (2020) Secured scheme for rf energy harvesting mobile edge computing networks based on noma and access point selection. In: 2020 7th NAFOSTED conference on information and computer science (NICS) (IEEE), pp 7–12
Truong VT, Ha DB, Lee Y, Nguyen AN (2020) On performance of cooperative transmission in uplink non-orthogonal multiple access wireless sensor networks. In: 2020 4th International conference on recent advances in signal processing, telecommunications & computing (SigTelCom) (IEEE), pp 56–60
Ha DB, Nguyen SQ, Nguyen HT (2019) Cooperative cognitive non-orthgonal multiple access under unreliable backhaul connections. Mobile Netw Appl 24(2):596–617
Duy TT, Ngoc PTD, Tran PT (2021) Performance enhancement for multihop cognitive df and af relaying protocols under joint impact of interference and hardware noises: Noma for primary network and best-path selection for secondary network. Wirel Commun Mob Comput
Son PN, Duy TT (2020) A new approach for two-way relaying networks: improving performance by successive interference cancellation, digital network coding and opportunistic relay selection. Wirel Netw 26 (2):1315–1329
Sheng Z, Tuan HD, Duong TQ, Poor HV, Fang Y (2018) Low-latency multiuser two-way wireless relaying for spectral and energy efficiencies. IEEE Trans Signal Process 66(16):4362–4376
Nguyen VL, Ha DB, Tran DD, Lee Y (2019) Enhancing physical layer security for cooperative non-orthogonal multiple access networks with artificial noise. EAI Endorsed Trans Indust Netw Intellig Syst 6(20):e4
Yu H, Lee IG (2020) Physical layer security based on noma and aj for misose channels with an untrusted relay. Futur Gener Comput Syst 102:611–618
Le TA, Kong H (2019) Secrecy analysis of a cooperative noma network using an eh untrusted relay. Int J Electron 106(6):799–815
Lei H, Yang Z, Park KH, Ansari IS, Guo Y, Pan G, Alouini MS (2018) Secrecy outage analysis for cooperative noma systems with relay selection scheme. arXiv:1811.03220
Kieu TN, Tran DD, Ha DB, Voznak M (2019) Secrecy performance analysis of cooperative miso noma networks over nakagami-m fading. IETE J Res, 1–12
Guo C, Zhao L, Feng C, Ding Z, Wang HM (2020) Secrecy performance of noma systems with energy harvesting and full-duplex relaying. IEEE Trans Veh Technol 69(10):12301–12305
Xie X, Li M, Shi Z, Tang H, Huang Q (2021) User selection and dynamic power allocation in the swipt-noma relay system. EURASIP J Wirel Commun Netw 2021(1):1–19
Li D, Shen C, Qiu Z (2013) Two-way relay beamforming for sum-rate maximization and energy harvesting. In: 2013 IEEE International conference on communications (ICC) (IEEE), pp 3115–3120
Chen J, Yang L, Alouini MS (2018) Physical layer security for cooperative noma systems. IEEE Trans Veh Technol 67(5):4645–4649
Zaghdoud N, Alouane WH, Boujemaa H, Touati F (2019) Secure performance of af and df relaying in cooperative noma systems. In: 2019 19th International conference on sciences and techniques of automatic control and computer engineering (STA) (IEEE), pp 614–619
Anh L, Kong H (2020) Secrecy performance of an uplink-downlink cooperative pd-noma df network in pls. Int J Electron 107(11):1861–1886
Garcia CE, Camana MR, Koo I (2020) Particle swarm optimization-based secure computation efficiency maximization in a power beacon-assisted wireless-powered mobile edge computing noma system. Energies (19961073), 13(21)
Masaracchia A, Da Costa DB, Duong TQ, Nguyen MN, Nguyen MT (2019) A pso-based approach for user-pairing schemes in noma systems: Theory and applications. IEEE Access 7:90550–90564
Marini F, Walczak B (2015) Particle swarm optimization (pso). a tutorial. Chemometr Intell Lab Syst 149:153–165
Bao VNQ, Linh-Trung N, Debbah M (2013) Relay selection schemes for dual-hop networks under security constraints with multiple eavesdroppers. IEEE Trans Wireless Commun 12(12):6076–6085
Zhao S, Zhang Q, Meng Q, Wang L (2014) Optimum power allocation for relay network based on artificial noise. J Inf Comput Sci 11(16):5863–5870
Jameel F, Wyne S, Kaddoum G, Duong TQ (2018) A comprehensive survey on cooperative relaying and jamming strategies for physical layer security. IEEE Commun Surv Tutor 21(3):2734–2771
Alsmadi MM, Ali NA, Hayajneh M, Ikki SS (2020) Down-link noma networks in the presence of iqi and imperfect sic: Receiver design and performance analysis. IEEE Trans Veh Technol 69(6):6793–6797
Liu Y, Qin Z, Elkashlan M, Gao Y, Hanzo L (2017) Enhancing the physical layer security of non-orthogonal multiple access in large-scale networks. IEEE Trans Wirel Commun 16(3):1656–1672
Le Anh T, Hong IP (2020) Secrecy performance of a multi-noma-mimo system in the ueh relaying network using the pso algorithm. IEEE Access 9:2317–2331
Kennedy J, Eberhart R (1995) Particle swarm optimization. In: Proceedings of ICNN’95-international conference on neural networks (IEEE), vol 4, pp 1942–1948
Eberhart RC, Shi Y (2000) Comparing inertia weights and constriction factors in particle swarm optimization. In: Proceedings of the 2000 congress on evolutionary computation. CEC00 (Cat No. 00TH8512) (IEEE), vol 1, pp 84–88
Clerc M, Kennedy J (2002) The particle swarm-explosion, stability, and convergence in a multidimensional complex space. IEEE Trans Evol Comput 6(1):58–73
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Proof of Lemma 1
Here, from Eq. 34 we derive the closed-form expression of \(P^{A}_{out}\) as follows.
where \(a_{1}=\frac {(1-\rho _{0})\gamma ^{A}_{th}}{\rho _{0}}\), \(b_{1}=\frac {\gamma ^{A}_{th}}{\rho _{0} \beta \gamma _{0}}\), \(\phi _{q}=\cos \limits \left (\frac {2q-1}{2Q}\pi \right )\), \(\theta _{q}=\frac {\phi _{q}+1}{2}\). Note that step (a) is obtained by applying the Gaussian-Chebyshev quadrature method with Q are the complexity-vs-accuracy trade-off coefficients. This ends our proof.
Appendix B: Proof of Lemma 3
Here, we derive the closed-form expression of \({P^{A}_{s}}\) as follows.
where
\(c_{1} = \frac {\rho _{1}+\rho _{2}(1-2^{{R^{A}_{s}}})}{\rho _{2} 2^{{R^{A}_{s}}}}\), \(c_{2} = \frac {\rho _{1}}{\rho _{2}+\rho _{3}}\), \(c=\min \limits \{c_{1},c_{2}\}\), \(\phi _{q}=\cos \limits \left (\frac {2q-1}{2Q}\pi \right )\), \(\theta _{q}=\frac {(\phi _{q}+1)c}{2}\). Note that step (b) is obtained by applying the Gaussian-Chebyshev quadrature method with Q are the complexity-vs-accuracy trade-off coefficients. This concludes our proof.
Rights and permissions
About this article
Cite this article
Nguyen, VL., Ha, DB., Truong, VT. et al. Secure Communication for RF Energy Harvesting NOMA Relaying Networks with Relay-User Selection Scheme and Optimization. Mobile Netw Appl 27, 1719–1733 (2022). https://doi.org/10.1007/s11036-022-01929-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-022-01929-3