Abstract
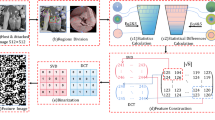
In this paper, a new yet simple reference logo watermarking scheme based on fractional Fourier transform (FrFT) and singular value decomposition (SVD) is proposed. The core idea of the proposed scheme is to segment host image into non-overlapping blocks by the means of Hilbert space filling curve and a reference image is formed by considering Human visual system (HVS). First, reference image is transformed into FrFT domain and embedding is done by modifying singular values of the reference image using singular values of watermark. After embedding, modified reference image is segmented into blocks and these modified blocks are mapped into their original places for constructing watermarked image. For extraction, a reliable watermark extraction scheme is proposed. The experimental results demonstrate better visual imperceptibility and resiliency of the proposed scheme against intentional or un-intentional variety of attacks.

















Similar content being viewed by others
References
Barni M, Bartiloni F, Piva A (2001) Improved wavelet based watermarking through pixel wise masking. IEEE Trans Image Process 10(5):783–791
Barni M, Bartolini F, Cappellini V, Piva A (1998) A DCT-domain system for robust image watermarking. Signal Process 66(3):357–372
Chandra DVS (2002) Digital image watermarking using singular value decomposition. In: Proceeding of midwest sym. on circuits and systems, Tulsa, Oklahoma, USA, vol 3, pp 264–267
Chandan C, Kutay M, Ozaktas HM (2000) The discrete fractional Fourier transform. IEEE Trans Signal Process 48(5):1329–1337
Chang CC, Tsai P, Lin CC (2005) SVD-based digital image watermarking scheme. Pattern Recogn Lett 26(10):1577–1586
Cox IJ, Miller ML, Bloom JA (2001) Digital watermarking. Morgan Kaufmann, San Francisco
Djurovic I, Stankovic S, Pitas I (2001) Digital watermarking in the fractional Fourier transformation domain. J Netw Comput Appl 24(4):167–173
Egiazarian K, Astola J, Ponomarenko N, Lukin V, Battisti F, Carli M (2006) New full-reference quality metrics based on HVS. In: Proceedings of int. workshop on video processing and quality metrics, Scottsdale, USA
Feng Z, Xiaomin M, Shouyi Y (2005) Multiple-chirp typed blind watermarking algorithm based on fractional Fourier transform. In: Proceedings of int. sym. on intelligent signal processing and communication systems, Hong Kong, pp 141–144
Ganic E, Eskicioglu AM (2005) Robust embedding of visual watermarks using DWT-SVD. J Electron Imaging 14(4):043004
Ganic E, Zubair N, Eskicioglu AM (2003) An optimal watermarking scheme based on singular value decomposition. In: Proceeding of IASTED int. conf. on communication, network, and information security, Uniondale, NY, pp 85–90
Hernandez JR, Amado M, Perez-Gonzalez F (2000) DCT-domain watermarking techniques for still images: detector performance analysis and a new structure. IEEE Trans Image Process 9(1):55–68
Hsia SC, Jou IC, Hwang SM (2002) A gray level watermarking algorithm using double layer hidden apporach. IEICE Trans Fundam E85-A(2):463–471
Huang JW, Shi YQ, Dai XH (1999) A segmentation-based image coding algorithm using the features of human vision system. J Image Graph 4(5):400–404
Hwang MS, Chang CC, Hwang KF (1999) A watermarking technique based on one-way hash functions. IEEE Trans Consum Electron 45(2):286–294
Katzenseisser S, Petitcolas F (2000) Information hiding techniques for steganography and digital watermarking. Artech House, Boston
Kundur D, Hatzinakos D (2004) Towards robust logo watermarking using multiresolution image fusion. IEEE Trans Multimedia 6(1):185–197
Lee YK, Chen LH (2000) High capacity image steganographic model. In: IEE proceedings of vision, image and signal processing, vol 147, pp 288–294
Li M, Cai W, Tan Z (2002) A region-based multi-sensor image fusion scheme using pulse-coupled neural network. Pattern Recogn Lett 27(16):1948–1956
Li Q, Yuan C, Zong YZ (2007) Adaptive DWT-SVD domain image watermarking using human visual model. In: Proceeding of int. conf. on advanced communication technology, Phoenix Park, Korea, pp 1947–1951
Lin W-H, Wang Y-R, Horng S-J (2009) A wavelet-tree-based watermarking method using distance vector of binary cluster. Expert Syst Appl 36(6):9869–9878
Lin W-H, Wang Y-R, Horng S-J, Pan Y (2009) A blind watermarking method using maximum wavelet coefficient quantization. Expert Syst Appl 36(9):11509–11516
Lin WH, Horng SJ, Kao TW, P. Fan, Lee CL, Pan Y (2008) An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Trans Multimedia 10(5):746–757
Lin W-H, Horng S-J, Kao T-W, Chen R-J, Chen Y-H, Lee C-L, Terano T (2009) Image copyright protection with forward error correction. Expert Syst Appl 36(9):11888–11894
Liu X (2004) Four alternative patterns of the Hilbert curve. Appl Math Comput 147(3):675–685
Liu R, Tan T (2002) An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans Multimedia 4(1):121–128
Liu JL, Lou DC, Chang MC, Tso HK (2006) A robust watermarking scheme using self-reference image. Comput Stand Interfaces 28(3):356–367
McBride AC, Kerr FH (1987) On Namias’s fractional Fourier transforms. IMA J Appl Math 39(2):159–175
Mooney A, Keating JG, Pitas I (2008) A comparative study of chaotic and white noise signals in digital watermarking. J Chaos Solitons Fractals 35(5):913–921
Moon B, Jagadish HV, Faloutsos C, Saltz JH (2001) Analysis of the clustering properties of the Hilbert space-filling curve. IEEE Trans Knowl Data Eng 13(1):124–141
Namias V (1980) The fractional order Fourier transform and its application to quantum mechanics. IMA J Appl Math 25(3):241–265
Ozaktas HM, Zalevsky Z, Kutay M (2001) The fractional Fourier transform. Wiley, New York
Pei SC, Yeh MH (1998) Two dimensional discrete fractional Fourier transform. Signal Process 67(1):99–108
Pereira S, Voloshynovskiy S, Pun T (2000) Effective channel coding for DCT watermarks. In: Proceeding of IEEE int. conf. on image processing, Vancouver, BC, Canada, vol 3, pp 671–673
Pereira S, O Ruanaidh JJK, Deguillaume F, Csurka G, Pun T (1999) Template based recovery of Fourier-based watermarks using log-polar and log-log maps. In: Proceeding of IEEE int. conf. on multimedia computing and systems, Florence, Italy, vol 1, pp 870–874
Ramkumar M, Akansu AN, Alatan AA (1999) A robust data hiding scheme for images using DFT. In: Proceedings of int. conf. on image processing, vol 2. Kobe, Japan, pp 211–215
Rose NJ (2001) Hilbert-type space-filling curves. http://www4.ncsu.edu/~njrose/pdfFiles/HilbertCurve.pdf
Sagan H (1994) Space-filling curves. Springer, New York
Schyndle RGV, Tirkel AZ, Osbrone CF (1994) A digital watermark. In: Proc. of IEEE int. conf. on image processing, Austin, Texas, USA, vol 2, pp 86–90
Strang G (1993) Introduction to linear algebra. Wellesley-Cambridge Press, Wellesley
Wang Y, Doherty JF, Van-Dyck RE (2002) A wavelet based watermarking algorithm for ownership verification of digital images. IEEE Trans Image Process 11(2):77–88
Yu FQ, Zhangi ZK, Xu MH (2006) A digital watermarking algorithm for image based on fractional Fourier transform. In: Proceeding of ieee conf. on industrial electronics and applications, Singapore, pp 1–5
Acknowledgements
One of the authors, Gaurav Bhatnagar, gratefully acknowledges the financial support of the Council of Scientific and Industrial Research, New Delhi, India through his Senior Research Fellowship (SRF) scheme (CSIR Award no.: 09/143(0559)/2006-EMR-I) for his research work.
Last but not least, the authors thank the anonymous Referees and the Editor for their valuable suggestions and many constructive comments that resulted in the improvement and readability of this paper.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Bhatnagar, G., Raman, B. A new robust reference logo watermarking scheme. Multimed Tools Appl 52, 621–640 (2011). https://doi.org/10.1007/s11042-009-0433-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-009-0433-2