Abstract
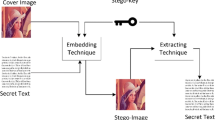
Embedding of confidential data in the least significant bit of an image is still an attractive method of steganography. Utilizing the full capacity of cover images by embedding one bit of data per pixel, using methods such as LSB flipping or LSB matching, usually decreases the security, making the algorithm vulnerable to steganalytic attacks. In this paper, we propose a novel efficient high payload ±1 steganographic method based on a special two variable binary function. This function uses the information of the least two significant bit planes of the cover image for the embedding and extraction purposes. Embedding efficiency, defined as the number of embeddable bits per one change in the cover medium, is a good criterion for concurrent evaluation of the capacity and security. Rather than randomly selecting +1 or −1, we achieve higher embedding efficiencies by choosing the correct modification component. In the generalized form of the proposed method, n bits of data are embedded in n pixels of the cover medium, by causing one unit change in only one third of these pixels. Analytical and experimental results demonstrated that the proposed method provides higher embedding efficiency than the other LSB embedding schemes. The proposed method is also applicable to other digital cover media.



Similar content being viewed by others
References
Anderson RJ, Petitcolas FAP (1998) On the limits of steganography. IEEE J Sel Areas Commun 16(4):474–481
Available: http://decsai.ugr.es/cvg/CG/base.htm
Bierbrauer J (1998) Crandall’s problem. Available: http://www.ws.binghamton.edu/fridrich/covcodes.pdf
Bierbrauer J, Fridrich J (2008) Constructing good covering codes for applications in steganography. LNCS Transactions on Data Hiding and Multimedia Security, Springer-Verlag 4920:1–22
Crandall R (1998) Some notes on steganography. Available: http://os.inf.tu-dresden.de/∼westfeld/crandall.pdf
Dijk M, Willems F (2001) Embedding information in gray-scale images. in Proc. 22nd Symp. Information Theory Benelux pp 147–154
Dumitrescu S, Wu X, Wang Z (2003) Detection of LSB steganography via sample pair analysis. IEEE Trans Signal Process 51(7):1995–2007
Fridrich J, Goljan M (2002) Practical steganalysis of digital images-state of the art. in Proc. SPIE Security Watermarking Multimedia Contents, 4675:1–13
Fridrich J, Goljan M, Dui R (2001) Reliable detection of LSB steganography in color and gray-scale images. Proc. of the ACM Workshop on Multimedia and Security, Ottawa, CA, October 5, pp 27–30
Fridrich J, Lisonek P, Soukal D (2008) On steganographic embedding efficiency. in Proc. Information Hiding Workshop, vol. 4437, Springer LNCS, pp 282–296
Fridrich J, Soukal D (2006) Matrix embedding for large payloads. IEEE Transaction on Information Forensics and Security 1(3):390–395
Harmsen JJ (2003) Steganalysis of additive noise modelable information hiding. MS Thesis, Rensselaer Polytechnic Institute, Troy, New York, April
Ker A (2004) Improved detection of LSB steganography in gray-scale images. in Proc. Information Hiding Workshop, vol. 3200, Springer LNCS, pp 97–115
Ker A (2005) Steganalysis of LSB matching in gray-scale images. IEEE Signal Process Lett 12(6):441–444
Khatirinejad M, P Lisonˇek (2008) Linear codes for high payload steganography. Discrete Appl Math. doi:10.1016/j.dam.2008.02.004
Lin WH, Horng SJ, Kao TW, Chen RJ, Chen YH, Lee CL, Terano T (2009) Image copyright protection with forward error correction. Expert Systems Appl 36(9):11888–11894
Lin WH, Horng SJ, Kao TW, Fan P, Lee CL, Pan Y (2008) An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Trans Multimedia 10(5):746–757
Mielikainen J (2006) LSB matching revisited. IEEE Signal Process Lett 13(5):285–287
NRCS Photo Gallery Home, United State Department of Agriculture, available: http://photogallery.nrcs.usda.gov
Petitcolas FAP, Anderson RJ, Kuhn MG (1999) Information hiding—a survey. Proc IEEE, special issue on protection of multimedia content 87(7):1062–1078
Westfeld A (2001) F5__ A steganographic algorithm: high capacity despite better steganalysis. in Proc. Information Hiding Workshop, vol. 2137, Springer LNCS, pp 289–302
Westfeld A, Pfitzman A (1999) Attacks on steganographic systems. in Proc. Information Hiding Workshop, Springer-Verlag, pp 61–76
Zhang X, Wang S (2006) Efficient steganographic embedding by exploiting modification direction. IEEE Commun Lett 10(11):781–783
Zhang W, Wang S, Zhang X (2007) Improving embedding efficiency of covering codes for applications in steganography. IEEE Commun Lett 11(8):680–682
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Omoomi, M., Samavi, S. & Dumitrescu, S. An efficient high payload ±1 data embedding scheme. Multimed Tools Appl 54, 201–218 (2011). https://doi.org/10.1007/s11042-010-0517-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-010-0517-z