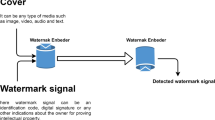
Abstract
In this paper, we present a new digital watermarking scheme for ownership protection. The algorithm embeds the watermark in the Schur decomposition components of the cover image. We also show that this algorithm is noninvertible. Comparisons with other algorithms indicate that the proposed algorithm is robust against most common attacks including geometrical distortions and jpeg compression attacks. Simulations show that the performance of this algorithm outperforms the closely related singular value decomposition based algorithms. More specifically, the proposed algorithm is more robust and requires less number of computations. In addition, our algorithm does not suffer the false positive detection problem inherent in SVD based algorithms.































Similar content being viewed by others
References
Agreste S, Andaloro G (2008) A new approach to pre-processing digital image for wavelet-based transform. J Comput Appl Math 221(2):274–283
Aldaheri RW (1991) Model order reduction via real Schur-form decomposition. Int J Control 53(3):709–716
Aldaheri RW (2004) Design of 2-D linear phase digital filters using Schur decomposition and symmetries. Multidim Syst Signal Process 15(1):65–81
Alturki FT, Almutairi A, Mersereauu RM (2007) Analysis of blind data hiding using discrete cosine transform phase modulation. Signal Process Image Commun 22(4):347–362
Amirgholipour SK, Naghsh-Nilchi AR (2009) Robust digital image watermarking based on joint DWT-DCT. IEEE Trans Image Process 3(2):42–54
Andrews H, Patterson C (1976) Singular value decompositions and digital image processing. IEEE Trans Acoust Speech Signal Process 24(1):26–53
Aslantas V (2008) A singular value decomposition based image watermarking using genetic algorithm. AEU Int J Electron Commun 62(5):386–394
Aslantas V (2009) An optimal robust digital image watermarking based on SVD using differential evolution algorithm. Opt Commun 282(5):769–777
Bhatnagar B, Balasubramanian R (2009) A new robust reference watermarking scheme based on DWT-SVD. Comput Stand Interfaces 31(5):1002–1013
Chan C, Cheng L (2004) Hiding data in images by simple LSB substitution. Pattern Recognit 37(3):469–474
Chandra DV (2002) Digital image watermarking using singular value decomposition. In: Proc. 45th IEEE Midwest Symposium on Circuits and Systems, Tulsa, OK, pp 264–267
Chandra B, Srinivas S (2008) A robust watermarking scheme using nonnegative matrix factorization and wavelet transform. Journal of Multimedia 3(1):7–15
Chang C, Lin C, Hu Y (2007) An SVD oriented watermark-embedding scheme with high qualities for the restored images. International Journal of Innovative Computing, Information and Control 3(3):609–620
Chang CC, Lin CC, Tseng CS, Tai WL (2007) Reversible hiding DCT-based compressed images. Inf Sci 177(13):2768–2786
Cheung CM, Lei CU, Ngai Wong N (2007) Design of 2D linear-phase IIR filters via Schur decomposition and discrete-time vector fitting, pp. 2403–2406
Chu WC (2003) DCT based image watermarking using subsampling. IEEE Trans Multimedia 5(1):34–38
Cox IJ, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Cruces S, Cichocki A (2003) Combining blind source extraction with joint approximate diagonalization: thin algorithms for ICA. In: Proc. of the4th International Symposium on Independent Component Analysis and Blind Signal Separation (ICA2003), Kyoto, Japan, pp 464–468
Cruces S, Cichocki A, Lathauwer L (2004) Thin QR and SVD factorizations for simultaneous blind signal extraction. In: Proc. of the European Signal Processing Conference (EUSIPCO), Vienna, Austria, pp 217–220
Dong P, Brankov JG, Galatsanos NP, Yang Y, Davoine F (2005) Digital watermarking robust to geometric distortions. IEEE Trans Image Process 14(12):2140–2150
Ganic E, Eskicioglu A (2004) Robust DWT-SVD domain image watermarking: embedding data in all frequencies. In: Proc. ACM Workshop on Multimedia and Security, Germany, pp 166–174
Ganic E, Zubair N, Eskicioglu A (2003) An optimal watermarking scheme based on singular value decomposition. In: Proc. IASTED Int. Conf. on Communication, Network, and Information Security, NY, pp. 85–90
Golub GH, Van Loan CF (1989) Matrix computations. Johns Hopkins Univ Press, Baltimore
Hernandez J, Amado M, Perez-Gonzalez F (2000) DCT-domain watermarking techniques for still images: detector performance analysis and a new structure. IEEE Trans Image Process 9(1):55–67
Hsu C, Wu J (1999) Hidden digital watermarks in images. IEEE Trans Image Process 8(1):58–68
Huang F, Guan ZH (2004) A hybrid SVD-DCT watermarking method based on LPSNR. Pattern Recognit Lett 25(15):1769–1775
Kang X, Zeng W, Huang J (2008) A multi-band wavelet watermarking scheme. International Journal of Network Security 6(2):121–126
Knockaert L, Backer B, Zutter D (1999) SVD compression, unitary transforms, and computational complexity. IEEE Trans Signal Process 47(10):2724–2729
Kong W, Bian B, Wu D, Niu X (2006) SVD based blind video watermarking algorithm. In: Proc. International Conference on Innovative Computing, Information, and Control, Beijing, China, pp 265–268
Laub AJ (1979) A Schur method for solving algebraic riccati equations. IEEE Trans Autom Control 24(6):913–921
Laub AJ (1982) Schur techniques for riccati differential equations, feedback control of linear and nonlinear systems. In: Lecture Notes In Control and Information Sciences, Springer, Berlin, 39:165–174
Lee J (1990) A Schur vector method to solve higher order Lyapunov equations. IEEE Trans Autom Control 35(2):215–218
Lei CU, Cheung CM, Wong N (2008) Efficient 2D linear-phase IIR filter design and application in image processing. Lect Notes Electr Eng 4:411–424
Lin C, Wu M, Bloom J, Cox IJ, Miller M, Lui Y (2001) Rotation, scale, and translation resilient watermarking for images. IEEE Trans Image Process 10(5):767–782
Liu J, Niu X, Kong W (2006) Image watermarking based on singular value decomposition. In: Proc. of the 2006 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Pasadena, CA, USA, pp. 457–460
Liu R, Tan T (2002) An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans Multimedia 4(1):121–128
Lu W, Lu H (2008) Robust watermarking based on subsampling and nonnegative matrix factorization. Informatica 19(4):555–566
Lu W, SunW LuH (2009) Robust watermarking based on DWT and nonnegative matrix factorization. Comput Electr Eng 35(1):183–188
Martin CD, Van Loan CF (2006) Solving real linear systems with the complex Schur decomposition. SIAM J Matrix Anal 29:184–198
Ming-Shi W, Wei-Che C (2009) A hybrid DWT-SVD copyright protection scheme based on k-means clustering and visual cryptography. Comput Stand Interfaces 31(4):757–762
Mohammad A, Alhaj A, Shaltaf S (2008) An improved SVD-based watermarking scheme for protecting rightful ownership. Signal Process 88(3):2158–2180
Ouhsain O, Ben-Hamza A (2009) Image watermarking scheme using nonnegative matrix factorization and wavelet transform. Expert Syst Appl 36(1):2123–2129
Rachid A, Hashim G (1992) Model reduction via Schur decomposition. IEEE Trans Autom Control 37(5):666–668
Reddy A, Chatterji B (2005) A new wavelet based logo-watermarking scheme. Pattern Recognit Lett 26(7):1019–1027
Rezazadeh Z, Yazdi M (2009) A non-oblivious image watermarking system based on singular value decomposition and texture segmentation. In: Proc. of World Academy of Science, Engineering, and Technology13:255–259
Ruanaidh J, Dowling W, Boland F (1996) Phase watermarking of digital images. In: Proc. IEEE Int. Conf. Image Processing, Switzerland, vol. 3, pp. 239–242
Safaonov M, Chiang RY (1989) A Schur method for balanced truncation model reduction. IEEE Trans Autom Control 34:729–733
Sebe F, Domingo-Ferrer J, Herrera J (2000) Spatial-domain image watermarking robust against compression, filtering, cropping, and scaling. Proc. 3rd int. Workshop on Information Security, pp. 44–53
Shieh J, Lou D, Chang M (2006) A semi-blind digital watermarking scheme based on singular value decomposition. Comput Stand Interfaces 28(4):428–440
Song F, Zhang D, Yang J (2006) A novel dimensionality-reduction approach for face recognition. Neurocomputing 69:1683–1687
Tao P, Eskicioglu A (2004) A robust multiple watermarking scheme in the discrete wavelet transform domain. In: Proc. SPIE, vol. 5601, pp. 133–144
Wang S, Lin Y (2004) Wavelet tree quantization for copyright protection watermarking. IEEE Trans Image Process 13(2):154–164
Wang R, Lin CF, Lin JC (2001) Image hiding by optimal LSB substitution and genetic algorithm. Pattern Recognit 34(3):671–683
Wang XY, Yang HY, Yang Cui CY (2008) An SVM-based robust digital image watermarking against de-synchronization attacks. Signal Process 88(9):2193–2205
Wu Y (2005) On the security of SVD based ownership watermarking. IEEE Trans Multimedia 7(4):624–627
Yavus E, Telatar Z (2007) Improved SVD-DWT based digital image watermarking against watermark ambiguity. In: Proceedings of the 2007 ACM symposium on Applied computing, Seoul, Korea, pp 1051–1055
Zhang XP, Li K (2005) Comments on ‘an SVD-based watermarking scheme for protecting rightful ownership’. IEEE Trans Multimedia 7(3):593–594
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mohammad, A.A. A new digital image watermarking scheme based on Schur decomposition. Multimed Tools Appl 59, 851–883 (2012). https://doi.org/10.1007/s11042-011-0772-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-011-0772-7