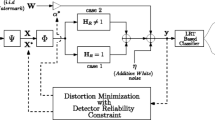
Abstract
Collusion attack is known to be a cost-effective attack against digital fingerprinting. Under the constraint that the fingerprint embedding algorithm and the host signal are unavailable to the adversaries, it is not very easy to perform efficient collusion attack. To solve this problem, we propose a generic collusion attack optimization (GCAO) strategy for traditional spread-spectrum (SS) and quantization index modulation (QIM) fingerprinting. First, we analyze the differential signal of two fingerprinted copies of the same content generated by popular fingerprint embedding algorithms, including both traditional SS-based embedder and QIM-based embedder. Based on the analysis of the differential signal, we construct a fingerprint forensic detector that identifies which embedder is applied and what the embedding parameters are adopted. Then, we improve the earlier proposed SANO collusion attack. Two components outlined above constitute a generic collusion attack optimization strategy. The simulation results show that the proposed forensic detector provides trustworthy performance: the detector can correctly identify the fingerprint embedding algorithm, and the probabilities of estimating the fingerprint length and position are higher than 86 % and 87 % for SS-based embedding and 84 % and 80 % for QIM-based embedding, respectively. The further experimental results illustrate that the proposed GCAO attack provides a better tradeoff between the probability of being undetected and the quality of the attacked copy.









Similar content being viewed by others
References
Barni M, Bartolini F, De Rosa A, Piva A (2001) A new decoder for the optimum recovery of nonadditive watermarks. IEEE Trans Image Process 10(5):755–766
Chang SG, Yu B, Vetterli M (2002) Spatially adaptive wavelet thresholding with context modeling for image denoising. IEEE Trans Image Process 9(9):1522–1531
Chen B, Wornell GW (1999) An information-theoretic approach to the design of robust digital watermarking systems. In: IEEE international conference on acoustics, speech, and signal processing, vol 4. pp 2061–2064
Chen B, Wornell GW (2001) Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans Inf Theory 47(4):1423–1443
Cox IJ, Kilian J, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Donoho DL (1995) De-noising by soft-thresholding. IEEE Trans Inf Theory 41(3):613–627
Donoho DL, Johnstone JM (1994) Ideal spatial adaptation by wavelet shrinkage. Biometrika 81(3):425
Eggers JJ, Girod B (2001) Quantization effects on digital watermarks. Signal Process 81(2):239–263
Feng H, Ling H, Zou F, Lu Z (2012) Svm-based anti-forensic method for spread-spectrum fingerprinting. Security and Communication Networks. doi:10.1002/sec.503
Feng H, Ling H, Zou F, Yan W, Lu Z (2012) A collusion attack optimization strategy for digital fingerprinting. ACM Trans Multimed Comput Commun Appl 8(2S):20
Feng H, Ling H, Zou F, Yan W, Sarem M, Lu Z (2013) A collusion attack optimization framework toward spread-spectrum fingerprinting. Appl Soft Comput 13:3482–3493
Feng H, Ling HF, Zou FH, Yan WQ, Lu ZD (2010) Optimal collusion attack for digital fingerprinting. In: Proceedings of ACM international conference on Multimedia (MM’10). ACM, New York, pp 767–770
He S, Wu M (2005) Performance study on multimedia fingerprinting employing traceability codes. Lecture Notes in Computer Science, vol 3710. Springer, p 84
He S, Wu M (2006) Joint coding and embedding techniques for multimedia fingerprinting. IEEE Trans Inf Forensic Secur 1(2):231–247
Kirovski D, Mihcak MK (2005) Bounded gaussian fingerprints and the gradient collusion attack. In: IEEE international conference on acoustics, speech, and signal processing, vol 2. New York, pp 1037–1040
Kiyavash N, Moulin P (2006) A framework for optimizing nonlinear collusion attacks on fingerprinting systems. In: 40th Annual Conference on Information Sciences and Systems. pp 1170–1175
Kiyavash N, Moulin P (2009) Performance of orthogonal fingerprinting codes under worst-case noise. IEEE Trans Inf Forensic Secur 4(3):293–301
Kuribayashi M., Kato H. (2010) Impact of rounding error on spread spectrum fingerprinting scheme. IEEE Trans Inf Forensic Secur 5(4):670–680
Ling H, Feng H, Zou F, Yan W, Lu Z (2010) A novel collusion attack strategy for digital fingerprinting. In: Kim YS H-J, Barni M (eds) IWDW 2010, LNCS 6526. Springer, Heidelberg, pp 224–238
Ming-Shing H, Din-Chang T, Yong-Huai H (2001) Hiding digital watermarks using multiresolution wavelet transform. IEEE Trans Ind Electron 48(5):875–882
Qiao L, Cox IJ (2007) Using perceptual models to improve fidelity and provide resistance to valumetric scaling for quantization index modulation watermarking. IEEE Trans Inf Forensic Secur 2(2):127–139
Robertson MA, Stevenson RL (2005) Dct quantization noise in compressed images. IEEE Trans Circ Syst Video Tech 15(1):27–38
Schuchman L (1964) Dither signals and their effect on quantization noise. IEEE Trans Commun Techn 12(4):162–165
Stone H (1996) Analysis of attacks on image watermarks with randomized coefficients. NEC Research Institute, Tech. Rep 96-045
Swaminathan A, He S, Wu M (2006) Exploring qim-based anti-collusion fingerprinting for multimedia. Proc SPIE 6072:698–709
Trappe W, Wu M, Wang ZJ, Liu KJR (2003) Anti-collusion fingerprinting for multimedia. IEEE Trans Signal Process 51(4):1069–1087
USC-SIPI (2012) The usc-sipi image database. Singal and Image Processing Institute, Ming Hsieh Electronic Engineering Department, University of Southern California, http://sipi.usc.edu/database/index.html
Varna AL, Shan H, Swaminathan A, Min W (2009) Fingerprinting compressed multimedia signals. IEEE Trans Inf Forensic Secur 4(3):330–345
Wang ZJ, Wu M, Trappe W, Liu KJRGroup-oriented fingerprinting for multimedia forensics. EURASIP Journal on Applied Signal Processing, vol 14, no 11. Hindawi Publishing Corporation, New York, p 2
Wang ZJ, Wu M, Zhao HV, Trappe W, Liu KJR (2005) Anti-collusion forensics of multimedia fingerprinting using orthogonal modulation. IEEE Trans Image Process 14(6):804–821
Wei ZH, Qin P, Fu YQ (1998) Perceptual digital watermark of images using wavelet transform. IEEE Trans Consum Electron 44(4):1267–1272
Xiaojun Q, Bialkowski S, Brimley G (2008) An adaptive qim- and svd-based digital image watermarking scheme in the wavelet domain. In: IEEE international conference on image processing, pp 421–424
Zhao HV, Min W, Wang ZJ, Liu KJR (2005) Forensic analysis of nonlinear collusion attacks for multimedia fingerprinting. IEEE Trans Image Process 14(5):646–661
Acknowledgments
The authors appreciate the anonymous reviewers and the Associate Editor. This work is supported by NSF of China Grants 61301279, the Fundamental Research Funds for the Central Universities(WUT:2013-IV-068).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Feng, H., Gan, L., Ling, H. et al. A generic collusion attack optimization strategy for traditional spread-spectrum and quantization index modulation fingerprinting. Multimed Tools Appl 74, 6967–6988 (2015). https://doi.org/10.1007/s11042-014-1948-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-014-1948-8