Abstract
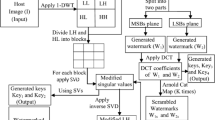
In this paper, a zero-watermarking based copyright protection scheme is proposed. The secret watermark image is not embedded in the host image rather it is encrypted with the host image. The proposed scheme is making use of discrete cosine transform and singular value decomposition to extract robust features of the host image. Further the selected robust features are used to encrypt the secret image. The secret image is encrypted with the host image by generating two shares namely master share and ownership share. The master share is generated by differential classification of features extracted. The ownership share is generated with the help of master share and the secret image. The two shares separately don’t give any clue of the secret image but when stacked together the encrypted secret image is revealed. Experimental study is conducted to evaluate the robustness of the algorithm against various signal processing and geometrical attacks.








Similar content being viewed by others
References
Agarwal H, Balasubramanian R, Venkat I (2014) Blind reliable invisible watermarking method in wavelet domain for face image watermark. Multimedia Tools and Applications
Bhatnagar G, Jonathan M, Wu Q, Balasubramanian R (2011) A new aspect in robust digital watermarking. Multimedia Tools and Applications
Cao H, Xiang H, Li X, Liu M, Yi S, Wei F (2006) A zero-watermarking algorithm based on dwt and chaotic modulation. In: Independent Component Analyses, Wavelets, Unsupervised Smart Sensors, and Neural Networks IV, vol 6247, p 624716. doi:10.1117/12.663927
Chang C, Chuan JC (2002) An image intellectual property protection scheme for gray-level images using visual secret sharing strategy. Pattern Recogn Lett 23:931–941
Chen T, Horng G, Lee W (2005) A publicly verifiable copyright-proving scheme resistant to malicious attacks. IEEE Trans Ind Electron 52:327–334
Fu Z, Yu B (2013) Optimal pixel expansion of deterministic visual cryptography scheme. Multimedia Tools and Applications
Gao G (2012) Composite chaos-based lossless image authentication and tamper localization. Multimedia Tools and Applications
Guitart O, Kim HC, Delp EJ (2006) Watermark evaluation testbed. J Electron Imaging 14(4)
Horng S, Rosiyadi D, Fan P, Wang X, Khurram Khan M, Pan Y (2012) An efficient copyright protection scheme for e-government document images. IEEE Multimedia 19(3):62–73. doi:10.1109/MMUL.2011.41
Hsu C, Hou Y (2005) Copyright protection scheme for digital images using visual cryptography and sampling methods. Opt Eng 44(7):077,003
Huynh-Thu Q, Ghanbari M (2008) Scope of validity of psnr in image/video quality assessment. Electron Lett 44(13)
Hwang RJ (2000) A digital image copyright protection scheme based on visual cryptography. Tamkang J Sci Eng 3(2):97–106
Kutter M, Petitcolas FAP (1999) A fair benchmark for image watermarking systems. In: Proceedings of SPIE Security and Watermarking of Multimedia Contents, vol 3657, pp 226–239
Lin WH, Horng SJ, Kao TW, Chen RJ, Chen YH, Lee CL, Teranoe T (2009) Image copyright protection with forward error correction. Expert Syst Appl 36(9):11,888–11,894
Lin WH, Horng SJ, Kao TW, Fan P, Lee CL, Pan Y (2008) An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Trans Multimed 10(5):746–757
Lin WH, Wang YR, Horng SJ (2009) A wavelet-tree-based watermarking method using distance vector of binary cluster. Expert Syst Appl 36(6):9869–9878
Matsumoto M, Nishimura T (1998) Mersenne twister: A 623 -dimensionally equidistributed uniform pseudorandomnumber generator. ACM Transactions on Modeling and Computer Simulations 8(1):3–30
Naor M, Shamir A (1995) Visual cryptography. In: Proceedings of the Advances in Cryptology, Lecture Notes in Computer Science, vol 950, pp 1–12. EUROCRYPT94, LNCS. Springer-Verlag
Rani A, Balasubramanian R, Kumar S (2013) A robust watermarking scheme exploiting balanced neural tree for rightful ownership protection. Multimedia Tools and Applications:1–24
Rawat S, Raman B (2012) A blind watermarking algorithm based on fractional fourier transform and visual cryptography. Signal Proc 92(6):1480–1491
Su Q, Niu Y, Zou H, Zhao Y, Yao T (2013) A blind double color image watermarking algorithm based on qr decomposition. Multimedia Tools and Applications
Swanson MD, Kobayashi M, Tewfik A (1998) Multimedia data embedding and watermarking technologies. In: Proceedings IEEE, vol 86(6), pp 1064—1087
Voloshynovski S, Pereiera S, Pun T, Eggers J, Su J (2001) Attacks on digital watermarks: Classification, estimation-based attacks and benchmarks. IEEE Commun Mag 39:118–126
Wang FH, Yen KK, Jain LC, Pan JS (2007) Multiuser-based shadow watermark extraction system. Inf Sci 177(12):25222532
Wang M, Chen W (2009) A hybrid dwt-svd copyright protection scheme based on k-means clustering and visual cryptography. Computer Standards & Interfaces 31:757–762
Wang MS, Chen WC (2006) Digital image copyright protection scheme based on visual cryptography and singular value decomposition. Opt Eng 46(6):067,006
Wang S, Lin Y (2004) Wavelet tree quantization for copyright protection watermarking. IEEE Trans Image Process 13:154–165
Yu L, Niu X, Sun S (2005) Print-and-scan model and the watermarking countermeasure. Image Vis Comput 23:807814
Zhou Y, Jin W (2011) A novel image zero-watermarking scheme based on dwt-svd. In: International Conference on Multimedia Technology (ICMT), pp. 2873–2876. IEEE. doi:10.1109/ICMT.2011.6002066
Acknowledgments
This research work is supported by Council of Scientific and Industrial Research (CSIR), New Delhi under the grant number CSR-557-MTD.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Rani, A., Raman, B. An image copyright protection scheme by encrypting secret data with the host image. Multimed Tools Appl 75, 1027–1042 (2016). https://doi.org/10.1007/s11042-014-2344-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-014-2344-0