Abstract
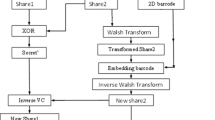
The basic idea of Visual Cryptography (VC) is to divide a secret image into several partitions which are called VC shares. With various categories of VC schemes having been developed to enhance the maturity of VC since its emergence, one of obsessions in current investigations of VC is that each VC share lacks authentication. In this paper, we analyze VC authentication methods using 2D barcodes and embed binary codes into VC shares for authentication purpose. The objective of this paper is to present a method of improving the authentication of traditional VC scheme. Our contribution of this paper is to propose a scheme of embedding 2D barcodes into given VC shares to prevent cheating, we search the best region of a given share where the 2D barcode could be embedded into so as to keep the visual quality of the revealed secret.







Similar content being viewed by others
References
Ateniese G, Blundo C, Santis AD, Stinson DR (2001) Extended capabilities for visual cryptography. Theor Comput Sci 250:143–161
Campbell A (2000) The designer’s lexicon. Chronicle Books, San Francisco
Chen Y-F, Chan Y-K, Huang C-C, Tsai M-H, Chu Y-P (2007) A multiple-level visual secret-sharing scheme without image size expansion. Inf Sci 177:4696–4710
Chen, S.-Q. A Corner Matching Algorithm Based on Harris Operator. In: Information Engineering and Computer Science (ICIECS), 2010 2nd International Conference on, pp. 1–2 (2010)
Chen Y-C, Tsai D-S, Horng G (2012) Comment on “cheating prevention in visual cryptography”. IEEE Trans Image Process 21:3319–3323
Chen Y-C, Tsai D-S, Horng G (2012) A new authentication based cheating prevention scheme in Naor–Shamir’s visual cryptography. J Vis Commun Image Represent 23:1225–1233
Dobbertin H (1998) Cryptanalysis of MD4. J Cryptol 11:253–271
Denso ADC:QR code Essentials (2011)
Gao, M., Sun, B. Blind Watermark Algorithm Based on QR Barcode. In: Wang, Y., Li, T. (eds.) Foundations of Intelligent Systems, vol. 122, pp. 457–462 (2012)
Guo T, Liu F, Wu CK (2013) Threshold visual secret sharing by random grids with improved contrast. J Syst Softw 86(8):2094–2109
Hahn, H., Jung, J. Improving performance of the decoder for two-dimensional barcode symbology PDF417. In: Braz, J., AraÚJo, H., Vieira, A., EncarnaÇÃO, B. (eds.) Information in Control, Automation and Robotics I, pp. 233–237 (2006)
Hegde, C., Manu, S., Shenoy, P., Venugopal, K., Patnaik, L. Secure authentication using image processing and Visual Cryptography for banking applications. In: 16th International Conference on Advanced Computing and Communications, pp. 65–72 (2008)
Horng G, Chen T, Tsai D-S (2006) Cheating in visual cryptography. Des Codes Crypt 38:219–236
Hou Y-C (2003) Visual cryptography for color images. Pattern Recogn 36:1619–1629
Hu CM, Tzeng WG (2007) Cheating prevention in visual cryptography. IEEE Trans Image Process 16(1):36–45
International Organization for Standardization ISO/IEC 16022–2000: Information technology international symbology specification-Data matrix. Switz Joint Tech Comm ISO/IEC JTC 1:67–87 (2004)
Jiang, F., Liu, Z., Feng, X. Research of Encodation Schemes Selecting Optimization for Character 2D Barcode. In: Yang, Y., Ma, M. (eds.) Proceedings of the 2nd International Conference on Green Communications and Networks 2012 (GCN 2012): Volume 1, vol. 223, pp. 615–623. Springer Berlin Heidelberg (2013)
Kuo, D., Wong, D., Gao, J., Chang, L. A 2D Barcode Validation System for Mobile Commerce. In: Bellavista, P., Chang, R.-S., Chao, H.-C., Lin, S.-F., Sloot, P.A. (eds.) Advances in Grid and Pervasive Computing, vol. 6104, pp. 150–161 (2010)
Lau, D.L., Arce, G.R.: Modern digital halftoning. CRC Press (2011)
Lee Y-S, Chen T-H (2012) Insight into collusion attacks in random-grid-based visual secret sharing. Signal Process 92:727–736
Liu F, Wu CK, Lin XJ (2008) Color visual cryptography schemes. Inf Secur, IET 2:151–165
Liu F, Wu CK, Lin XJ (2010) Some extensions on threshold visual cryptography schemes. Comput J 53(1):107–119
Liu F, Wu C, Lin X (2011) Cheating immune visual cryptography scheme. IET Inf Secur 5:51–59
Memon N, Wong PW (1998) Protecting digital media content. Commun ACM 41:35–43
Metz C (1999) AAA protocols: authentication, authorization, and accounting for the internet. IEEE Internet Comput 3:75–79
Myodo, E., Sakazawa, S., Takishima, Y.: Visual cryptography based on void-and-cluster halftoning technique. In: Image Processing, 2006 I.E. International Conference on, pp. 97–100. IEEE (2006)
Myodo, E., Takagi, K., Miyaji, S., Takishima, Y.: Halftone visual cryptography embedding a natural grayscale image based on error diffusion technique. In: Multimedia and Expo, 2007 I.E. International Conference on, pp. 2114–2117. IEEE (2007)
Nakajima, M., Yamaguchi, Y.: Extended Visual Cryptography for Natural Images. In: WSCG, pp. 303–310 (2002)
Naor, M., Pinkas, B. Visual Authentication and Identification. In: Kaliski Jr., B.S. (ed.) CRYPTO 1997. LNCS, vol. 1294, pp. 322–336 (1997)
Naor, M., Shamir, A.: Visual cryptography. In: Advances in Cryptology – EUROCRYPT’ 94, pp. 1–12. Springer (1995)
Revenkar PS, Anjum A, Gandhare WZ (2010) Survey of VC schemes. Int J Secur Appl 4:49–56
B. V. Rompay, “Analysis and Design of Cryptographic Hash functions, MAC algorithms and Block Ciphers”, Ph.D. thesis, Katholieke Universiteit, Leuven, Belgium (2004)
Rouillard, J.: Contextual QR codes. In: ICCGI 2008. The Third International Multi- Conference on Computing in the Global Information Technology, July 27-August 1, pp. 50–55 (2008)
Shyu SJ, Huang S-Y, Lee Y-K, Wang R-Z, Chen K (2007) Sharing multiple secrets in VC. Pattern Recogn 40:3633–3651
Sobti R, Geetha G (2012) Cryptographic hash functions: a review. IJCSI Int J Comput Sci Issues 9:461–479
Solms, S.H., Solms, R.: Information Technology Governance. Information Security Governance, pp. 1–7. Springer (2009)
Stoleru D (2005) Extended visual cryptography schemes. Dr Dobb’s J 30:36–39
Touch JD (1995) Performance analysis of MD5. SIGCOMM Computing Commun Rev 25:77–86
Tuyls, P., Hollmann, H. D. L., Lint, J. H. V., Tolhuizen, L.: XOR-based VC schemes. Designs, Codes and Cryptography 37, 169–186 (2005) 19 Veltkamp, R. C.: Shape matching: similarity measures and algorithms. Paper presented at the Shape Modeling and Applications, SMI 2001 International Conference on (2001).
Vincent E, Laganière R (2005) Detecting and matching feature points. J Vis Commun Image Represent 16:38–54
Wang G (2014) Content based authentication of visual cryptography. Master Thesis. Auckland University of Technology, New Zealand
Wang, Z., Arce, G.R.: Halftone visual cryptography through error diffusion. In: Image Processing, 2006 I.E. International Conference on, pp. 109–112. IEEE (2006)
Wei-Qi Yan, Duo Jin, Kankanhalli, M.S. Visual cryptography for print and scan applications, Proceedings of the IEEE ISCAS’04, pp.572 - 575 (2004)
Weir J, Yan W-Q (2009) Dot-size variant VC. In: Ho ATS, Shi YQ, Kim HJ, Barni M (eds) IWDW 2009. LNCS, vol 5703. Springer, Heidelberg, pp 136–148
Weir, J., Yan, W.: A Comprehensive Study of VC. In: Shi, Y. (ed.) Transactions on Data Hiding and Multimedia Security V, vol. 6010, pp. 70–105. Springer Berlin Heidelberg (2010)
Weir, J., Yan, W.: Authenticating VC Shares Using 2D Barcodes. In: Shi, Y., Kim, H.-J., Perez-Gonzalez, F. (eds.) Digital Forensics and Watermarking, vol. 7128, pp. 196–210. Springer Berlin Heidelberg (2012)
Weir, J., Yan, W.-Q: Sharing multiple secrets using VC. In: Circuits and Systems, 2009. ISCAS 2009. IEEE International Symposium on, pp. 509–512 (2009)
Yan, Y., Li, Q., Cao, M., Chen, H., Xue, J.: Application Research of Two-Dimensional Barcode in Information Construction of Colleges. In: Lu, W., Cai, G., Liu, W., Xing, W. (eds.) Proceedings of the 2012 International Conference on Information Technology and Software Engineering, vol. 212, pp. 71–80. Springer Berlin Heidelberg (2013)
Yang C-N, Chen T-S, Ching M-H (2006) Embed additional private information into two-dimensional bar codes by the visual secret sharing scheme. Integr Computer-Aided Eng 13:189–199
Yang, C., Laih, C.: Some new types of visual secret sharing schemes. In: National Computer Symposium (NCS 1999), vol. III, pp. 260–268 (1999)
Zhang, C., Ma, L., Mao, D.: A 2D Barcode Recognition System Based on Image Processing. In: Zhu, M. (ed.) Electrical Engineering and Control, vol. 98, pp. 683–688. Springer Berlin Heidelberg (2011)
Zhou, Z., Arce, G.R., Di Crescenzo, G.: Halftone visual cryptography. In: ICIP 2003. International Conference on, pp. I-521-524 vol. 521 (2003)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, G., Liu, F. & Yan, W.Q. 2D Barcodes for visual cryptography. Multimed Tools Appl 75, 1223–1241 (2016). https://doi.org/10.1007/s11042-014-2365-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-014-2365-8