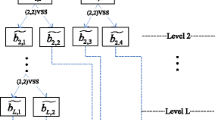
Abstract
Differently from traditional secret sharing, progressive secret sharing can gain clearer recovered secret image with more shares. However, previous progressive visual secret sharing (PVSS) schemes with unexpanded shares are only for case (2, n) other than general threshold (case), which will restrict the application range. In this paper, a general threshold PVSS construction method from case (2, n) with unexpanded shares is proposed. It has the feature of (k, n) threshold with no pixel expansion, which could be loss-tolerant and control access for a wider application. Based on the proposed construction method, a new threshold PVSS scheme is constructed. Compared with relative approaches, the proposed scheme has improved performances.








Similar content being viewed by others
References
Chen S-K (2009) Friendly progressive visual secret sharing using generalized random grids. Optical Eng 48(11):117001-1–117001-7
Chen T-H, Tsao K-H (2011) Threshold visual secret sharing by random grids. J Syst Software 84:1197–1208
Chen T-H et al (2013) Quality-adaptive visual secret sharing by random grids. J Syst Softw 86(5):1267–1274
Fang W-P, Lin J-C (2006) Progressive viewing and sharing of sensitive images. Pattern Recog Image Analysis 16(4):632–636
Guo T, Liu F, Wu CK (2013) Threshold visual secret sharing by random grids with improved contrast. J Syst Software 86(8):2094–2109
Hou Y-C (2003) Visual cryptography for color images. Pattern Recogn 36(7):1619–1629
Hou Y-C, Quan Z-Y (2011) Progressive visual cryptography with unexpanded shares. IEEE Trans on Circ and Sys for Video Tech 21(11):1760–1764
Hou Y-C, Quan Z-Y, Tsai C-F (2013) Block-based progressive visual secret sharing. Inf Sci 233:290–304
Jin D, Yan W-Q, Mohan S (2005) Kankanhalli, Progressive color visual cryptography. SPIE J Electron Imaging 14(3)
Naor, Moni, and Adi Shamir (1995) Visual cryptography, in Advances in Cryptography, Eurocrypt'94, pp. 1–12
Shyu SJ (2007) Image encryption by random grids. Patt Recog 40.3:1014–1031
Shyu SJ (2009) Image encryption by multiple random grids. Patt Recog 42:1582–1596
Wang Z, Arce GR, Di G (2009) Crescenzo. Halftone visual cryptography via error diffusion IEEE Trans Inf Forensics Security 4(3):383–396
Wang D, Zhanga L, Ma N, Li X (2007) Two secret sharing schemes based on Boolean operations [J]. Pattern Recogn 40(10):2776–2785
Weir J, Yan WQ (2010) A comprehensive study of visual cryptography, Transactions on DHMS V. LNCS 6010:70–105
Wu X (2013) Wei Sun, Random grid-based visual secret sharing with abilities of OR and XOR decryptions. J Vis Commun Image R 24:48–62
Wu X, Sun W (2013) Improving the visual quality of random grid-based visual secret sharing. Signal Process 93(5):977–995
Yan X, Shen W, Abd El-Latif AA, Niu X (2014) A novel perceptual secret sharing scheme. Trans Data Hiding Multimedia Secur IX Lect Notes Comp Sci 8363:68–90
Yan X, Wang S, El-Latif AAA et al. (2013) Visual secret sharing based on random grids with abilities of AND and XOR lossless recovery[J]. Multimedia Tools and Applications :1–22
Yang C-N (2004) New visual secret sharing schemes using probabilistic method [J]. Pattern Recogn Lett 25(4):481–494
Acknowledgement
The authors would like to thank the anonymous reviewers for their valuable discussions and comments. This work is supported by the National Natural Science Foundation of China (Grant Number: 61100187, 61301099, 61361166006).
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Yan, X., Wang, S. & Niu, X. Threshold progressive visual cryptography construction with unexpanded shares. Multimed Tools Appl 75, 8657–8674 (2016). https://doi.org/10.1007/s11042-015-2779-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2779-y