Abstract
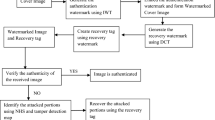
Due to rapid development of Internet and computer technology, image authentication and restoration are very essential, especially when it is utilized in forensic science, medical imaging and evidence of court. A quantization and Discrete Cosine Transform(DCT) based self-embedding fragile watermarking scheme with effective image authentication and restoration quality is proposed in this paper. In this scheme, the cover image is divided in size of 2×2 non-overlapping blocks. For each block twelve bits watermark are generated from the five most significant bits (MSBs) of each pixel and are embedded into the three least significant bits (LSBs) of the pixels corresponding to the mapped block. The proposed scheme uses two levels encoding for content restoration bits generation. The restoration is achievable with high PSNR and NCC up to 50 % tampering rate. The experimental results demonstrate that the proposed scheme not only outperforms high quality restoration effectively, but also removes the blocking artifacts and improves the accuracy of tamper localization due to use of very small size blocks.















Similar content being viewed by others
References
Bhatnagar G, Wu QJ, Raman B (2013) A new aspect in robust digital watermarking. Multimed Tools Appl 66(2):179–200
Cheng CJ, Hwang WJ, Zeng HY, Lin YC (2014) A fragile watermarking algorithm for hologram authentication. J Disp Technol 10(4):263–271
Cox I, Miller M, Bloom J, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Morgan Kaufmann
Hartung F, Kutter M (1999) Multimedia watermarking techniques. Proc IEEE 87(7):1079–1107
He H, Zhang J, Chen F (2007) Block-wise fragile watermarking scheme based on scramble encryption. In: Second International Conference on Bio-Inspired Computing: Theories and Applications, 2007. BIC-TA 2007. IEEE, pp 216–220
Kang X, Yang R, Huang J (2011) Geometric invariant audio watermarking based on an lcm feature. IEEE Trans Multimed 13(2):181–190
Korus P, Dziech A (2013) Efficient method for content reconstruction with self-embedding. IEEE Trans Image Process 22(3):1134–1147
Leng L, Zhang J, Xu J, Khan MK, Alghathbar K (2010) Dynamic weighted discrimination power analysis in dct domain for face and palmprint recognition. In: International Conference on Information and Communication Technology Convergence (ICTC), 2010. IEEE, pp 467–471
Li X, Zhang H, Chen M (2012) Self-recovery fragile watermarking based on superior block-wise tamper detection. In: IEEE 11th International Conference on Signal Processing (ICSP), 2012, vol 3. IEEE, pp 1697–1700
Preda RO (2013) Semi-fragile watermarking for image authentication with sensitive tamper localization in the wavelet domain. Measurement 46(1):367–373
Qian Z, Feng G, Zhang X, Wang S (2011) Image self-embedding with high-quality restoration capability. Digital Signal Process 21(2):278–286
Rahman SM, Ahmad MO, Swamy M (2009) A new statistical detector for dwt-based additive image watermarking using the gauss–hermite expansion. IEEE Trans Image Process 18(8):1782–1796
Riaz S, Javed MY, Anjum MA (2008) Invisible watermarking schemes in spatial and frequency domains. In: Fourth International Conference on Emerging Technologies, 2008. ICET 2008. IEEE, pp 211–216
Singh D, Shivani S, Agarwal S (2013) Quantization-based fragile watermarking using block-wise authentication and pixel-wise recovery scheme for tampered image. Int J Image Graph 13(02):1340,002–1–1340,002–11
Singh D, Shivani S, Agarwal S (2013) Self-embedding pixel wise fragile watermarking scheme for image authentication. In: Intelligent Interactive Technologies and Multimedia. Springer, pp 111–122
Song C, Sudirman S, Merabti M (2009) Recent advances and classification of watermarking techniques in digital images. In: Proceedings of Post Graduate Network Symposium
Song C, Sudirman S, Merabti M (2012) A robust region-adaptive dual image watermarking technique. J Vis Commun Image Represent 23(3):549–568
Wang S, Zheng D, Zhao J, Tam WJ, Speranza F (2014) Adaptive watermarking and tree structure based image quality estimation. IEEE Trans Multimed 16(2):311–325
Wolfgang RB, Podilchuk CI, Delp EJ (1999) Perceptual watermarks for digital images and video. Proc IEEE 87(7):1108–1126
Zhang X, Qian Z, Ren Y, Feng G (2011) Watermarking with flexible self-recovery quality based on compressive sensing and compositive reconstruction. IEEE Trans Inf Forensics Secur 6(4):1223–1232
Zhang X, Wang S (2007) Statistical fragile watermarking capable of locating individual tampered pixels. IEEE Signal Process Lett 14(10):727–730
Zhang X, Wang S, Qian Z, Feng G (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495
Zhang X, Wang S, Qian Z, Feng G (2011) Self-embedding watermark with flexible restoration quality. Multimed Tools Appl 54(2):385–395
Zhang X, Xiao Y, Zhao Z (2014) Self-embedding fragile watermarking based on dct and fast fractal coding. Multimedia Tools and Application, pp 1–20
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Singh, D., Singh, S.K. DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76, 953–977 (2017). https://doi.org/10.1007/s11042-015-3010-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3010-x