Abstract
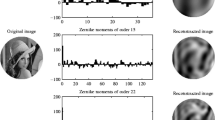
The rapid development of the Internet and digital image modification software has invited the illegal access to and use of digital images. In response, digital watermarking has emerged as a unique tool for protecting the authenticity of digital images. This technique involves the insertion of an imperceptible message within the media. This paper proposes a semi-fragile watermarking system using content-based techniques that address the challenge of image authentication. The proposed algorithm exploits the Zernike moments to authenticate an image and the Sobel edge map to perform tamper detection. The main contributions of this work are the establishment of an authentication algorithm that is robust against scaling, translation, noise pollution, rotation and JPEG compression, which are considered to be non-malicious modifications, while significantly decreasing the computational complexity using optimum orders of Zernike moments. In addition, this work addresses the challenge of capacity in terms of watermark insertion while preserving the visual quality of the image, where the capacity is increased almost three fold, as shown in the results. This process can successfully distinguish malicious attacks and reject modifications to watermarked images made through additions, replacements, and image cropping.

















Similar content being viewed by others
References
Chan P, Lyu M, Chin R (2005) A novel scheme for hybrid digital video watermarking: approach, evaluation and experimentation. IEEE Trans Circuits Syst Video Technol 15(12):1638–1649
Deng C, Gao X, Li X, Tao D (2009) A local tchebichef moments-based robust image watermarking. Signal Process 89(8):1531–1539
Eddins SL, Gonzalez R, Woods R (2004) Digital image processing using matlab. Princeton Hall Pearson Education Inc., New Jersey
Flusser J, Suk T, Zitov B, Ebrary I (2009) Moments and moment invariants in pattern recognition. Wiley Online Library
Fridrich J, Goljan M (2000) Robust hash functions for digital watermarking. In: Proceedings of the international conference on information technology: coding and computing, 2000. IEEE, pp 178–183
Hao Z, Li H, Yu P (2009) Semi-fragile watermarking technique for image tamper localization. In: International conference on measuring technology and mechatronics automation, 2009. ICMTMA’09. IEEE, pp 519–523
Hongmei L, Xinzhi Y, Jiwu H (2010) Semi-fragile zernike moment-based image watermarking for authentication. In: EURASIP journal on advances in signal processing, vol 2010
Hsieh S, Tsai I, Yeh C, Chang C (2011) An image authentication scheme based on digital watermarking and image secret sharing. Multimed Tools Appl 52(2):597–619
Hu Y, Han D (2005) Using two semi-fragile watermark for image authentication. In: Proceedings of international conference on machine learning and cybernetics, 2005. IEEE, vol 9, pp 5484–5489
Jayanthi V, Rajamani V, Karthikayen P (2011) Performance analysis for geometrical attack on digital image watermarking. Int J Electron 98(11):1565–1580
Kang H, Park J (2003) A semi-fragile watermarking using jnd. In: Proceedings of STEG, pp 127–131
Kao C, Chang L (2009) Zernike moments and edge features based semi-fragile watermark for image authentication with tampering localization. In Proceedings of APSIPA ASC 2009. APSIPA ASC
Khotanzad A, Hong YH (1990) Invariant image recognition by zernike moments. IEEE Trans Pattern Anal Mach Intell 12(5):489–497
Kim W-Y, Kim Y-S (2000) A region-based shape descriptor using zernike moments. Signal Process Image Commun 16(1):95–102
Li G, Pei S, Chen G, Cao W, Wu B (2009) A self-embedded watermarking scheme based on relationship function of corresponding inter-blocks dct coefficient. In: 13th international conference on computer supported cooperative work in design, 2009. IEEE, pp 107–112
Li C, Zhang A, Liu Z, Liao L, Huang D (2014) Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimedia tools and applications , pp 1–24
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forensics Secur 10(3):507–518
Lin C, Chang S (2000) Semifragile watermarking for authenticating jpeg visual content. In: Electronic Imaging. International Society for Optics and Photonics, pp 140–151
Lin E, Podilchuk C, Delp III E (2000) Detection of image alterations using semifragile watermarks. In: Electronic imaging. International society for optics and photonics, pp 152–163
Lin C, Wu M, Bloom J, Cox I, Miller M, Lui Y (2001) Rotation, scale, and translation resilient watermarking for images. IEEE Trans Image Process 10 (5):767–782
Liu H, Lin J, Huang J (2005) Image authentication using content based watermark. In: IEEE international symposium on circuits and systems, 2005. ISCAS 2005. IEEE, pp 4014–4017
Liu H, Rao J, Yao X (2008) Feature based watermarking scheme for image authentication. In: IEEE international conference on multimedia and expo, 2008. IEEE, pp 229–232
Maeno K, Sun Q, Chang S, Suto M (2006) New semi-fragile image authentication watermarking techniques using random bias and nonuniform quantization. IEEE Trans Multimedia 8(1):32–45
Misiti M, Misiti Y, Oppenheim G, Poggi J (1996) Wavelet toolbox. The MathWorks Inc., Natick
Ouyang B (2010) Watermarking based on unified pattern recognition framework. Ph.D. dissertation, Southern Methodist University
Petitcolas FA (2000) Watermarking schemes evaluation. IEEE Signal Process Mag 17(5):58–64
Qin C, Chang C-C, Chen P-Y (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150
Qin C, Chang C-C, Tsou P-L (2013) Robust image hashing using non-uniform sampling in discrete fourier domain. Digital Signal Process 23(2):578–585
Ruanaidh J, Pun T (1998) Rotation, scale and translation invariant spread spectrum digital image watermarking. Signal Process 66(3):303–317
Singh P, Agarwal S (2015) An efficient fragile watermarking scheme with multilevel tamper detection and recovery based on dynamic domain selection. Multimedia tools and applications, pp 1–30
Shojanazeri H, Adnan WAW, Ahmad SMS (2013) Video watermarking techniques for copyright protection and content authentication. IJCISIM 5:652–660
Teague M (1980) Image analysis via the general theory of moments ∗. JOSA 70(8):920–930
Tsai M, Yu K, Chen Y (2000) Joint wavelet and spatial transformation for digital watermarking. IEEE Trans Consum Electron 46(1):237
Tsougenis E, Papakostas G, Koulouriotis D, Tourassis V (2012) Performance evaluation of moment-based watermarking methods: a review. Journal of Systems and Software
Wallin Å, Kubler O (1995) Complete sets of complex zernike moment invariants and the role of the pseudoinvariants. IEEE Trans Pattern Anal Mach Intell 17(11):1106–1110
Wang X, Yang Y, Yang H (2010) Invariant image watermarking using multi-scale harris detector and wavelet moments. Comput Electr Eng 36(1):31–44
Xin Y, Liao S, Pawlak M (2007) Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recogn 40(12):3740–3752
Zhou X, Duan X, Wang D (2004) A semifragile watermark scheme for image authentication. In: Proceeding of 10th international conference on multimedia modelling, 2004. IEEE, pp 374–377
Zhaoqian G, Fei G, Cheng S (2012) Implementation of dwt domain-video watermarking fast algorithm in blackfin dsp. Mechanical engineering and technology, pp 773–778
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shojanazeri, H., Wan Adnan, W.A., Syed Ahmad, S.M. et al. Authentication of images using Zernike moment watermarking. Multimed Tools Appl 76, 577–606 (2017). https://doi.org/10.1007/s11042-015-3018-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3018-2