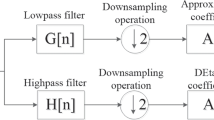
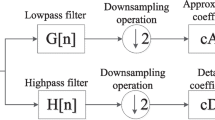
Abstract
Since existing watermarking schemes usually cannot recover the tampered position, a secure variable-capacity self-recovery watermarking scheme is proposed. Both watermark embedding capacity and security are taken into account. The original image is divided into texture blocks and smooth blocks, and the texture blocks not only save traditional information, and save the “details” information. The so-called “details” information refers to the texture information, which not only can effectively resist mean attack, but also help to improve the quality of the recovered image to meet the needs of practical work. And then according to the characteristics of different blocks, the different length compound watermarks are produced. The so-called “compound watermarks” include the authentication watermarks and information watermarks. Authentication watermarks are used to detect the tampered region, and the information watermarks which include basic watermark and additional watermark are used to recover image. Then the compound watermarks are inserted into the other blocks based on the new proposed scheme called three level secret-key embedding scheme (TLSES). And then detect the tamper blocks and recover them by the three level tamper detection scheme (TLTDS). The experimental results show that the paper can not only accurately detect the tamper region and recover image, but also can effectively resist mean attack and collage attack.


















Similar content being viewed by others
References
Abbasi A, Woo CS, Shamshirband S (2015) Robust image watermarking based on Riesz transformation and IT2FLS. Measurement 74(10):116–129. doi:10.1016/j.measurement.2015.06.006
Botta M, Cavagnino D, Pomponiu V (2015) A successful attack and revision of a chaotic system based fragile watermarking scheme for image tamper detection. Int J Electron Commun 69(1):242–245. doi:10.1016/j.aeue.2014.09.004
Cai N, Zhu NN, Weng SW et al (2015) Difference angle quantization index modulation scheme for image watermarking. Signal Process Image Commun 34(5):52–60. doi:10.1016/j.image.2015.03.010
Chang JD, Chen CS, Tsai CS (2013) Lbp-based fragile watermarking scheme for image tamper detection and recovery. In: 2013 I.E. international symposium on next-generation electronics (ISNE), IEEE. Tamsui, New Taipei City, pp 173–176. doi: 10.1109/ISNE.2013.6512330
Chang C, Fan YH, Tai WL (2008) Four-scanning attack on hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 41(2):654–661. doi:10.1016/j.patcog.2007.06.003
Chen YC (2014) Research on image authenticatin technology of invariant feature-based digital watermarking and perceptual hash. South China University of Technology
Chen F, He HJ, Wang HX (2012) Variable-payload self-recovery watermarking scheme for digital image authentication. Chin J Comput 35(1):154–163
Dadkhah S, Manaf AA, Hori Y et al (2014) An effective SVD-based image tampering detection and self-recovery using active watermarking. Signal Process Image Commun 29(10):1197–1210. doi:10.1016/j.image.2014.09.001
Deguillaume F, Voloshynovskiy S, Pun T (2003) Secure hybrid robust watermarking resistant against tampering and copy attack. Signal Process 83(10):2133–2147. doi:10.1016/S0165-1684(03)00172-5
Fridrich J, Goljan M (1999) Images with self-correcting capabilities. Proc IEEE Int Conf Image Process Kobe: IEEE 1999:792–796. doi:10.1109/ICIP.1999.817228
Fridrich J, Goljan M, Memon N (2002) Cryptanalysis of the Yeung–Mintzer fragile watermarking technique. J Electron Imaging 11(2):262–274
Ghosal SK, Mandal JK (2014) Binomial transform based fragile watermarking for image authentication. J Inf Secur Appl 19(4–5):272–281. doi:10.1016/j.jisa.2014.07.004
He HJ, Zhang JS, Chen F (2008) A self-recovery fragile watermarking scheme for image authentication with superior localization. Sci China: Ser F Inf Sci 51(10):1487–1507
He HJ, Zhang JS, Chen F (2009) Adjacent-block based statistical method for self-embedding watermarking techniques. Signal Process 89(8):1557–1566. doi:10.1016/j.sigpro.2009.02.009
He HJ, Zhang JS, Tai HM (2008) Block-Chain Based Fragile Watermarking Scheme with Superior Localization. Proc of the 10th Int Conf on Information Hiding. Springer, Berlin, pp 147–160. doi: 10.1007/978-3-540-88961-8_11
He HJ, Zhang JS, Tai HM (2009) Self-recovery fragile watermarking using block-neighborhood tampering characterization. Proc of the 11th Int Conf on Information Hiding. Springer, Berlin. pp 132–145.doi: 10.1007/978-3-642-04431-1_10
Holiman M, Memon N (2000) Counterfeiting attacks on oblivious block-wise independent invisible watermarking schemes. IEEE Trans Image Process 3(10):432–441. doi:10.1109/83.826780
Hsu LY, Hu HT (2015) Blind image watermarking via exploitation of inter-block prediction and visibility threshold in DCT domain. J Vis Commun Image Represent 32(10):130–143. doi:10.1016/j.jvcir.2015.07.017
Hu WC, Dai JS, Jian JS (2015) Effective composite image detection method based on feature inconsistency of image components. Digital Signal Process 39(4):50–62. doi:10.1016/j.dsp.2015.01.006
Lee TY, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 41(11):3497–3506. doi:10.1016/j.patcog.2008.05.003
Li CL, Wang YH, Ma B et al (2011) A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure. Comput Electr Eng 37(6):927–940. doi:10.1016/j.compeleceng.2011.09.007
Li CL, Wang YH, Ma B et al (2012) Tamper detection and self-recovery of biometric images using salient region-based authentication watermarking scheme. Comput Standard Interfaces 4(4):367–379. doi:10.1016/j.csi.2012.01.003
Li CL, Zhang ZX, Wang YH et al (2015) Dither modulation of significant amplitude difference for wavelet based robust watermarking. Neurocomputing 166(20):404–415. doi:10.1016/j.neucom.2015.03.039
Lin PL, Hsieh CK, Huang PW (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 38(12):2519–2529. doi:10.1016/j.patcog.2005.02.007
Lou OJ (2010) Feature point based image watermarking scheme in contourlet domain against geometrical attacks. J Comput Res Dev 35(1):154–163
Muhammad AQ, Mohamed D (2015) A bibliography of pixel-based blind image forgery detection techniques. Signal Process Image Commun 39(11):46–74. doi:10.1016/j.image.2015.08.008
Nidaa AA (2015) Image watermark detection techniques using quadtrees. Appl Comput Informatics 11(2):102–115. doi:10.1016/j.aci.2014.07.003
Qi XJ, Xin X (2015) A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J Vis Commun Image Represent 30(7):312–327. doi:10.1016/j.jvcir.2015.05.006
Qian ZX, Feng GR, Zhang XP (2011) Image self-embedding with high-quality restoration capability. Digital Signal Process 21(2):278–286. doi:10.1016/j.dsp.2010.04.006
Qin C, Chang CC, Chen PY (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150. doi:10.1016/j.sigpro.2011.11.013
Qin C, Chang CC, Chen KN (2013) Adaptive self-recovery for tampered images based on VQ indexing and inpainting. Signal Process 9(4):933–946. doi:10.1016/j.sigpro.2012.11.013
Ronaldo R, Pedro GF, Mylene CQF (2016) Detecting tampering in audio-visual content using QIM watermarking. Inf Sci 328(20):127–143. doi:10.1016/j.ins.2015.08.040
Sergio BS, Nandi AK (2011) Secure fragile watermarking method for image authentication with improved tampering localisation and self-recovery capabilities. Signal Process 91(4):728–739. doi:10.1016/j.sigpro.2010.07.019
Son CH, Choo H (2014) Color recovery of black-and –white halftoned images via categorized color-embedding look-up tables. Digital Signal Process 28(5):93–105. doi:10.1016/j.dsp.2014.02.004
Verma VS, Jha RK, Ojha A (2015) Significant region based robust watermarking scheme in lifting wavelet transform domain. Expert Syst Appl 42(21):8184–8197. doi:10.1016/j.eswa.2015.06.041
Wang H, Anthony TSH, Li SJ (2014) A novel image restoration scheme based on structured side information and its application to image watermarking. Signal Process Image Commun 29(7):773–787. doi:10.1016/j.image.2014.05.001
Wang XY, Hou LM, Yang HY (2008) A robust watermarking scheme based on image feature and pseudo-zenike moments. J Comput Res Dev 45(5):772–778
Wang XY, Liu YN, Li S et al (2015) A new robust digital watermarking using local polar harmonic transform. Comput Electr Eng 29(4): in press. doi:10.1016/j.compeleceng.2015.04.001
Wang XY, Wang AL, Yang HY et al (2014) A new robust digital watermarking based on exponent moments invariants in nonsubsampled contourlet transform. Comput Electr Eng 40(3):942–955. doi:10.1016/j.compeleceng.2013.12.017
Wu Y, Deng RH (2005) Security of an ill-posed operator for image authentication. IEEE Trans Circuits Syst Video Technol 15(1):161–163. doi:10.1109/TCSVT.2004.839978(410)1
Yang CW, Shen JJ (2010) Recover the tampered image based on VQ indexing. Signal Process 90(1):331–343. doi:10.1016/j.sigpro.2009.07.007
Yang HY, Wang XY, Wang P et al (2015) Geometrically resilient digital watermarking scheme based on radial harmonic fourier moments magnitude. Int J Electron Commun 69(1):389–399. doi:10.1016/j.aeue.2014.10.012
Yu M, Wang J, Jiang GY (2015) New fragile watermarking method for stereo image authentication with localization and recovery. Int J Electron Commun 69(1):361–370. doi:10.1016/j.aeue.2014.10.006
Zhang XP, Wang SZ (2007) Statistical fragile watermarking capable of locating individual tampered pixels. IEEE Signal Process Lett 14(10):727–730. doi:10.1109/LSP.2007.896436
Zhang XP, Wang SZ (2009) Fragile watermarking scheme using a hierarchical mechanism. Signal Process 89(4):675–679. doi:10.1016/j.sigpro.2008.10.001
Zhang X, Wang S, Qian Z (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495. doi:10.1109/TIP.2010.2066981
Zhu SM, Liu JM (2010) A novel fragile watermarking scheme for image tamper detection and recovery. Chin Opt Lett 8(7):661–665
Acknowledgments
This paper has been supported by the National Youth Fund (Grant No. 61401060).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shi, H., Wang, X., Li, M. et al. Secure variable-capacity self-recovery watermarking scheme. Multimed Tools Appl 76, 6941–6972 (2017). https://doi.org/10.1007/s11042-016-3328-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3328-z