Abstract
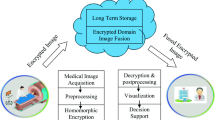
In this paper, the problem of outsourcing the selective encryption of a medical image to cloud by resource-constrained devices such as smart phone is addressed, without revealing the cover image to cloud using steganography. In the proposed framework, the region of interest of the medical image is first detected using a visual saliency model. The detected important data is then embedded in a host image, producing a stego image which is outsourced to cloud for encryption. The cloud which has powerful resources, encrypts the image and sent back the encrypted marked image to the client. The client can then extract the selectively encrypted region of interest and can combine it with the region of non-interest to form a selectively encrypted image, which can be sent to medical specialists and healthcare centers. Experimental results and analysis validate the effectiveness of the proposed framework in terms of security, image quality, and computational complexity and verify its applicability in remote patient monitoring centers.






Similar content being viewed by others
References
Abu-Marie W, Gutub A, Abu-Mansour H (2010) Image based steganography using truth table based and determinate Array on RGB indicator. International Journal of Signal and Image Processing 1:196–204
Al-Dmour H, Al-Ani A (2016) A steganography embedding method based on edge identification and XOR coding. Expert Syst Appl 46:293–306
Almeida J, Leite NJ, Torres R d S (2012) Vison: Video summarization for online applications,. Pattern Recogn Lett 33:397–409
Al-Otaibi NA, Gutub AA (2014a) 2-Leyer Security System for Hiding Sensitive Text Data on Personal Computers,. Lecture Notes on Information Theory Vol 2
Al-Otaibi NA, Gutub AA (2014b) Flexible Stego-System for Hiding Text in Images of Personal Computers Based on User Security Priority,. Proceedings of 2014 International Conference on Advanced Engineering Technologies (AET-2014):250–256
Nouf Alotaibi, Adnan Gutub, and Esam Khan, stego-system for hiding text in images of personal computers, The 12th Learning and Technology Conference, 2015.
Bruce N, Tsotsos J (2005) Saliency based on information maximization,. Adv Neural Inf Proces Syst:155–162
Buke A, Gaoli F, Yongcai W, Lei S, Zhiqi Y (2015) “healthcare algorithms by wearable inertial sensors: a survey,” Communications. China 12:1–12
Chen Y, Lee J (2012) A review of machine-vision-based analysis of wireless capsule endoscopy video. Diagnostic and therapeutic endoscopy, vol 2012
Chih-Yang L, Chang C-C, Yu-Zheng W (2008) Reversible steganographic method with high payload for JPEG images. IEICE Trans Inf Syst 91:836–845
de Avila SEF, Lopes APB, da Luz A, de Albuquerque Araújo A (2011) VSUMM: a mechanism designed to produce static video summaries and a novel evaluation method. Pattern Recogn Lett 32:56–68
Ejaz N, Mehmood I, Baik SW (2013) MRT letter: visual attention driven framework for hysteroscopy video abstraction. Microsc Res Tech 76:559–563
Erdem E, Erdem A (2013) Visual saliency estimation by nonlinearly integrating features using region covariances. J Vis 13:11–11
Goferman S, Zelnik-Manor L, Tal A (2012) context-aware saliency detection, Pattern Analysis and Machine Intelligence. IEEE Transactions on 34:1915–1926
Gupta B, Joshi RC, Misra M (2009) Defending against distributed denial of service attacks: issues and challenges. Information Security Journal: A Global Perspective 18:224–247
Gutub AA-A (2010) Pixel indicator technique for RGB image steganography. Journal of Emerging Technologies in Web Intelligence 2:56–64
Gutub A, Ankeer M, Abu-Ghalioun M, Shaheen A, Alvi A (2008) “pixel indicator high capacity technique for RGB image based steganography,” in WoSPA 2008-5th IEEE International Workshop on Signal Processing and its Applications
Gutub A, Al-Qahtani A, Tabakh A (2009) Triple-A: Secure RGB image steganography based on randomization, in Computer Systems and Applications, AICCSA 2009. IEEE/ACS International Conference on, 2009, pp. 400–403
https://ganymed.imib.rwth-aachen.de/irma/veroeffentlichungen_en.php.
Hussain M, Wahab AWA, Anuar NB, Salleh R, Noor RM (2015) Pixel value differencing steganography techniques: Analysis and open challenge,. Consumer Electronics-Taiwan (ICCE-TW), 2015 I.E. International Conference on:21–22
Khan F, Gutub AA-A, (2007) message concealment techniques using image based steganography, in The 4th IEEE GCC Conference and Exhibition
Li X, Yang B, Cheng D, Zeng T (2009) a generalization of LSB matching, Signal Processing Letters. IEEE 16:69–72
Lin C-C, Liu X-L, Yuan S-M (2015) Reversible data hiding for VQ-compressed images based on search-order coding and state-codebook mapping. Inf Sci 293:314–326
Liu Z, Zhang F, Wang J, Wang H, Huang J (2016) Authentication and recovery algorithm for speech signal based on digital watermarking. Signal Processing 123:157–166
Lv Z, Chirivella J, Gagliardo P (2016) Bigdata oriented multimedia mobile health applications. J Med Syst 40:1–10
Mehmood I, Sajjad M, Baik SW (2014a) Mobile-cloud assisted video summarization framework for efficient management of remote sensing data generated by wireless capsule sensors. Sensors 14:17112–17145
Mehmood I, Sajjad M, Baik SW (2014b) Video summarization based tele-endoscopy: a service to efficiently manage visual data generated during wireless capsule endoscopy procedure. J Med Syst 38:1–9
Mehmood I, Sajjad M, Ejaz W, Baik SW (2015) Saliency-directed prioritization of visual data in wireless surveillance networks. Information Fusion 24:16–30
Mstafa RJ, Elleithy KM (2014) A highly secure video steganography using Hamming code (7, 4),. Systems, Applications and Technology Conference (LISAT), 2014 I.E. Long Island:1–6
Mstafa RJ, Elleithy KM (2015) A video steganography algorithm based on Kanade-Lucas-Tomasi tracking algorithm and error correcting codes. Multimedia Tools and Applications:1–23
Muhammad K, (2015) Steganography: A Secure way for Transmission in Wireless Sensor Networks, arXiv preprint arXiv:1511.08865,
Muhammad K, Ahmad J, Farman H, Zubair M (2014) A novel image steganographic approach for hiding text in color images using HSI color model. Middle-East J Sci Res 22:647–654
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2015a) A novel magic LSB substitution method (M-LSB-SM) using multi-level encryption and achromatic component of an image. Multimedia Tools and Applications:1–27
Muhammad K, Ahmad J, Farman H, Jan Z, Sajjad M, Baik SW (2015b) A Secure Method for Color Image Steganography using Gray-Level Modification and Multi-level Encryption,. KSII Transactions on Internet and Information Systems (TIIS) 9:1938–1962
Muhammad K, Ahmad J, Sajjad M, Zubair M (2015c) Secure image steganography using cryptography and image transposition. NED Univ J Res 12:81–91
Muhammad K, Mehmood I, Lee MY, Ji SM, Baik SW (2015d) Ontology-based secure retrieval of semantically significant visual contents. Journal of Korean Institute of Next Generation Computing 11:87–96
Muhammad K, Sajjad M, Baik SW (2016a) Dual-level security based Cyclic18 steganographic method and its application for secure transmission of Keyframes during wireless capsule endoscopy. J Med Syst 40:1–16
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2016b) CISSKA-LSB: color image steganography using stego key-directed adaptive LSB substitution method. Multimedia Tools and Applications:1–30
Muhammad K, Ahmad J, Sajjad M, Rho S, Baik SW (2016c) Evaluating the Suitability of Color Spaces for Image Steganography and Its Application in Wireless Capsule Endoscopy,. 2016 International Conference on Platform Technology and Service (PlatCon):1–3
Parvez MT, Gutub A-A (2008) RGB intensity based variable-bits image steganography,. Asia-Pacific Services Computing Conference, APSCC’08. IEEE 2008:1322–1327
Parvez MT, Gutub AA-A (2011) Vibrant color image steganography using channel differences and secret data distribution. Kuwait J Sci Eng 38:127–142
Qin C, Chang C-C, Huang Y-H, Liao L-T (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Transactions on Circuits and Systems for Video Technology 23:1109–1118
Salvatore M, Margolies L, Kale M, Wisnivesky J, Kotkin S, Henschke CI, et al. (2014) Breast density: comparison of chest CT with mammography. Radiology 270:67–73
Singh AK, Kumar B, Dave M, Mohan A (2015a) Multiple watermarking on medical images using selective discrete wavelet transform coefficients. Journal of Medical Imaging and Health Informatics 5:607–614
Singh AK, Dave M, Mohan A (2015b) Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimedia Tools and Applications:1–21
Tewari A, Jain A, Gupta B (2016) Recent survey of various defense mechanisms against phishing attacks. Journal of Information Privacy and Security 12:3–13
Wang L, Song H, Liu P (2016) A novel hybrid color image encryption algorithm using two complex chaotic systems. Opt Lasers Eng 77:118–125
Wu H, Wang H (2013) Multibit color-mapping steganography using depth-first search,. Biometrics and Security Technologies (ISBAST), 2013 International Symposium on:224–229
Wu H, Wang H, Zhao H, Yu X (2015) Multi-layer assignment steganography using graph-theoretic approach. Multimedia Tools and Applications 74:8171–8196
Xiang T, Wong K-w, Liao X (2007) Selective image encryption using a spatiotemporal chaotic system. Chaos: An Interdisciplinary Journal of Nonlinear Science 17:023115
Xiang T, Hu J, Sun J (2015) Outsourcing chaotic selective image encryption to the cloud with steganography. Digital Signal Processing 43:28–37
Yang J-J, Li J, Mulder J, Wang Y, Chen S, Wu H, et al. (2015a) Emerging information technologies for enhanced healthcare. Comput Ind 69:3–11
Yang J, Lin Y, Gao Z, Lv Z, Wei W, Song H (2015b) Quality index for stereoscopic images by separately evaluating adding and subtracting. PLoS One 10:e0145800
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea(NRF) funded by the Ministry of Education (2013R1A1A2061978).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sajjad, M., Muhammad, K., Baik, S.W. et al. Mobile-cloud assisted framework for selective encryption of medical images with steganography for resource-constrained devices. Multimed Tools Appl 76, 3519–3536 (2017). https://doi.org/10.1007/s11042-016-3811-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3811-6