Abstract
The most essential advantage of applying linear algebra to construct visual cryptography scheme (VCS) lies in that it only requires solving linear equations in the construction of initial basis matrices, which are the basis matrices before removing the common columns. In this paper, we give some new insight into linear algebraic technique to construct VCS, where we can take more equations simultaneously. Then based on this knowledge, we propose a construction of VCS for general access structure. The construction is efficient in the sense that it gets the smallest initial pixel expansion compared with some well-known constructions. At the same time, by using the technique of deleting common columns from the initial basis matrices, the proposed construction achieves the optimal pixel expansions in most cases according to our experimental results. However, finding exact number of common columns in the initial basis matrices is a challenging issue. Then we deal with this issue and find out that the exact number of common columns is n − 2 for (2, n) threshold access structures. Finally, we provide some future research directions in the algebraic aspect of VCS.
Similar content being viewed by others
References
Adhikari A (2014) Linear algebraic techniques to construct monochrome visual cryptographic schemes for general access structure and its applications to color images. Des Codes Crypt 73(3):865–895
Ateniese G, Blundo C, De Santis A, Stinson DR (1996) Visual cryptography for general access structures. Inf Comput 129:86–106
Blundo C, De Santis A, Stinson DR (1999) On the contrast in visual cryptography schemes. J Cryptol 12(4):261–289
Blundo C, Darco P, De Santis A, Stinson DR (2003) Contrast optimal threshold visual cryptography. SIAM J Discret Math 16(2):224–261
Cimato S, De Prisco R, De Santis A (2005) Optimal colored threshold cisual cryptography schemes. Des Codes Crypt 35:311–335
Cimato S, De Prisco R, De Santis A (2006) Probabilistic Visual Cryptography Schemes. Comput J 49:97–107
Dutta S, Rohit RS, Adhikari A (2016) Constructions and analysis of some efficient t-(k, n)*-visual cryptographic schemes using linear algebraic techniques. Des Codes Cryptc 80(1):165–196
Guo T, Liu F, Wu C, Ren YW, Wang W (2014) On (k, n) visual cryptography scheme with t essential parties. In: ICITS 2013. Lecture Notes in Computer Science, vol. 8317, pp 56–68. Springer, Berlin
Hou YC, Quan ZY, Tsai CF, Tseng AY (2013) Block-based progressive visual secret sharing. Inf Sci 233:290–304
Hu CM, Tzeng WG (2007) Cheating Prevention in Visual Cryptography. IEEE Trans Image Process 16(1):36–45
Li P, Ma PJ, Li D (2012) Aspect ratio invariant visual cryptography scheme with flexible size expansion. ICIC Express Letters 6(8):2033–2038
Liu F, Wu CK, Lin XJ (2011) Cheating immune visual cryptography scheme. IET Inf Secur 5(1):51–59
Naor M, Shamir A (1994) Visual cryptography. In: Advance in Cryptography, Eurocrypt. Lecture Notes in Computer Science, vol. 950, pp. 1–12. Springer, Berlin
Shyu SJ, Chen MC (2011) Optimum pixel expansions for threshold visual secret sharing schemes. IEEE Trans Inf Forensics Secur 6(3):960–969
Shyu SJ, Jiang HW (2013) General constructions for threshold multiple-secret visual cryptography schemes. IEEE Trans Inf Forensics Secur 8(5):733–743
Shyu SJ, Chen MC (2015) Minimizing Pixel Expansion in Visual Cryptographic Scheme for General Access Structures. IEEE Trans Circuits Syst Video Technol 25 (9):1557–1561
Wang DS, Yi F, Li X (2009) On general construction for extended visual cryptography schemes. Pattern Recogn 42(11):3071–3082
Wu XT, Sun W (2013) Generalized Random Grid and Its Applications in Visual Cryptography. IEEE Trans Inf Forensics Secur 8(9):1541–1553
Yamaguchi Y (2012) An Extended Visual Cryptography Scheme for Continuous-Tone Images. Springer Trans Digital Forensics and Watermarking 7128:228–242
Yan XH, Shen W, Niu XM, Yang CN (2015) Halftone visual cryptography with minimum auxiliary black pixels and uniform image quality. Digital Signal Process 38:53–65
Yan WQ, Jin D, Kankanhalli MS (2004) Visual cryptography for print and scan applications. In: ISCAS 2004. Proceedings of IEEE international symposium on circuits and systems, vol. 5, pp. 572–575. IEEE, Canada
Yang CN, Chen TS (2006) Reduce shadow size in aspect ratio invariant visual secret sharing schemes using a square block-wise operation. Pattern Recogn 39:1300–1314
Yang CN, Shih HW, Wu CC, Harn L (2012) k out of n region incrementing scheme in visual cryptography. IEEE Trans Circuits Syst Video Technol 22:779–810
Yu B, Shen G (2014) Multi-secret visual cryptography with deterministic contrast. Multi Tools Appl 72(2):1867–1886
Acknowledgments
The authors would like to thank the anonymous reviewers for their helpful and constructive comments that improved the clarity and quality of this paper. This work was supported by the National Natural Science Foundation of China (Grant No.61602513 and No.61671448) and the Strategic Priority Research Program of the Chinese Academy of Sciences (Grant No.XDA06010701).
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A
Let us first group the set Γ0 = {{1, 2}, {1, 3}, {1, 4}} into two collections, namely \({{\Gamma }^{1}_{0}}=\{\{1,2\},\{1,3\}\}\) and \({{\Gamma }^{2}_{0}}=\{\{1,4\}\}\). For \({{\Gamma }^{1}_{0}}\), consider the following two systems of two linear equations over the binary field:
and
Let \({S^{0}_{1}}\) and \({S^{1}_{1}}\) be the Boolean matrices whose columns are just all possible solutions of (15) and (16), respectively. Thus, \({S^{0}_{1}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 1\\ 0 & 1\\ 0 & 0 \end {array} \right ]\) and \({S^{1}_{1}}=\left [ \begin {array}{cc} 0 & 1\\ 1 & 0\\ 1 & 0\\ 0 & 0 \end {array} \right ]\). Note that the fourth participant is non-essential for the strong access structure determined by \({{\Gamma }^{1}_{0}}\), so we assign it the values (00).
For \({{\Gamma }^{2}_{0}}\), consider the following two systems of one linear equations over the binary field:
and
Let \({S^{0}_{2}}\) and \({S^{1}_{2}}\) be the Boolean matrices whose columns are just all possible solutions of (17) and (18), respectively. Thus, \({S^{0}_{2}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 0\\ 0 & 0\\ 0 & 1 \end {array} \right ]\) and \({S^{1}_{2}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 0\\ 0 & 0\\ 1 & 0 \end {array} \right ]\). Note that the second and third participants are non-essential for the strong access structure determined by \({{\Gamma }^{2}_{0}}\), so we assign both of them the values (00).
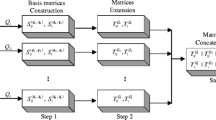
Finally, by Lemma 2 we construct a (Γ Q u a l , Γ F o r b )-VCS on a set of four participants having Γ0 = {{1, 2}, {1, 3}, {1, 4}} with the basis matrices \(S^{0}=\left [ \begin {array}{cccc} 0 & 1 & 0 & 1\\ 0 & 1 & 0 & 0\\ 0 & 1 & 0 & 0\\ 0 & 0 & 0 & 1 \end {array} \right ]\) and \(S^{1}=\left [ \begin {array}{cccc} 0 & 1 & 0 & 1\\ 1 & 0 & 0 & 0\\ 1 & 0 & 0 & 0\\ 0 & 0 & 1 & 0 \end {array} \right ]\). It gives the pixel expansion 4.
Appendix B
Let us first group the collection Γ0={{1,2},{1,3},{2,3},{1,4}} into two collections, namely \({{\Gamma }^{1}_{0}}=\{\{1,2\},\{1,3\}\}\) and \({{\Gamma }^{2}_{0}}=\{\{2,3\},\{1,4\}\}\). For \({{\Gamma }^{1}_{0}}\), consider the following two systems of two linear equations over the binary field:
and
Let \({S^{0}_{1}}\) and \({S^{1}_{1}}\) be the Boolean matrices whose columns are just all possible solutions of (19) and (20), respectively. Thus, \({S^{0}_{1}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 1\\ 0 & 1\\ 0 & 0 \end {array} \right ]\) and \({S^{1}_{1}}=\left [ \begin {array}{cc} 0 & 1\\ 1 & 0\\ 1 & 0\\ 0 & 0 \end {array} \right ]\). Note that the fourth participant is non-essential for the strong access structure determined by \({{\Gamma }^{1}_{0}}\), so we assign it the values (00).
For \({{\Gamma }^{2}_{0}}\), consider the following two systems of two linear equations over the binary field:
and
Let \({S^{0}_{2}}\) and \({S^{1}_{2}}\) be the Boolean matrices whose columns are just all possible solutions of (21) and (22), respectively. Thus, \({S^{0}_{2}}=\left [ \begin {array}{cccc} 0 & 0 & 1 & 1\\ 0 & 1 & 0 & 1\\ 0 & 1 & 0 & 1\\ 0 & 0 & 1 & 1 \end {array} \right ]\) and \({S^{1}_{2}}=\left [ \begin {array}{cccc} 0 & 0 & 1 & 1\\ 0 & 1 & 0 & 1\\ 1 & 0 & 1 & 0\\ 1 & 1 & 0 & 0 \end {array} \right ]\).
Finally, by Lemma 2 we construct a (Γ Q u a l , Γ F o r b )-VCS on a set of four participants having Γ0={{1,2},{1,3},{2,3},{1,4}} with the basis matrices \(S^{0}=\left [ \begin {array}{cccccc} 0 & 1 & 0 & 0 & 1 & 1\\ 0 & 1 & 0 & 1 & 0 & 1\\ 0 & 1 & 0 & 1 & 0 & 1\\ 0 & 0 & 0 & 0 & 1 & 1 \end {array} \right ]\) and \(S^{1}=\left [ \begin {array}{cccccc} 0 & 1 & 0 & 0 & 1 & 1\\ 1 & 0 & 0 & 1 & 0 & 1\\ 1 & 0 & 1 & 0 & 1 & 0\\ 0 & 0 & 1 & 1 & 0 & 0 \end {array} \right ]\). It gives the pixel expansion 5, obtained by deleting the common column (0110)T from the initial basis matrices S 0 and S 1.
Appendix C
Let us first group the set Γ0={{1,2},{1,3},{2,3},{1,4}} into two collections, namely \({{\Gamma }^{1}_{0}}=\{\{1,2\},\{2,3\}\}\) and \({{\Gamma }^{2}_{0}}=\{\{1,3\},\{1,4\}\}\). For \({{\Gamma }^{1}_{0}}\), consider the following two systems of two linear equations over the binary field:
and
Let \({S^{0}_{1}}\) and \({S^{1}_{1}}\) be the Boolean matrices whose columns are just all possible solutions of (23) and (24), respectively. Thus, \({S^{0}_{1}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 1\\ 0 & 1\\ 0 & 0 \end {array} \right ]\) and \({S^{1}_{1}}=\left [ \begin {array}{cc} 1 & 0\\ 0 & 1\\ 1 & 0\\ 0 & 0 \end {array} \right ]\). Note that the fourth participant is non-essential for the strong access structure determined by \({{\Gamma }^{1}_{0}}\), so we assign it the values (00).
For \({{\Gamma }^{2}_{0}}\), consider the following two systems of two linear equations over the binary field:
and
Let \({S^{0}_{2}}\) and \({S^{1}_{2}}\) be the Boolean matrices whose columns are just all possible solutions of (25) and (26), respectively. Thus, \({S^{0}_{2}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 0\\ 0 & 1\\ 0 & 1 \end {array} \right ]\) and \({S^{1}_{2}}=\left [ \begin {array}{cc} 0 & 1\\ 0 & 0\\ 1 & 0\\ 1 & 0 \end {array} \right ]\). Note that the second participant is non-essential for the strong access structure determined by \({{\Gamma }^{2}_{0}}\), so we assign it the values (00).
Finally, by Lemma 2 we construct a (Γ Q u a l , Γ F o r b )-VCS on a set of four participants having Γ0 = {{1, 2}, {3, 4}, {2, 3}, {2, 4}} with the basis matrices \(S^{0}=\left [ \begin {array}{cccc} 0 & 1 & 0 & 1\\ 0 & 1 & 0 & 0\\ 0 & 1 & 0 & 1\\ 0 & 0 & 0 & 1 \end {array} \right ]\) and \(S^{1}=\left [ \begin {array}{cccc} 1 & 0 & 0 & 1\\ 0 & 1 & 0 & 0\\ 1 & 0 & 1 & 0\\ 0 & 0 & 1 & 0 \end {array} \right ]\). It gives the pixel expansion 4.
Rights and permissions
About this article
Cite this article
Shen, G., Liu, F., Fu, Z. et al. New insight into linear algebraic technique to construct visual cryptography scheme for general access structure. Multimed Tools Appl 76, 14511–14533 (2017). https://doi.org/10.1007/s11042-016-3867-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3867-3