Abstract
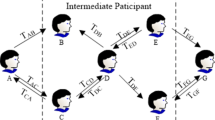
Mobile social network makes users create and share multimedia contents freely and conveniently. However, some nodes in mobile social network have malicious behavior, such as discarding or tampering packet. These factors will cause service interruptions in the process of providing multimedia contents for the user. When the service interruption happens, how to choose the more reliable backup device, reduce interruption number, increase the packet transmission efficiency and improve user’s experience of sharing multimedia contents is the object of this paper. We propose a service recovery method based on trust evaluation which adopts Dempster-Shafer (D-S) evidence theory. The service requester calculates the direct trust degree and the recommended trust degree of the backup devices, then uses the evidence combination rule to calculate the comprehensive trust degree. The backup device with the highest trust value will be seclected to recover the service. The simulation results show that this method effectively improves the packet delivery ratio, reduces the service execution time and provides users with more stable multimedia contents.









Similar content being viewed by others
References
Aivaloglou E, Gritzalis S (2010) Hybrid trust and reputation management for sensor networks. Wirel Netw 16(5):1493–1510. doi:10.1007/s11276-009-0216-8
Amgoth T, Jana PK (2014) Energy efficient and load balanced clustering algorithms for wireless sensor networks. Int J Inf Commun Technol 6(3–4):272–291. doi:10.1504/IJICT.2014.063216
Bao FY, Chen IR, Chang MJ, Cho JH (2012) Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE Trans Netw Serv Manag 9(2):169–183. doi:10.1109/TCOMM.2012.031912.110179
Batra PK, Kant K (2016) LEACH-MAC: a new cluster head selection algorithm for wireless sensor networks. Wirel Netw 22(1):49–60. doi:10.1007/s11276-015-0951-y
Bellavista P, Montanari R, Das SK (2013) Mobile social networking middleware: a survey. Pervasive Mob Comput 9(4):437–453. doi:10.1016/j.pmcj.2013.03.001
Boix EG, Carreton AL, Scholliers C, Van Cutsem T, De Meuter W, D’Hondt T (2011) Flocks: enabling dynamic group interactions in mobile social networking applications. In: 26th annual ACM symposium on applied computing, pp 425–432. doi:10.1145/1982185.1982277
Chen WY, He ZY, Ren G, Sun WW (2008) Service recovery for composite service in MANETs. In: Proceeding of IEEE international conference on wireless communication, networking and mobile computing, pp 1–4. doi:10.1109/WiCom.2008.630
Chen WY, Xu YX, Peng B, Sun WW (2008) Dynamic monitor based service recovery for composite service in MANETs. In: Proceeding of 11th IEEE international conference on communication technology, pp 557–560. doi:10.1109/ICCT.2008.4716120
Dempster A (1967) Upper and lower probabilities induced by multi-valued mapping. Ann Math Stat 38:325–339
Dooms S, De Pessemier T, Verslype D, Nelis J, De Meulenaere J, Van den Broeck W, Martens L, Develder C (2014) OMUS: an optimized multimedia service for the home environment. Multimedia Tools Appl 72(1):281–311. doi:10.1007/s11042-012-1347-y
Hu R, Liu JX, Liu XF (2011) A trustworthiness fusion model for service cloud platform based on D-S evidence theory. In: 11th IEEE/ACM international symposium on cluster, cloud and grid computing, pp 566–571. doi:10.1109/CCGrid.2011.31
Johnson DB, Maltz DA (1996) Dynamic source routing in ad hoc wireless networks. Mobile Comput 353:153–181
Li L, Wang Y (2009) Trust evaluation in composite services selection and discovery. In: 2009 IEEE international conference on services computing, pp 482–485. doi:10.1109/SCC.2009.70
Li X, Qian ZZ, You I, Lu SL (2014) Towards cost efficient mobile service and information management in ubiquitous environment with cloud resource scheduling. Int J Inf Manag 34(3):319–328. doi:10.1016/j.ijinfomgt.2013.11.007
Maria Kalavathy G, Edison Rathinam N, Seethalakshmi P (2012) Self-adaptable media service architecture for guaranteeing reliable multimedia services. Multimedia Tools Appl 57(3):633–650. doi:10.1007/s11042-010-0664-2
Paul A, Rho S, Bharnitharan K (2014) Interactive scheduling for mobile multimedia service in M2M environment. Multimedia Tools Appl 71(1):235–246. doi:10.1007/s11042-013-1490-0
Ruocco M, Ramampiaro H (2014) A scalable algorithm for extraction and clustering of event-related pictures. Multimedia Tools Appl 70(1):55–88. doi:10.1007/s11042-012-1087-z
Shafer G (1976) A mathematical theory of evidence. Princeton University Press, New York
Shaikh RA, Jameel H, d’Auriol BJ, Lee H, Lee S, Song YJ (2009) Group-based trust management scheme for clustered wireless sensor networks. IEEE Trans Parallel Distrib Syst 20(11):1698–1712. doi:10.1109/TPDS.2008.258
Sun LL, An JW, Yang Y, Zeng M (2011) Recovery strategies for service composition in dynamic network. In: 2011 International conference on cloud and service computing, pp 60–64. doi:10.1109/CSC.2011.6138553
Wang Y, Dai GP, Hou YR (2009) Dynamic methods of trust-aware composite service selection. Chin J Comput 32(8):1668–1675. doi:10.3724/SP.J.1016.2009.01668
Xia H, Jia ZP, Li X, Ju L, Sha EHM (2013) Trust prediction and trust-based source routing in mobile ad hoc networks. Ad Hoc Netw 11(7):2096–2114. doi:10.1016/j.adhoc.2012.02.009
Yang K, Galis A, Chen HH (2010) QoS-aware service selection algorithms for pervasive service composition in mobile wireless environments. Mobile Netw Appl 15:488–501. doi:10.1007/s11036-009-0189-y
Yang K, Ma JF, Yang C (2011) Trusted routing based on D-S evidence theory in wireless mesh network. J Commun 32(5):89–103
Yang ZM, Zhang BY, Dai JP, Champion AC, Xuan D, Li D (2010) E-SmallTalker: a distributed mobile system for social networking in physical proximity. In: 2010 International conference on distributed computing systems, pp 468–477. doi:10.1109/ICDCS.2010.56
Zeng LZ, Benatallah B, Ngu AHH, Dumas M, Kalagnanam J, Chang H (2004) QoS-aware middleware for web services composition. IEEE Trans Softw Eng 30(5):311–327
Zhang ZY (2012) Frontier and methodologies on digital rights management for multimedia social networks. Int J Digital Content Technol Appl 6:245–249. doi:10.4156/jdcta.vol6.issue9.31
Zhang ZY, Wang KL (2013) A trust model for multimedia social networks. Soc Netw Anal Min 3(4):969–979. doi:10.1007/s13278-012-0078-4
Zhang K, Liang XH, Shen XM, Lu RX (2014) Exploiting multimedia services in mobile social networks from security and privacy perspectives. IEEE Commun Mag 52(3):58–65. doi:10.1109/MCOM.2014.6766086
Acknowledgments
The work is supported by National Natural Science Foundation of China (61302078, 61372108, 61370220), Program for Innovative Research Team (in Science and Technology) in University of Henan Province Grant (15IRTSTHN010).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Niu, D., Rui, L., Huang, H. et al. A service recovery method based on trust evaluation in mobile social network. Multimed Tools Appl 76, 3255–3277 (2017). https://doi.org/10.1007/s11042-016-3963-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3963-4