Abstract
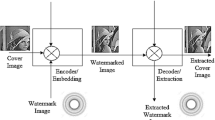
The traditional watermarking algorithms prove the rightful ownership via embedding of independent watermarks like copyright logos, random noise sequences, text etc into the cover images. Coupling biometrics with watermarking evolved as new and secure approach as it embeds user specific biometric traits and thus, narrows down the vulnerability to impostor attacks. A multimodal biometric watermarking system has been proposed in this paper in the redundant discrete wavelet transform(RDWT). Two biometric traits of the user i.e. the iris and facial features are embedded independently into the sub-bands of the RDWT of cover image taking advantage of its translation invariant property and sufficient embedding capacity. The ownership verification accuracy of the proposed system is tested based on the individual biometric traits as well as the fused trait. The accuracy was enhanced while using the fused score for evaluation. The security of the scheme is strengthened with usage of non-linear chaotic maps, randomization via Hessenberg decomposition, Arnold scrambling and multiple secret keys. The robustness of the scheme has been tested against various attacks and the verification accuracy evaluated based on false acceptance rate, false rejection rate, area under curve and equal error rate to validate the efficacy of the proposed scheme.





















Similar content being viewed by others
References
Amirgholipour S, Aboosaleh S (2014) A pre-filtering method to improve watermark detection rate in DCT based watermarking. Int Arab J Inf Technol 11(2):178–185
Barni M, Bartolini F, Cappellini V, Piva A (1998) A dct domain system for robust image watermarking. Signal Process 66(3):357–372
Barni M, Bartolini F, Cappellini V, Piva A, Rigacci F (1998) A m.a.p. identification criterion for dct based watermarking. In: Proceedings European Signal Processing Conference, pp 17–20
Bohra A, Farooq O (2009) Izharuddin Blind self-authentication of images for robust watermarking using integer wavelet transform. Int J Electron Commun 63 (8):703–707
Chang C, Tsai P, Lin C (2005) Svd based digital image watermarking scheme. Pattern Recogn Lett 26(10):1577–1586
Chu W (2003) Dct based image watermarking using subsampling. IEEE Trans Multimed 5(1):34–38
Consultants T (2010) Building a digital economy. The importance of saving jobs in Europes Creative Economy, Paris: International Chamber of Commerce/BASCAP. Available on line: www.ec.europa.eu/dgs/jrc/downloads/events/.../20110405budapestturlea.pdf (access 15/05/2011)
Cox I, Kilian J, Leighton F, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Dodis Y, Reyzin L, Smith A (2004) Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. Eurocrypt 2004(3027):523–540
Gangyi J, Mei Y, Shi S, Liu X, Kim Y (2002) New blind image watermarking in dct domain. In: Signal Processing, 6th International Conference, vol 2, pp 1580–1583
Gunsel B, Uludag U, Tekalp AM (2002) Robust watermarking of fingerprint images. Pattern Recogn 35(12):2739–2747
Hernandez J, Amado M, Perezgonzalez F (2000) Dct domain watermarking techniques for still images: Detector performance analysis and a new structure. IEEE Trans Image Process 9(1):5568
Hsu C, Wu J (1999) Hidden digital watermarks in images. Image Processing, IEEE Transactions 8(1):58–68
Jain AK, Uludag U (2003) Hiding biometric data. IEEE Trans Pattern Anal Mach Intell 25(11):1494–1498
Jain AK, Uludag U, Hsu RL (2002) Hiding a face in a fingerprint image
Kalantari N, Ahadi S, Vafadust M (2010) A robust image watermarking in the ridgelet domain using universally optimum decoder. IEEE Trans Circ Syst Video Technol 20(3):396–406
Li Z, Yap K, Lei B (2011) A new blind robust image watermarking scheme in svd dct composite domain. In: Image Processing (ICIP), 18th IEEE International Conference, pp 2757–2760
Lu Z, Zheng H, Huang J (2007) A digital watermarking scheme based on dct and svd. In: Intelligent Information Hiding and Multimedia Signal Processing, IIHMSP 2007. Third International Conference, vol 1, pp 241–244
Maity S, Kundu M (2010) Dht domain digital watermarking with low loss in image informations. Int J Electrons Commun 64(3):243–257
Mohanty S, Ranganathan N, Namballa R (2003) Vlsi implementation of invisible digital watermarking algorithms towards the development of a secure jpeg encoder. In: Proceedings of the IEEE Workshop on Signal Processing Systems Based Implementation of an Invisible Robust Image Watermarking Encoder, pp 183–188
Morita Y, Ayeh E, Adamo O, Guturu P (2009) Hardware/software co-design approach for a dct- based watermarking algorithm. In: Circuits and Systems, 2009. MWSCAS’09. 52nd IEEE International Midwest Symposium. IEEE, pp 683–686
Patra J, Phua J, Bornand D (2010) A novel dct domain crt-based watermarking scheme for image authentication surviving jpeg compression. Digit Signal Process 20 (6):1597–1611
Qi H, Zheng D, Zhao J (2008) Human visual system based adaptive digital image watermarking. Signal Process 88(1):174–188
Ratha NK, Connell JH, Bolle RM (2000) Secure data hiding in wavelet compressed fingerprint images. Proceedings of ACM Multimedia:127–130
Rawat S, Raman B (2012) A publicly veriable lossless watermarking scheme for copyright protection and ownership assertion. Int J Electron Commun 66(11):955–962
Sadreazami H, Amini M (2012) A robust spread spectrum based image watermarking in ridgelet domain. Int J Electron Commun 66(5):364–371
Soutar C, Roberge D, Stoianov A, Gilroy R, Kumar B (1999) Biometric encryption, ICSA Guide to Cryptography, McGraw-Hill
Suhail M, Obaidat M (2003) Digital watermarking based dct and jpeg model. IEEE Trans Instrum Measur 52(5):1640–1647
Uludag U, Pankanti S, Prabhakar S, Jain AK (2004) Biometric cryptosystems: issues and challenges. Proc IEEE 92(6):948–960
Vatsa M, Singh R, Mitra P, Noore A (2004) Comparing robustness of watermarking algorithms on biometrics data. Proceedings of the Workshop on Biometric Challenges from Theory to Practice ICPR Workshop:5–8
Yang C, Hu W, Lai J (2008) Dct based watermarking by quotient-embedding algorithm. In: Innovative Computing Information and Control ICICIC’08. 3rd International Conference. IEEE, pp 20–20
Zhao D, Chen G, Liu W (2004) A chaos-based robust wavelet-domain watermarking algorithm. Chaos Solitons Fractals 22:47–54
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Singh, P., Raman, B. & Roy, P.P. A multimodal biometric watermarking system for digital images in redundant discrete wavelet transform. Multimed Tools Appl 76, 3871–3897 (2017). https://doi.org/10.1007/s11042-016-4048-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4048-0