Abstract
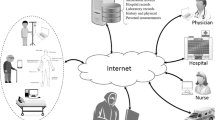
The E-health care systems allow patients to gain the health monitoring facility and access medical services remotely. A secure mechanism for mutual authentication and session key agreement is the most important requirements for E-Health Care Systems. Recently, Amin et al.’s proposed a mutual authentication and session key agreement protocol and claimed that their scheme is secure against all possible attacks. In this paper, we show that not only their scheme is vulnerable to privileged-insider attack, replay attack, session key disclosure attack, but also does not provide patient untraceability and backward secrecy. In order to withstand the mentioned security weaknesses, we propose an efficient remote mutual authentication scheme for the systems which are using ECC and Fuzzy Extractor. The proposed scheme not only resists against different security attacks, but it also provides an efficient registration, login, mutual authentication, session key agreement, and password and biometric update phases. During the experimentation, it has been observed that the proposed scheme is secure against various known attacks. Beside, our scheme is robust against privileged-insider attack that it rarely checked in security analysis. The informal analysis will ensure that our scheme provides well security protection against the different security attacks. Furthermore, we analyzed the security of the scheme using AVISPA software and Random Oracle Model. The formal analysis results and performance evaluation vouch that our scheme is also secure and efficient in computation and communication cost.











Similar content being viewed by others
References
Amin R, Biswas G (2015) A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. J Med Syst 39(8):1–19
Amin R, Biswas G (2015) A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. J Med Syst 39(3):1–17
Amin R, Biswas G (2015) An improved rsa based user authentication and session key agreement protocol usable in tmis. J Med Syst 39(8):1–14
Amin R, Hafizul Islam S, Biswas G, Khan MK (2015) An efficient remote mutual authentication scheme using smart mobile phone over insecure networks. In: Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), 2015 International Conference on, IEEE pp 1–7
Amin R, Islam SH, Biswas G, Khan MK, Kumar N (2015) An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. J Med Syst 39(11):1–18
Amin R, Islam SH, Biswas G, Khan MK, Li X (2015) Cryptanalysis and enhancement of anonymity preserving remote user mutual authentication and session key agreement scheme for e-health care systems. J Med Syst 39(11):1–21
Amin R, Islam SH, Biswas G, Khan MK, Obaidat MS (2015) Design and analysis of an enhanced patient-server mutual authentication protocol for telecare medical information system. J Med Syst 39(11):1–20
Armando A (2003) Deliverable D2. 1: the high level protocol specification language. Technical Report IST-2001-39252. http://www.avispaproject.org/delivs/2.1/d2-1.Pdf
Armando A, Compagna L (2004) SATMC: a SAT-based model checker for security protocols. In: European Workshop on Logics in Artificial Intelligence, 2004. Springer, pp 730–733
Arshad H, Nikooghadam M (2014) Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J Med Syst 38(12):1–12
AVISPA D (2003) D2. 3: The intermediate format
Awasthi AK, Srivastava K (2013) A biometric authentication scheme for telecare medicine information systems with nonce. J Med Syst 37(5):1–4
Basin D, Mödersheim S, Vigano L (2005) OFMC: a symbolic model checker for security protocols. Int J Inf Secur 4(3):181–208
Boichut Y, Héam P-C, Kouchnarenko O, Oehl F (2004) Improvements on the Genet and Klay technique to automatically verify security protocols. In: Proc. AVIS, 2004 pp. 1-11
Chatterjee S, Das AK (2015) An effective ECC-based user access control scheme with attribute-based encryption for wireless sensor networks. Security and Communication Networks 8(9):1752–1771
Chatterjee S, Das AK, Sing JK (2014) An enhanced access control scheme in wireless sensor networks. Adhoc & Sensor Wireless Networks 21(1)121–149
Chaudhry SA (2015) A secure biometric based multi-server authentication scheme for social multimedia networks. Multimedia Tools and Applications:1–21
Chaudhry SA, Mahmood K, Naqvi H, Khan MK (2015) An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J Med Syst 39(11):1–12
Chaudhry SA, Naqvi H, Farash MS, Shon T, Sher M (2015) An improved and robust biometrics-based three factor authentication scheme for multiserver environments. J Supercomput:1–17
Chaudhry SA, Naqvi H, Shon T, Sher M, Farash MS (2015) Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J Med Syst 39(6):1–11
Chen H-M, Lo J-W, Yeh C-K (2012) An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J Med Syst 36(6):3907–3915
Chevalier Y, Compagna L, Cuellar J, Drielsma PH, Mantovani J, Mödersheim S, Vigneron L A high level protocol specification language for industrial security-sensitive protocols. In: Proc. SAPS'04, Austrian Computer Society. pp. 193-205
Chuang YH, Tseng YM (2010) An efficient dynamic group key agreement protocol for imbalanced wireless networks. Int J Netw Manag 20(4):167–180
Das AK (2015) A secure user anonymity-preserving three-factor remote user authentication scheme for the telecare medicine information systems. J Med Syst 39(3):1–20
Das AK (2015) A secure and efficient user anonymity-preserving three-factor authentication protocol for large-scale distributed wireless sensor networks. Wirel Pers Commun 82(3):1377–1404
Das AK, Goswami A (2013) A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J Med Syst 37(3):1–16
Das AK, Odelu V, Goswami A (2015) A secure and robust user authenticated key agreement scheme for hierarchical multi-medical server environment in TMIS. J Med Syst 39(9):1–24
Das AK, Paul NR, Tripathy L (2012) Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Inf Sci 209:80–92
Debiao H, Jianhua C, Jin H (2012) An ID-based client authentication with key agreement protocol for mobile client–server environment on ECC with provable security. Information Fusion 13(3):223–230
Debiao H, Jianhua C, Rui Z (2012) A more secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1989–1995
Dodis Y, Reyzin L, Smith A Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In: International Conference on the Theory and Applications of Cryptographic Techniques, 2004. Springer, pp 523–540. doi:10.1007/978-3-540-24676-3_31
Dolev D, Yao AC (1983) On the security of public key protocols. Information Theory, IEEE Transactions on 29(2):198–208
He D, Khan MK, Kumar N (2015) A new handover authentication protocol based on bilinear pairing functions for wireless networks. Int J Ad Hoc Ubiquitous Comput 18(1–2):67–74
He D, Kumar N, Khan M, Lee J-H (2013) Anonymous two-factor authentication for consumer roaming service in global mobility networks. Consumer Electronics, IEEE Transactions on 59(4):811–817
He D, Kumar N, Lee J-H, Sherratt R (2014) Enhanced three-factor security protocol for consumer USB mass storage devices. Consumer Electronics, IEEE Transactions on 60(1):30–37
Islam S (2014) Design and analysis of an improved smartcard-based remote user password authentication scheme. International Journal of Communication Systems. doi:10.1002/dac.2793
Islam SH (2014) A provably secure ID-based mutual authentication and key agreement scheme for mobile multi-server environment without ESL attack. Wirel Pers Commun 79(3):1975–1991
Islam SH (2015) Design and analysis of a three party password-based authenticated key exchange protocol using extended chaotic maps. Inf Sci 312:104–130
Islam SH, Biswas G (2014) Dynamic id-based remote user mutual authentication scheme with smartcard using elliptic curve cryptography. Journal of Electronics (China) 31(5):473–488
Islam SH, Khan MK (2014) Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J Med Syst 38(10):1–16
Islam SH, Khan MK, Obaidat MS, Muhaya FTB (2015) Provably secure and anonymous password authentication protocol for roaming service in global mobility networks using extended chaotic maps. Wirel Pers Commun 84(3):2013–2034
Jiang Q, Ma J, Ma Z, Li G (2013) A privacy enhanced authentication scheme for telecare medical information systems. J Med Syst 37(1):1–8
Khan MK, Chaturvedi A, Mishra D, Kumari S (2015) On the security enhancement of integrated electronic patient records information systems. Computer Science and Information Systems 12(2):857–872
Khan MK, He D (2012) Weaknesses of “security analysis and enhancement for three-party password-based authenticated key exchange protocol”. In: Data and knowledge engineering. Springer, pp 243–249
Koblitz N (2000) Towards a quarter-century of public key cryptography. Springer. doi:10.1007/978-1-4757-6856-5
Kocher PC, Jaffe J, Jun B (1999) Differential power analysis. In: Wiener MJ (ed) Advances in Cryptology—CRYPTO ’99, 19th Annual International Cryptology Conference, Santa Barbara, California, USA, August 15–19, 1999, Proceedings, Lecture Notes in Computer Science, vol. 1666, Springer, pp 388–397
Kumari S, Chaudhry SA, Wu F, Li X, Farash MS, Khan MK (2015) An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Networking and Applications:1-14
Kumari S, Khan MK, Kumar R (2013) Cryptanalysis and improvement of ‘a privacy enhanced scheme for telecare medical information systems’. J Med Syst 37(4):1–11
Lee C-C, Hsu C-W (2013) A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn 71(1–2):201–211
Lee C-C, Li C-T, Chiu S-T, Lai Y-M (2015) A new three-party-authenticated key agreement scheme based on chaotic maps without password table. Nonlinear Dyn 79(4):2485–2495
Li C-T, Hwang M-S, Chu Y-P (2008) A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Comput Commun 31(12):2803–2814
Li W, Wen Q, Su Q, Jin Z (2012) An efficient and secure mobile payment protocol for restricted connectivity scenarios in vehicular ad hoc network. Comput Commun 35(2):188–195
Li X, Niu J-W, Ma J, Wang W-D, Liu C-L (2011) Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 34(1):73–79
Lu Y, Li L, Peng H, Yang Y (2015) An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J Med Syst 39(3):1–8
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. Computers, IEEE Transactions on 51(5):541–552
Mishra D, Das AK, Mukhopadhyay S (2016) A secure and efficient ECC-based user anonymity-preserving session initiation authentication protocol using smart card. Peer-to-peer Networking and Applications 9(1):171–192
Mishra D, Mukhopadhyay S, Chaturvedi A, Kumari S, Khan MK (2014) Cryptanalysis and improvement of Yan et al.’s biometric-based authentication scheme for telecare medicine information systems. J Med Syst 38(6):1–12
Nanni L, Lumini A (2008) Random subspace for an improved biohashing for face authentication. Pattern Recogn Lett 29(3):295–300
Pu Q, Wang J, Zhao R (2012) Strong authentication scheme for telecare medicine information systems. J Med Syst 36(4):2609–2619
Ren Y, Shen J, Wang J, Han J, Lee S (2015) Mutual verifiable provable data auditing in public cloud storage. Journal of Internet Technology 16(2):317–323
Tan Z (2014) A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J Med Syst 38(3):1–9
AVISPA T (2006) AVISPA v1. 1 User manual
Team A (2006) HLPSL tutorial the Beginner’s guide to modelling and analysing internet security protocols
Turuani M The CL-Atse protocol analyser. In: International Conference on Rewriting Techniques and Applications, 2006. Springer, pp 277–286. doi:10.1007/11805618_21
Wang X-M, Zhang W-F, Zhang J-S, Khan MK (2007) Cryptanalysis and improvement on two efficient remote user authentication scheme using smart cards. Computer Standards & Interfaces 29(5):507–512
Wazid M, Das AK, Kumari S, Li X, Wu F (2016) Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Security and Communication Networks. doi:10.1002/sec.1452
Wei J, Hu X, Liu W (2012) An improved authentication scheme for telecare medicine information systems. J Med Syst 36(6):3597–3604
Wu S, Chen K (2012) An efficient key-management scheme for hierarchical access control in e-medicine system. J Med Syst 36(4):2325–2337
Wu Z-Y, Lee Y-C, Lai F, Lee H-C, Chung Y (2012) A secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1529–1535
Xu L, Wu F (2015) Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J Med Syst 39(2):1–9
Zhu Z (2012) An efficient authentication scheme for telecare medicine information systems. J Med Syst 36(6):3833–3838
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ravanbakhsh, N., Nazari, M. An efficient improvement remote user mutual authentication and session key agreement scheme for E-health care systems. Multimed Tools Appl 77, 55–88 (2018). https://doi.org/10.1007/s11042-016-4208-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4208-2