Abstract
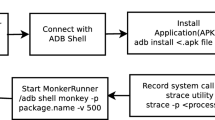
Recently, people rely on mobile devices to conduct their daily fundamental activities. Simultaneously, most of the people prefer devices with Android operating system. As the demand expands, deceitful authors develop malware to compromise Android for private and money purposes. Consequently, security analysts have to conduct static and dynamic analyses to counter malware violation. In this paper, we adopt static analysis which only requests minimal resource consumption and rapid processing. However, finding a minimum set of features in the static analysis are vital because it removes irrelevant data, reduces the runtime of machine learning detection and reduces the dimensionality of datasets. Therefore, in this paper, we investigate three categories of features, which are permissions, directory path, and telephony. This investigation considers the features frequency as well as repeatedly used in each application. Subsequently, this study evaluates the proposed features in three bio-inspired machine learning classifiers in artificial neural network (ANN) category to signify the usefulness of ANN type in uncovering unknown malware. The classifiers are multilayer perceptron (MLP), voted perceptron (VP) and radial basis function network (RBFN). Among all these three classifiers, the outstanding outcomes acquire is the MLP, which achieves 90% in accuracy and 87% in true positive rate (TPR), as well as 97% accuracy in our Bio Analyzer prediction system.


















Similar content being viewed by others
References
Aafer Y., Du, W. and Yin H., “DroidAPIMiner: Mining API-Level Features for Robust Malware Detection in Android,” in Security and Privacy in Communication Networks, 2013, pp. 86–103.
Adewole KS, Anuar NB, Kamsin A, Varathan KD, Razak SA (2017) Malicious accounts: dark of the social networks. J Netw Comput Appl 79:41–67
Adrian (2012) For Android apps, ‘zero permissions’ does not actually mean zero permissions. [Online]. Available: http://www.androidauthority.com/android-apps-zero-permissions-75001/. Accessed: 26-Feb-2017
Afifi F, Anuar NB, Shamshirband S, Choo K-KR (2016) DyHAP: dynamic hybrid ANFIS-PSO approach for predicting mobile malware. PLoS One 11(9):1–21
Allix K, Bissyandé TF, Klein J, Le Traon Y (2016) AndroZoo: collecting millions of android apps for the research community. In: MSR ‘16 proceedings of the 13th international conference on mining software repositories. Texas, Austin, pp 468–471
Amos B, Turner H, White J (2013) Applying machine learning classifiers to dynamic android malware detection at scale. In: 9th international wireless communications and mobile computing conference (IWCMC). Cagliari, Sardinia, Italy, pp 1666–1671
Anderson B. Understanding the Android File Hierarchy. [Online]. Available: http://www.all-things-android.com/content/understanding-android-file-hierarchy. Accessed: 08 Jul 2016
Android. Telephony Manager. [Online]. Available: https://developer.android.com/reference/android/telephony/TelephonyManager.html. Accessed: 01 Jul 2016
Anuar NB, Papadaki M, Furnell S, Clarke N (2013) Incident prioritisation using analytic hierarchy process (AHP): risk index model (RIM). Sec Comm Net 6(9):1087–1116
Apktool. [Online]. Available: https://ibotpeaches.github.io/Apktool/. Accessed: 29-Jun-2015
Apvrille A, Strazzere T (2012) Reducing the window of opportunity for android malware Gotta catch ‘em all. J Comput Virol 8(1):61–71
Arp D, Spreitzenbarth M, Malte H, Gascon H, Rieck K (2014) DREBIN: effective and explainable detection of android malware in your pocket. In: 21th annual network and distributed system security symposium (NDSS). San Diego, CA, pp 1–15
Arzt S, Rasthofer S, Fritz C, Bodden E, Bartel A, Klein J, Le Traon Y, Octeau D, Mcdaniel P (2014) FlowDroid: precise context, flow, field, object-sensitive and lifecycle-aware taint analysis for android apps. In: Proceedings of the 35th ACM SIGPLAN conference on programming language design and implementation. Edinburgh, United Kingdom, pp 259–269
Aung Z. and Zaw, W. “Permission-based android malware detection,” Intern J Scien Technol Res, vol. 2, no. 3, pp. 228–234, 2013.
Balakrishnan SM, Sangaiah AK (2016) Integrated QoUE and QoS approach for optimal service composition selection in internet of services (IoS). Multimed Tools Appl:1–28
Bartel A, Klein J, Le Traon Y, Monperrus M (2012) Automatically securing permission-based software by reducing the attack surface: an application to android. In: Proceedings of the 27th IEEE/ACM international conference on automated software engineering (ASE). Essen, Germany, pp 274–277
Burguera I, Zurutuza U, Nadjm-Tehrani S (2011) Crowdroid: behavior-based malware detection system for android. In: Proceedings of the 1st ACM workshop on security and privacy in smartphones and mobile devices. Illinois, Chicago, pp 15–26
Castillo CA (2011) Android Malware Past, Present, and Future. McAfee White Paper, Mobile Security Working Group. [Online]. Available: http://www.mcafee.com/us/resources/white-papers/wp-android-malware-past-present-future.pdf
Chan PPK, Song WK (2015) Static detection of android malware by using permissions and API calls. In: International Conference on Machine Learning and Cybernetics, Lanzhou, China, vol. 1, pp. 82–87
Chess B, McGraw G (2004) Static analysis for security. IEEE Sec Privacy Mag 2(6):76–79
Clarke NL, Furnell SM (2007) Authenticating mobile phone users using keystroke analysis. Int J Inf Secur 6(1):1–14
Deshotels L, Notani V, Lakhotia A (2014) DroidLegacy: automated familial classification of android malware. In: Proceedings of ACM SIGPLAN on program protection and reverse engineering workshop. San Diego, CA, USA, pp 1–12
Developers A.(2015) App Manifest. [Online]. Available: http://developer.android.com/guide/topics/manifest/manifest-intro.html. Accessed: 28 Apr 2015
Enck W. (2011) Defending users against smartphone apps: techniques and future directions. In: Jajodia S, Mazumdar C (eds) Information systems security. ICISS 2011. Lecture notes in computer science, vol 7093. Springer, Berlin, Heidelberg
Faruki P, Ganmoor V, Laxmi V, Gaur MS, Bharmal A (2013) AndroSimilar: robust statistical feature signature for android malware detection. In: Proceedings of the 6th international conference on security of information and networks. Aksaray, Turkey, pp 152–159
Feizollah A, Anuar NB, Salleh R, Amalina F, Ma’arof RR, Shamshirband S (2013a) A study of machine learning classifiers for anomaly-based mobile botnet detection. Malaysian Journal of Computer Science 26(4):251–265
Feizollah A, Shamshirband S, Anuar NB, Salleh R, Kiah MLM (2013b) Anomaly detection using cooperative fuzzy logic controller. In: Communications in Computer and Information Science (CCIS), pp. 220–231
Feizollah A, Anuar NB, Salleh R, Wahab AWA (2015a) A review on feature selection in mobile malware detection. Digit Investig 13:22–37
Feizollah A, Anuar NB, Salleh R, Suarez-Tangil G, Furnell S (2017) AndroDialysis: analysis of android intent effectiveness in malware detection. Computers & Security 65:121–134
Feng Y, Anand S, Dillig I, Aiken A (2014) Apposcopy: semantics-based detection of android malware through static analysis. In: Proceedings of the 22nd ACM SIGSOFT international symposium on foundations of software engineering. Hong Kong, China, pp 576–587
Firdaus A, Anuar NB (2015) Root-exploit malware detection using static analysis and machine learning. In: Proceedings of the fourth international conference on Computer Science & Computational Mathematics (ICCSCM 2015). Langkawi, Malaysia, pp 177–183
Freund Y, Schapire RE (1999) Large margin classification using the perceptron algorithm. Mach Learn 37(3):277–296
Gascon H, Yamaguchi F, Arp D, Rieck K (2013) Structural detection of android malware using embedded call graphs. In: Proceedings of the 2013 ACM workshop on artificial intelligence and security, Berlin, Germany, pp. 45–54
Google (2014) Google Play Store. [Online]. Available: https://play.google.com/store?hl=en. Accessed: 01-Jan-2014
Gordon MI, Kim D, Perkins J, Gilham L, Nguyen N, Rinard M (2015) Information-flow analysis of android applications in DroidSafe. In: Network and distributed system security symposium (NDSS). San Diego, CA, pp 8–11
Grace M, Zhou Y, Zhang Q, Zou S, Jiang X (2011) RiskRanker: scalable and accurate zero-day android malware detection. In: Proceedings of the 10th international conference on mobile systems, applications, and services. Low Wood Bay, Lake District, UK, pp 281–293
Grace M, Zhou Y, Wang Z, Jiang X (2012a) Systematic detection of capability leaks in stock android smartphones. In: Proceedings of the 19th network and distributed system security symposium (NDSS). San Diego, CA, pp 1–15
Grace MC, Zhou W, Jiang X, Sadeghi A-R (2012b) Unsafe exposure analysis of mobile in-app advertisements. In: proceeding 5th ACM conference on security and privacy in wireless and mobile networks, Tucson, Arizona. USA 67(2):101–112
Hou O. A Look at Google Bouncer. [Online]. Available: http://blog.trendmicro.com/trendlabs-security-intelligence/a-look-at-google-bouncer/. Accessed: 09-Sep-2016
Huang C-Y, Tsai Y-T, Hsu C-H (2013) Performance evaluation on permission-based detection for android malware. Smart Innov, Syst Technolo (SIST) 21:111–120
Huang J, Zhang X, Tan L, Wang P, Liang B (2014) AsDroid: detecting stealthy behaviors in android applications by user interface and program behavior contradiction. In: Proceeding ICSE 2014 proceedings of the 36th international conference on software engineering. Hyderabad, India, pp 1036–1046
I. T. Union. ICT FACTS AND FIGURES. [Online]. Available: http://www.itu.int/en/ITU-D/Statistics/Documents/facts/ICTFactsFigures2016.pdf
Ikinci A, Holz T, Freiling F (2008) Monkey-spider: detecting malicious websites with low-interaction Honeyclients. In: In proceedings of Sicherheit. Schutz und Zuverlässigkeit, Saarbrücker Schloss, German, pp 407–421
Junaid M, Liu D, Kung D (2016) Dexteroid: detecting malicious behaviors in android apps using reverse-engineered life cycle models. Comp Sec 59:92–117
Kang, H. Jang, J. Mohaisen A., and Kim, H. K. “Detecting and classifying android malware using static analysis along with creator information,” International Journal of Distributed Sensor Networks - Special issue on Advanced Big Data Management and Analytics for Ubiquitous Sensors, vol. 11, no. 6, pp. 1–17, 2015.
Karim, A. Salleh, R. Shiraz M., Shah S. A. A.. Awan, I and Anuar N. B., “Botnet detection techniques: review, future trends, and issues,” Journal of Zhejiang University-SCIENCE C (Computers & Electronics), vol. 15, no. 11, pp. 943–983, 2014.
Karim A, Salleh R, Khan MK (2016a) SMARTbot: a behavioral analysis framework augmented with machine learning to identify mobile botnet applications. PLoS One 11(3):1–35
Karim A, Salleh R, Khan MK, Siddiqa A, Choo K-KR (2016b) On the analysis and detection of mobile botnet. J Univ Comp Sci 22(4):567–588
Kasperksy. IT threat evolution Q3 2016 Statistics, 2016. [Online]. Available: https://securelist.com/analysis/quarterly-malware-reports/76513/it-threat-evolution-q3-2016-statistics/. Accessed: 15 Nov 2016
Kent JT (1982) Information gain and a general measure of correlation. Biometrika:163–173
Kotsiantis SB, Zaharakis ID, Pintelas PE (2006) Machine learning: a review of classification and combining techniques. Artif Intell Rev 26(2006):159–190
Lee S-H, Jin S-H (2013) Warning system for detecting malicious applications on android system. Intern J Comp Comm Eng 2(3):324–327
Lee J, Lee S, Heejo L (2015a) Screening smartphone applications using malware family signatures. Comp Sec 52:234–249
Liang S, Keep AW, Might M, Lyde S, Gilray T, Aldous P, Van Horn D (2013) Sound and precise malware analysis for android via pushdown reachability and entry-point saturation. In: ACM workshop on security and privacy in smartphones and mobile devices. Germany, Berlin, pp 21–32
Lippmann RP (1987) An introduction to computing with neural nets. IEEE ASSP Mag 4(2):4–22
Lu L, Li Z, Wu Z, Lee W, Jiang G (2012) CHEX: statically vetting android apps for component hijacking vulnerabilities. In: CCS proceedings of the ACM conference on computer and communications security. Raleigh, North Carolina, USA, pp 229–240
Luoshi Z, Yan N, Xiao W, Wang Z, Xue Y (2013) A3: automatic analysis of android malware. In: International workshop on cloud computing and information security (CCIS). Shanghai, China, pp 89–93
Marefat A, Noor RM, Anuar NB, Hussin N (2016) The feasibility of employing IEEE802.11P in electronic-based congestion pricing zone: a comparative study with RFID. Malaysian J Comp Sci 29(4):247–261
McAfee.McAfee Labs Threats Report. [Online]. Available: http://www.mcafee.com/us/resources/reports/rp-quarterly-threats-sep-2016.pdf
Narudin FA, Feizollah A, Anuar NB, Gani A (2014) Evaluation of machine learning classifiers for mobile malware detection. Soft Comput 20(1):343–357
Peiravian N, Zhu X (2013) Machine learning for android malware detection using permission and API calls. In: International conference on tools with artificial intelligence (ICTAI). Herndon, VA, USA, pp 300–305
Peng H, Gates C, Sarma B, Li N, Qi Y, Potharaju R, Nita-Rotaru C, Molloy I (2012) Using probabilistic generative models for ranking risks of android apps. In: ACM conference on computer and communications security, (CCS). Raleigh, North Carolina, pp 241–252
Rasthofer S, Arzt S, Bodden E (2014) A machine-learning approach for classifying and categorizing android sources and sinks. In: Symposium on network and distributed system security (NDSS). San Diego, CA, USA, pp 1–15
Razak MFA, Anuar NB, Salleh R, Firdaus A (2016) The rise of malware: Bibliometric analysis of malware study. J Netw Comput Appl 75:58–76
Russon M-A (2016) Android malware discovered on Google Play has infected millions of users with spyware. [Online]. Available: http://www.ibtimes.co.uk/android-malware-discovered-google-play-store-1553341. Accessed: 13 Jun 2016
Sahs J, Khan L (2012) A machine learning approach to android malware detection. In: European intelligence and security informatics conference, (EISIC). University of Southern Denmark Odense, Denmark, pp 141–147
Samra AAA, Kangbin Y, Ghanem OA (2013) Analysis of clustering technique in android malware detection. In: Seventh international conference on innovative mobile and internet Services in Ubiquitous Computing (IMIS). Taichung, Taiwan, pp 729–733
Sanz, B. Santos, I. Laorden, C. Ugarte-Pedrero, X, Bringas, P. G. and Alvarez, G. “PUMA: Permission Usage to detect Malware in Android,” in Advances in Intelligent Systems and Computing, 2013a, pp. 289–298.
Sanz B, Santos I, Laorden C, Ugarte-Pedrero X, Nieves J, Bringas PG, Álvarez Marañón G (2013b) Mama: manifest analysis for malware detection in android. Cybern Syst 44(6–7):469–488
Sarip AG, Hafez MB, Daud MN (2016) Application of fuzzy regression model for real estate price prediction. Malaysian Journal of Computer Science 29(1):15–27
Sarma B, Li N, Gates C, Potharaju R, Nita-rotaru C, Molloy I (2012) Android permissions: a perspective combining risks and benefits. In: SACMAT ‘12 proceedings of the 17th ACM symposium on access control models and technologies. USA, New Jersey, pp 13–22
Schmidt A, Schmidt H, Batyuk L, Clausen JH, Camtepe SA, Albayrak S, Yildizli C (2009a) Smartphone malware evolution revisited: android next target ? In: IEEE conference publications. Montreal, Quebec, pp 1–7
Schmidt A-D, Bye R, Schmidt H-G, Clausen J, Kiraz O, Yuksel KA, Camtepe SA, Albayrak S (2009b) Static analysis of Executables for collaborative malware detection on android. In: IEEE international conference on communications (ICC). Dresden, Germany, pp 1–5
Schneider J (2016) Cross Validation. [Online]. Available: http://www.cs.cmu.edu/~schneide/tut5/node42.html. Accessed: 01-Aug-2016
Seo S-H, Gupta A, Mohamed Sallam A, Bertino E, Yim K (2014) Detecting mobile malware threats to homeland security through static analysis. J Netw Comput Appl 38:43–53
Shabtai A, Fledel Y, Elovici Y (2010) Automated static code analysis for classifying android applications using machine learning. In: Ninth international conference on computational intelligence and security. Nanning, Guangxi Zhuang Autonomous Region China, pp 329–333
Shabtai A, Kanonov U, Elovici Y, Glezer C, Weiss Y (2011) ‘Andromaly’: a behavioral malware detection framework for android devices. J Intell Inf Syst 38(1):161–190
Shannon, C. E. “A mathematical theory of communication,” The Bell System Technical Journal, vol. 27, no. July 1928, pp. 379–423, 1948.
Sharif M, Yegneswaran, V. Saidi, H Porras, P. and Lee, W. “Eureka: A framework for enabling static malware analysis,” in Lect Notes Comput Sci, vol. 5283, 2008, pp. 481–500.
Sheen S, Anitha R, Natarajan V (2015) Android based malware detection using a multifeature collaborative decision fusion approach. Neurocomputing 151:905–912
Suarez-Tangil G, Tapiador JE, Peris-Lopez P, Blasco J (2014) Dendroid: a text mining approach to analyzing and classifying code structures in android malware families. Expert Syst Appl 41(4):1104–1117
Symantec. Symantec Intelligence Report. [Online]. Available: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence-report-01-2015-en-us.pdf
Talha KA, Alper DI, Aydin C (2015) APK auditor: permission-based android malware detection system. Digit Investig 13:1–14
VirusTotal (2016) VirusTotal. [Online]. Available: https://www.virustotal.com/. Accessed: 24-Aug-2016
Waikato U. Weka 3: Data Mining Software in Java. [Online] 2017. Available: http://www.cs.waikato.ac.nz/ml/weka/
Walczak B, Massart DL (2000) Local modelling with radial basis function networks. Chemom Intell Lab Syst 50(2):179–198
Walenstein A, Deshotels L, Lakhotia A (2012) Program structure-based feature selection for android malware analysis. In: Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol. 107, pp. 51–52
Williams G (2010) ARFF Data. [Online]. Available: http://datamining.togaware.com/survivor/ARFF_Data0.html. Accessed: 10-Sep-2015
Wu D-J, Mao C-H, Wei T-E, Lee H-M, Wu K-P (2012) DroidMat: android malware detection through manifest and API calls tracing. In: Seventh Asia joint conference on information security. Tokyo, Japan, pp 62–69
Yang Z, Yang M (2012) Leak miner: detect information leakage on android with static taint analysis. In: Third world congress on software engineering (WCSE). Wuhan, China, pp 101–104
Yerima SY, Sezer S, McWilliams G, Muttik I (2013) A new android malware detection approach using Bayesian classification. In: IEEE 27th international conference on advanced information networking and applications (AINA). Barcelona, Spain, pp 121–128
Yerima SY, Sezer S, McWilliams G (2014a) Analysis of Bayesian classification-based approaches for android malware detection. IET Inf Secur 8(1):25–36
Yerima SY, Sezer S, Muttik I (2014b) Android malware detection using parallel machine learning classifiers. In: Eight international conference on next generation mobile apps, services and technologies, (NGMAST). Anthony’s College of the University of Oxford, St, pp 37–42
Yerima SY, Sezer S, Muttik I (2015) High accuracy android malware detection using ensemble learning. IET Inf Secur 9(6):313–320
Yu L, Liu H (2004) Efficient feature selection via analysis of relevance and redundancy. J Mach Learn Res 5:1205–1224
Zhongyang Y, Xin Z, Mao B, Xie L (2013) DroidAlarm: an all-sided static analysis tool for android privilege-escalation malware. In: ASIA CCS ‘13 proceedings of the 8th ACM SIGSAC symposium on information, computer and communications security. Hangzhou, China, pp 353–358
Zhou Y, Jiang X (2012) Android Malware Genome Project. [Online]. Available: http://www.malgenomeproject.org/
Zhou W, Zhou Y, Jiang X, Ning P (2012) Detecting repackaged smartphone applications in third-party android marketplaces. In: CODASPY ‘12 proceedings of the second ACM conference on data and application security and privacy. San Antonio, Texas, USA, pp 317–326
Zhou W, Zhou Y, Grace M, Jiang X, Zou S (2013) Fast, scalable detection of ‘piggybacked’ mobile applications. In: CODASPY ‘13 proceedings of the second ACM conference on data and application security and privacy. San Antonio, Texas, pp 185–195
Zia T, Akhter MP, Abbas Q (2015) Comparative study of feature selection Aapproaches for Urdu text categorization. Malaysian Journal of Computer Science 28(2):93–109
Acknowledgements
This work was supported by the Ministry of Science, Technology and Innovation, under the Grant eScienceFund 01-01-03-SF0914.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Funding
This study was funded by eScienceFund (grant number 01–01-03-SF0914).
Conflict of interest
Ahmad Firdaus, Nor Badrul Anuar, Mohd Faizal Ab Razak and Arun Kumar Sangaiah declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Rights and permissions
About this article
Cite this article
Firdaus, A., Anuar, N.B., Razak, M.F.A. et al. Bio-inspired computational paradigm for feature investigation and malware detection: interactive analytics. Multimed Tools Appl 77, 17519–17555 (2018). https://doi.org/10.1007/s11042-017-4586-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4586-0