Abstract
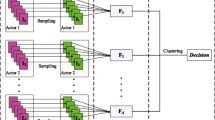
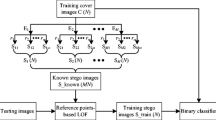
This work proposes a new unsupervised steganalysis scheme which mainly tackles the challenge in identifying individual JPEG image as stego or cover. The proposed scheme does not need a large number of samples to train classification model, and thus it is significantly different from the existing supervised steganalysis schemes. The proposed scheme employs calibration technology to construct multiple reference images from one suspicious image. These reference images are considered as the imitation of cover. Furthermore, randomized sampling is performed to construct sub-image sets from suspicious image and reference images, respectively. By calculating the maximum mean discrepancy between any two sub-image sets, an efficient measure is provided to give the optimal decision on this suspicious image. Experimental results show that the proposed scheme is effective and efficient in identifying individual image, and outperforms the state-of-the-art steganalysis scheme.






Similar content being viewed by others
Notes
We assume that the images from the same camera have the same noise distribution.
A fixed cropped size is used to show the overall performance of proposed scheme, although there might exist an optimal range for the cropped size m×n for the recent image database.
In fact, D value can be changed in smaller steps, e.g. 0.01 step.
Since the scale of training set can potentially affect the matching degree of generalized classification model in supervised schemes and further affect the accuracy of classification, we tend to use the same number of images as the training set to show a fair comparison.
References
Böhme R (2007) Weighted stego-image steganalysis for JPEG covers. 10th International Workshop on information hiding, Barbara, USA, May 19-21, 5284:178-194
Chang C, Lin C (2001) LIBSVM: a library for support vector machines 2001. Software available at http://www.csie.ntu.edu.tw/~cjlin/libsvm
Cogranne R, Zitzmann C, Retraint F, Nikiforov I, Cornu P, Fillatre L (2014) A local adaptive model of natural images for almost optimal detection of hidden data. Elsevier Signal Process 100:169–185
Denemark T, Fridrich J, Holub V (2014) Further study on security of S-UNIWARD. Proceedings of SPIE, Electronic Imaging, Media Watermarking, Security, and Forensics, 9028, San Francisco, CA, February 2-6
Fridrich J, Kodovský J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur 7(3):868–882
Fridrich J, Goljan M, Hogea D (2002) Steganalysis of JPEG images: breaking the F5 algorithm, 5th International Workshop on information hiding, Noordwijkerout, Netherlands, October 7-9, 2578:310–323
Fridrich J, Pevný T, Kodovský J (2007) Statistically undetectable JPEG steganography: dead ends, challenges, and opportunities. Proceedings of the 9th ACM multimedia \& security Workshop, Dallas, TX, September 20-21, pp 3–14
Gretton A, Borgwardt K, Rasch M, Scholkopf B, Smola A (2007) A kernel method for the two-sample-problem. Adv Neural Inf Proces Syst 19, MIT press, Cambridge, 513-520
Hetzl S, Mutzel P (2005) A graph-theoretic approach to steganography. Proceedings of 9th IFIP TC-6 TC-11 Internetional conference on communications and multimedia security, Salzburg, Austria, September 19-21, 3677:119-128
Holub V, Fridrich J (2013) Random projections of residuals for digital image steganalysis. IEEE Trans Inf Forensics Secur 8(12):1996–2006
JSteg algorithm. Available from: http://zooid.org/%7epaul/crypto/jsteg/. Accessed on 2011
Ker A, Pevný T (2011) A new paradigm for steganalysis via clustering. Proc SPIE, Media Watermarking, Secur, Forensics III 7880:78800U
Ker A, Pevný T (2012) Identifying a steganographer in realistic and hereogeneous data sets. Proc SPIE, Media Watermarking, Secur, Forensics XIV 8303:N01–N13
Ker A, Pevný T (2014) The steganographer is the outlier: realistic large-scale steganalysis. IEEE Trans Inf Forensics Secur 9(9):1424–1435
Kodovský J, Fridrich J (2009) Calibration revisited. Proceedings of the 11th ACM multimedia \& security Workshop, 63-74
Kodovský J, Fridrich J (2010) Quantitative structural steganalysis of Jsteg. IEEE Trans Inf Forensics Secur 5(4):681–693
Li F, Zhang X, Cheng H, Yu J (2016) Digital image steganalysis based on local textural features and double dimensionality reduction. Secur Commun Netw 9(8):729–736
Li F, Wu K, Lei J, Wen M, Bi Z, Gu C (2016) Steganalysis over large-scale social networks with high-order joint features and clustering ensembles. IEEE Trans Inf Forensics Secur 11(2):344–357
Li F, Wu K, Lei J, Wen M, Cao Y, Jin T (2016) Multi-source stego detection with local textural feature and clustering ensembles. Technical Report, Sept., 2016
[Online]. http://www.instagram.com. Accessed on March 2016
[Online]. Available: http://exile.felk.cvut.cz/boss/BOSSFinal/
[Online]. Available: http://dde.binghamton.edu/download/
[Online]. http://www.flickr.com. Accessed on March 2016
Pevný T, Fridrich J (2007) Merging markov and DCT features for multi-class JPEG Steganalysis. Proceedings of SPIE, Electronic imaging, security, steganography, and Watermarking of multimedia contents IX, San Jose, CA, January 29- February 1, 6505: 3 1-3 14
Pevný T, Bas P, Fridrich J (2010) Steganalysis by subtractive pixel adjacency matrix. IEEE Trans Inf Forensics Secur 5(2):215–224
Qiao T, Retraint F, Cogranne R, Zitzmann C (2015) Steganalysis of JSteg algorithm using hypothesis testing theory. EURASIP J Inf Secur 2(1):1–16
Qin C, Hu Y (2016) Reversible data hiding in VQ index table with lossless coding and adaptive switching mechanism. Signal Process 129:48–55
Shi Y, Chen C, Chen W (2006) A markov process based approach to effective attacking JPEG steganography, 8th International Workshop on information hiding, Alexandria, VA, July 10-12, 4437: 249–264
Thai T, Cogranne R, Retraint F (2014) Statistical model of quantized DCT coefficients: application in the steganalysis of Jsteg algorithm. IEEE Trans Image Process 23(5):1980–1993
Westfeld A (2001) High capacity despite better steganalysis (F5-a steganographic algorithm). Proceedings of 4th International Workshop on information hiding. Pittsburgh, PA, April 25-27, pp 289–302
Xia Z, Wang X, Sun X, Wang B (2014) Steganalysis of least significant bit matching using multi-order differences. Secur Commun Netw 7(8):1283–1291
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2016) Steganalysis of LSB matching using differences between nonadjacent pixels. Multimed Tools Appl 75(4):1947–1962
Zhang T, Ping X (2003) A fast and effective steganalytic technique against Jsteg-like algorithm. Proceedings of the ACM Symposium on Applied Computing, New York, USA, 307–311
Acknowledgments
This work was supported by Natural Science Foundation of China under Grants (No. 61602295, 61373152, 61672337, 61572311, 61572309, and 61472236), Natural Science Foundation of Shanghai (No. 16ZR1413100), the Scientific Research Foundation of Shanghai University of Electric Power (No. K2015-010), the Excellent University Young Teachers Training Program of Shanghai Municipal Education Commission (No. ZZsdl15105), Project of Shanghai Science and Technology Committee (14110500800) and the “Dawn” Program of Shanghai Education Commission (No. 16SG47).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, F., Wu, K., Lei, J. et al. Unsupervised steganalysis over social networks based on multi-reference sub-image sets. Multimed Tools Appl 77, 17953–17971 (2018). https://doi.org/10.1007/s11042-017-4759-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4759-x