Abstract
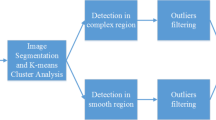
In this paper, we propose a new multi-granularity superpixels matching based algorithm for the accurate detection and localization of copy-move forgeries, which integrated the advantages of keypoint-based and block-based forgery detection approaches. Firstly, we divide the original tempted image into non-overlapping and irregular coarse-granularity superpixels, and the stable image keypoints are extracted from each coarse-granularity superpixel. Secondly, the superpixel features, which is quaternion exponent moments magnitudes, are extracted from each coarse-granularity superpixel, and we find the matching coarse-granularity superpixels (suspected forgery region pairs) rapidly using the Exact Euclidean Locality Sensitive Hashing (E2LSH). Thirdly, the suspected forgery region pairs are further segmented into fine-granularity superpixels, and the matching keypoints within the suspected forgery region pairs are replaced with the fine-granularity superpixels. Finally, the neighboring fine-granularity superpixels are merged, and we obtain the detected forgery regions through morphological operation. Compared with the state-of-the-art approaches, extensive experimental results, conducted on the public databases available online, demonstrate the good performance of our proposed algorithm even under a variety of challenging conditions.
















Similar content being viewed by others
References
Amerini I, Ballan L, Caldelli R et al (2013) Copy-move forgery detection and localization by means of robust clustering with J-linkage. Signal Process Image Commun 28(6):659–669
Ardizzone E, Bruno A, Mazzola G (2015) Copy-move forgery detection by matching triangles of keypoints. IEEE Trans Inf Forensics Secur 10(10):2084–2094
Bi X, Pun CM, Yuan XC (2016) Multi-level dense descriptor and hierarchical feature matching for copy-move forgery detection. Inf Sci 345:226–242
Chen L, Lu W, Ni J et al (2013) Region duplication detection based on Harris corner points and step sector statistics. J Vis Commun Image Represent 24(3):244–254
Chen B, Yang J, Jeon B, Zhang X (2017) Kernel quaternion principal component analysis and its application in RGB-D object recognition. Neurocomputing. doi:10.1016/j.neucom.2017.05.047
Christlein V, Riess C, Jordan J et al (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inf Forensics Secur 7(6):1841–1854
Costanzo A, Amerini I, Caldelli R et al (2014) Forensic analysis of SIFT keypoint removal and injection. IEEE Trans Inf Forensics Secur 9(9):1450–1464
Cozzolino D, Poggi G, Verdoliva L (2014) Copy-move forgery detection based on patchmatch. 2014 I.E. International Conference on Image Processing (ICIP), Paris, France, 5312–5316
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copy–move forgery detection. IEEE Trans Inf Forensics Secur 10(11):2284–2297
Geusebroek JM, Van den Boomgaard R, Smeulders AWM et al (2001) Color invariance. IEEE Trans Pattern Anal Mach Intell 23(12):1338–1350
Jiang YJ (2011) Exponent moments and its application in pattern recognition. Beijing University of Posts and Telecommunications, Beijing
Lee JC (2015) Copy-move image forgery detection based on Gabor magnitude. J Vis Commun Image Represent 31:320–334
Lee JC, Chang CP, Chen WK (2015) Detection of copy–move image forgery using histogram of orientated gradients. Inf Sci 321:250–262
Li J, Li X, Yang B et al (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forensics Secur 10(3):507–518
Li Y, Wang S, Tian Q et al (2015) A survey of recent advances in visual feature detection. Neurocomputing 149:736–751
Lim WQ (2010) The discrete shearlet transform: a new directional transform and compactly supported shearlet frames. IEEE Trans Image Process 19(5):1166–1180
Liu M, Tuzel O, Ramalingam S, Chellappa R (2011) Entropy rate superpixel segmentation. Proceedings of the IEEE Conference on Computer Vision and Pattern
Mainali P, Lafruit G, Yang Q et al (2013) SIFER: scale-invariant feature detector with error resilience. Int J Comput Vis 104(2):172–197
Pan X, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inf Forensics Secur 5(4):857–867
Pandey R, Singh S, Shukla K (2016) Passive forensics in image and video using noise features: a review. Digit Investig 19:1–28
Pun CM, Yuan XC, Bi XL (2015) Image forgery detection using adaptive oversegmentation and feature point matching. IEEE Trans Inf Forensics Secur 10(8):1705–1716
Qureshi M, Deriche M (2015) A bibliography of pixel-based blind image forgery detection techniques. Signal Process Image Commun 39:46–74
Ryu SJ, Kirchner M, Lee MJ et al (2013) Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Trans Inf Forensics Secur 8(8):1355–1370
Silva E, Carvalho T, Ferreira A et al (2015) Going deeper into copy-move forgery detection: exploring image telltales via multi-scale analysis and voting processes. J Vis Commun Image Represent 29:16–32
Wang X, Niu P, Yang H et al (2014) A new robust color image watermarking using local quaternion exponent moments. Inf Sci 277:731–754
Wang J, Li T, Shi Y-Q, Lian S, Ye J (2016) Forensics feature analysis in quaternion wavelet domain for distinguishing photographic images and computer graphics. Multimed Tool Appl. doi:10.1007/s11042-016-4153-0
Wu Q, Wang S, Zhang X (2011) Log-polar based scheme for revealing duplicated regions in digital images. IEEE Signal Process Lett 18(10):559–562
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(11):2594–2608
Xiang-yang W, Yu-nan L, Huan X, Pei W, Hong-ying Y Robust copy-move forgery detection using quaternion exponent moments. Pattern Anal Applic. doi:10.1007/s10044-016-0588-1
Yu L, Han Q, Niu X (2016) Feature point-based copy-move forgery detection: covering the non-textured areas. Multimedia Tools Appl 75(2):1159–1176
Zandi M, Mahmoudi-Aznaveh A, Talebpour A (2016) Iterative copy-move forgery detection based on a new interest point detector. IEEE Trans Inf Forensics Secur 11(11):2499–2512
Zhang R, Wei F, Li B (2014) E2LSH based multiple kernel approach for object detection. Neurocomputing 124:105–110
Zhili Z, Ching-Nung Y, Xingming S et al (2016) Effective and efficient image copy detection with resistance to arbitrary rotation. IEICE Trans Inf Syst 99(6):1531–1540
Zhou Z, Wang Y, Wu Q et al (2017) Effective and efficient global context verification for image copy detection. IEEE Trans Inf Forensics Secur 12(1):48–63
Zong T, Xiang Y, Natgunanathan I et al (2015) Robust histogram shape-based method for image watermarking. IEEE Trans Circuits Syst Video Technol 25(5):717–729
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grant No. 61472171 & 61272416, the Natural Science Foundation of Liaoning Province of China under Grant No. 201602463, A Project Funded by the Priority Academic Program Development of Jiangsu Higher Education Institutions, and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology.
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Yang, Hy., Niu, Y., Jiao, Lx. et al. Robust copy-move forgery detection based on multi-granularity Superpixels matching. Multimed Tools Appl 77, 13615–13641 (2018). https://doi.org/10.1007/s11042-017-4978-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4978-1