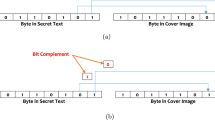
Abstract
Similar to the Internet, the IoT also faces numerous information security issues. Because the multimedia sensors that form Wireless Multimedia Sensor Networks (WMSNs) inherently operate with large amounts of data with high redundancy, steganography appears to be a better way to ensure the security of information in this medium than does cryptography. Considering that computing power and energy resources are often limited in the IoT, it is more effective and feasible to use steganography to obtain the outcomes that people expect, including better concealment and security. Currently, some advanced steganalysis techniques can reliably detect embedded secret messages, To defend against such steganalysis techniques, most scholars in this field have focused on developing or improving advanced embedding algorithms. However, in this article, choosing a suitable carrier is also considered to be a good approach to improve resistance. Thus, this paper proposes the Maximum Matching Degree(MMD) sifting algorithm, which is based on the principle of " minimizing the effect of embedding" (here, we measure the effect of embedding by the number of modified bits) and can be applied to choose the best carrier by minimizing the number of bits that will be modified during embedding. This approach can be regarded as a steganography pretreatment. Moreover, it is easy to implement, which is also important in IoT situations. Using greyscale-images as carriers, we conducted experiments. The results demonstrated that the pretreatment method not only improves embedding efficiency and steganalysis resistance (to some common steganalysis techniques) but is also extremely versatile. This result has significant implications for steganography and broad implementation prospects.







Similar content being viewed by others
References
Amin R, Kumar N, Biswas GP, Iqbal R, Chang V (2016) A light weight authentication protocol for IoT-enabled devices in distributed cloud computing environment[J]. Futur Gener Comput Syst. doi:10.1016/j.future.2016.12.028
Atamli AW, Martin A. (2014) Threat-based security analysis for the internet of things. In Secure Internet of Things (SIoT), 2014 International Workshop on, pp. 35-43
Avcibas I, Memon N, Sankur B (2002) Steganalysis using image quality metrics[C]. IEEE Trans Image Process 12(2):221–229
Aydogdu I, Abualrub T, Siap I (2015) On double-struck capital Z(2)Double-Struck capital Z(2)[u]-additive codes[J]. Int J Comput Math 92(9):1806–1814
Bairagi, Anupam Kumar; Khondoker, Rahamatullah; Islam, Rafiqul. An efficient steganographic approach for protecting communication in the Internet of Things (IoT) critical infrastructures[C]. Inf Secur J, p 1–16, 2016; ISSN: 19393555, E-ISSN: 19393547; doi:10.1080/19393555.2016.1206640; Publisher: Taylor and Francis Inc.
Bhattasali T (2013) LICRYPT: Lightweight Cryptography Technique for Securing Smart Objects in Internet of Things Environment. CSI Communication pp 26–28
Bohan Z, Xu W, Kaili Z, Xueyuan Z (2013) "Encryption node Design in Internet of things based on fingerprint features and CC2530," in Green computing and communications (GreenCom), 2013 I.E. and internet of things (iThings/CPSCom), IEEE International Conference on and IEEE Cyber, Physical and Social Computing, pp. 1454–1457
Chang V (2015) Towards a big data system disaster recovery in a private cloud[J]. Ad Hoc Netw 35:65–82
Chang V, Kuo Y-H, Ramachandran M (2016) Cloud computing adoption framework: a security framework for business clouds[J]. Futur Gener Comput Syst 57:24–41
Fridrich J (2010) Steganography in Digital Media Principles, Algorithms, and Applications[M]. Cambridge University Press, New York, pp. 1–20
Gul F, Kurugollu F (June 2010) SVD-based universal spatial domain image Steganalysis[C]. IEEE Trans Inf Forensics Secur 5(2):349–353
Harjito B (2010) Secure communication in wireless multimedia sensor networks using watermarking[C]. In 4th IEEE International Conference on Digital Ecosystems and Technologies, Dubai, United Arab Emirates, 640–645
Hu M, Yang Y*, Shen F, Zhang L, Tao Shen H and Li X (2017) Robust web image annotation via exploring multi-facet and structural knowledge. IEEE Trans Image Process 26(10):4871–4884
Jaheel HL, Beiji Z (2015) A Novel Approach Of Combiningsteganography Algorithms[J]. Int J Smart Sensing Intell Syst 8(1):90–106
Jessica F, Miroslav G, Rui D (2001) Detecting LSB steganography in color and gray-scale images[J]. IEEE Trans Multimedia 8(4):22–28
Jiang N, Wang L (2015) A Novel Strategy for Quantum Image SteganographyBased on Moire Pattern[J]. Int J Theor Phys 54(3):1021–1032
Kanan HR, Nazeri B (2014) A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm[J]. Expert Syst Appl 41(14):6123–6130
Katagi M and Moriai S (2008) Lightweight cryptography for the internet of things. Sony Corporation, pp 7–10
Kim, Sung Ryoung; Kim, Jeong Nyeo; Kim, Sung Tae; Shin, Sunwoo; Yi, Jeong Hyun. Anti-reversible dynamic tamper detection scheme using distributed image steganography for IoT applications[C]. J Supercomput, p 1–20, 2016; ISSN: 09208542, E-ISSN: 15730484; doi:10.1007/s11227-016-1848-y; Publisher: Springer New York LLC
Lee J-Y, Lin W-C, Huang Y-H (2014) "A lightweight authentication protocol for internet of things," in Next-Generation Electronics (ISNE), 2014 International Symposium on, pp. 1-2
Liu JF, Tian YG, Han T, Yang CF, Liu WB (2015) LSB steganographic payload location for JPEG-decompressed images[J]. Digit Signal Process 38:66–77
Luo Y, Yang Y*, Shen F, Huang Z, Zhou P and Tao Shen H (2017) Robust discrete code modeling for supervised hashing. Pattern Recogn. doi:10.1016/j.patcog.2017.02.034
Lyu S, and H. Farid. Detecting messages using higher-order statistics and support vector machines[C] in Proceedings of 5th International Workshop on Inforrmation Hiding(IH'2002)(F.A. P. Petitcolas, ed.), vol. 2578, pp. 340–354, Springer-Verlag, 2003
Pennerbasker W, Mitchell J (1993) JPEG: Still Image Data Compression Standard[M]. Van Nostrand Reinhold, New York
Provos N (2001) Defending against statistical steganalysis[C]. In 10th USENIX Security Symposium, Washington, DC, 323–335
Roman R, Zhou JY and Lopez J (2013) On the features and challenges of security and privacy in distributed internet of things[J]. Comput Netw 57(10):2266–2279
Schneier B (1996) Applied Cryptography[M]. Wiley, New York
Sun G, Xie Y, Liao D, Yu H, Chang V (2017) User-defined privacy location-sharing system in mobile online social network[J]. J Netw Comput Appl 86:34–35
Tiwari N, Shandilya DM (2010) Evaluation of various LSB based methods of image steganography on GIF file format[J]. Int J Comput Appl 6(2):1–4
Touati L, Challal Y, Bouabdallah A (2014) "C-CP-ABE: Cooperative Ciphertext Policy Attribute-Based Encryption for the Internet of Things," in Advanced Networking Distributed SYSTEMS and Applications (INDS), 2014 International Conference on, pp. 64-69
Turner C (2009) A Steganographic computational paradigm for wireless sensor networks[C]. In International Conference on Innovations in Information Technology, Al-Ain, United Arab Emirates, 258–262
Wang S, Sang JZ, Song XH, Niu XM (2015) Least significant qubit (LSQb) information hiding algorithm for quantum image[J]. Measurement 73:352–359
Wang Z, Cao C, Yang N, Chang V (2016) ABE with improved auxiliary input for big data security[J]. J Comput Syst Sci 89(2017):41–50
Xia ZH, Wang XH, Sun XM, Liu QS, Xiong NX (2016) Steganalysis of LSB matching using differences between nonadjacent pixels[J]. Multimed Tools Appl 75(4):1947–1962
Yan XH, Wang S, Abd El-Latif AA, Niu XM (2015) New approaches for efficient information hiding-based secret image sharing schemes[J]. Signal ImageVideo Process 9(3):499–510
Yang Y, Zha Z-J, Gao Y, Zhu X, Chua T-S (2014) Exploiting web images for semantic video indexing via robust sample-specific loss. IEEE Trans Multimedia 16(6):1677–1689
Yang Y, Shen F, Tao Shen H, Li H, Li X (2016) Robust discrete spectral hashing for large-scale image semantic indexing. IEEE Trans Big Data 1(4):162-171
Yang Y, Ma Z, Yang Y, Nie F, Tao Shen H (2015) Multitask spectral clustering by exploring Intertask correlation. IEEE Trans Cybern 45(5):1083–1094
Yang Y, Shen F, Huang Z, Tao Shen H, Li X (2017) Discrete nonnegative spectral clustering. IEEE Trans Knowl Data Eng 29(9):1834–1845
Yin JHJ, Fen GM, Mughal F, Iranmanesh V (2015) Internet of things: Securing data using image steganography[C]. Proceedings - AIMS 2015, 3rd International Conference on Artificial Intelligence, Modelling and Simulation. doi:10.1109/AIMS.2015.56
Funding
This work is funded by: European Seventh Framework Program (FP7) under Grant No. GA-2011-295222, and by National Natural Science Foundation of China under Grant No. 61073009, and by National Sci-Tech Support Plan of China under Grant No. 2014BAH02F03,and by National Key R&D Plan of China under Grant No. 2017YFA0604500, National Sci-Tech Support Plan of China under Grant No. 2014BAH02F00, and by Youth Science Foundation of Jilin Province of China under Grant No. 20160520011JH, and by Youth Sci-Tech Innovation Leader and Team Project of Jilin Province of China under GrantNo. 20170519017JH.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, H., Hu, L., Chu, J. et al. The maximum matching degree sifting algorithm for steganography pretreatment applied to IoT. Multimed Tools Appl 77, 18203–18221 (2018). https://doi.org/10.1007/s11042-017-5075-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5075-1