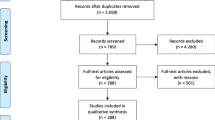
Abstract
This paper presents an innovative technique to find out the most influential challenge faced by big data. Presently, the key challenges faced by big data are security, privacy, and accuracy. To prioritize the most influential factor among the three, we need to select the suitable factor that accomplishes our objectives within the available resources. In this study, we propose the Analytic Network Process (ANP) technique for evaluating these challenges. The study also appraises the ANP model in comparison with the priorities of all competing challenges inside the big data. The secondary data has been taken for the ANP analysis from numerous scholarly articles focusing on big data. In our analysis, we have proposed a policy assessment of the relation between big data characteristics and the challenges; it further prioritizes the consequent results for the most influential challenge by using ANP model. The empirical results conclude that the security has the highest influence value i.e. 54% of the total measurement, while privacy and accuracy stand second and third among the most influential factors with 36% and 8% values respectively. Finally, the study provides important clues in the decision-making process in finding the solutions to such challenges faced by big data.









Similar content being viewed by others
Notes
The eigenvector is defined as, “It is a vector whose direction remains unchanged when a linear transformation is applied to it”. It has many applications in computer vision and machine learning.
References
Acker O, Blockus A, Pötscher F (2013) Benefiting from big data: a new approach for the telecom industry. Strategy & Analysis Report
Agrawal D, El Abbadi A, Wang S (2013) Secure and privacy-preserving database services in the cloud. In: Data Engineering (ICDE), 2013 I.E. 29th International Conference on. IEEE, pp 1268–1271
Ahmed ESA, Saeed RA (2014) A Survey of big data cloud computing security. Int J Comput Sci Softw Eng (IJCSSE) 3:78–85
Ahmed F, Naeem M, Iqbal M (2016) ICT and renewable energy: a way forward to the next generation telecom base stations. Telecommun Syst:1–14. https://doi.org/10.1007/s11235-016-0156-4
Ammu N, Irfanuddin M (2013) Big data challenges. Int J Adv Trends Comput Sci Eng 2:613–615
Andreichicova ON, Radyshevskaya TN (2009) An application of the Analytic Network Process to researching oral health. Int J Analytic Hierarchy Process 1(1):45–60
Angello C, Wema E (2010) Availability and usage of ICTs and e-resources by livestock researchers in Tanzania: challenges and ways forward. Int J Educ Dev Inf Commun Technol 6(1):A34
Bello-Orgaz G, Jung JJ, Camacho D (2016) Social big data: Recent achievements and new challenges. Information Fusion 28:45–59
Brynjolfsson E, McAfee A (2014) The second machine age: work, progress, and prosperity in a time of brilliant technologies. WW Norton & Company
Butler M (2011) Android: changing the mobile landscape. IEEE Pervasive Comput. https://doi.org/10.1109/MPRV.2011.1
Castells M (2011) The rise of the network society: the information age: economy, society, and culture, vol 1. Wiley
Chen CLP, Zhang C-Y (2014) Data-intensive applications, challenges, techniques and technologies: a survey on big data. Inf Sci 275:314–347
Chen M, Mao S, Liu Y (2014) Big data: a survey. Mob Netw Appl 19(2):171–209
Chen J, Song X, Nie L, Wang X, Zhang H, Chua TS (2016) Micro tells macro: predicting the popularity of micro-videos via a transductive model. In: Proceedings of the 2016 ACM on Multimedia Conference. ACM, pp 898-907
Colombo P, Ferrari E (2015) Privacy aware access control for big data: a research roadmap. Big Data Res 2(4):145–154
Cuzzocrea A (2014) Privacy and security of big data: current challenges and future research perspectives. In: Proceedings of the First International Workshop on Privacy and Secuirty of Big data. ACM, pp 45–47
Cuzzocrea A, Saccà D (2010) Balancing accuracy and privacy of OLAP aggregations on data cubes. In: Proceedings of the ACM 13th international workshop on Data warehousing and OLAP. ACM, pp 93–98
Data, IBM Big (2015) IBM-bringing big data to the enterprise
De Mauro A, Greco M, Grimaldi M (2015) What is big data? A consensual definition and a review of key research topics. In: AIP Conference Proceedings, vol 1644, 1, pp 97–104
Dong Y, Zhang G, Hong W-C, Xu Y (2010) Consensus models for AHP group decision making under row geometric mean prioritization method. Decis Support Syst 49(3):281–289
Douglas L (2001) 3d data management: controlling data volume, velocity and variety. Gartner Retrieved 6:2001
Dumbill E (2013) Making sense of big data. Big Data 1(1):1–2
Ellaway RH, Pusic MV, Galbraith RM, Cameron T (2014) Developing the role of big data and analytics in health professional education. Med Teach 36(3):216–222
Fisher D, DeLine R, Czerwinski M, Drucker S (2012) Interactions with big data analytics. Interactions 19(3):50–59
Garuti C, Sandoval M (2005) Comparing AHP and ANP shiftwork models: hierarchy simplicity v/s network connectivity. In: Proceedings of the 8th international Symposium of the AHP
Hashem IAT, Chang V, Anuar NB, Adewole K, Yaqoob I, Gani A, Ahmed E, Chiroma H (2016) The role of big data in smart city. Int J Inf Manag 36(5):748–758
Herold R (2002) What is the difference between security and privacy. InformationShield
Hilbert M (2014) What is the content of the world's technologically mediated information and communication capacity: how much text, image, audio, and video? Inf Soc 30(2):127–143
Hilbert M (2016) Big data for development: a review of promises and challenges. Dev Policy Rev 34(1):135–174
Hilbert M, López P (2011) The world’s technological capacity to store, communicate, and compute information. Science 332(6025):60–65
Hurwitz J, Nugent A, Halper F, Kaufman M (2013) Big data for dummies. Wiley
Iqbal R, Doctor F, More B, Mahmud S, Yousuf U (2016) Big data analytics: computational intelligence techniques and application areas. Int J Inf Manag
Jensen M (2013) Challenges of privacy protection in big data analytics. In: Proceedings-2013 Ieee International Congress on Big Data, Bigdata 2013. IEEE
Jin X, Wah BW, Cheng X, Wang Y (2015) Significance and challenges of big data research. Big Data Res 2(2):59–64
Kaisler S, Armour F, Alberto Espinosa J, Money W. (2013) Big data: issues and challenges moving forward. In: System Sciences (HICSS), 2013 46th Hawaii International Conference on. IEEE, pp 995–1004
Khalafzai AK, Nirupama N (2011) Building resilient communities through empowering women with information and communication technologies: a Pakistan case study. Sustainability 3(1):82–96
Kim G-H, Trimi S, Chung J-H (2014) Big-data applications in the government sector. Commun ACM 57(3):78–85
Kshetri N (2014) The emerging role of big data in key development issues: opportunities, challenges, and concerns. Big Data Soc 1(2):2053951714564227
Kshetri N (2016) Big data’s role in expanding access to financial services in China. Int J Inf Manag 36(3):297–308
Kwon TH, Kwak JH, Kim K (2015) A study on the establishment of policies for the activation of a big data industry and prioritization of policies: lessons from Korea. Technol Forecast Soc Chang 96:144–152
Lad AP, Shah SA Big data–a pool of opportunities and negotiations: forseen and unforseen
Laney D (2001) 3D data management: controlling data volume, velocity and variety. META Group Res Note 6:70
Letouzé E (2012) Big datafor development: what may determine success or failure
Li M, Zang W, Bai K, Yu M, Liu P (2013) MyCloud: supporting user-configured privacy protection in cloud computing. In: Proceedings of the 29th Annual Computer Security Applications Conference. ACM, pp 59–68
Liu Y, Nie Li, Han L, Zhang L, Rosenblum DS (2015) Action2Activity: recognizing complex activities from sensor data. Paper presented at the Proceedings of the 24th International Conference on Artificial Intelligence, Buenos Aires, Argentina
Liu L, Cheng L, Liu Y, Jia Y, Rosenblum DS (2016) Recognizing complex activities by a probabilistic interval-based model. In: AAAI, vol 30, pp 1266–1272
Liu Y, Zhang L, Nie L, Yan Y, Rosenblum DS (2016) Fortune teller: predicting your career path. Paper presented at the AAAI
Liu Y, Zheng Y, Liang Y, Liu S, Rosenblum DS (2016) Urban water quality prediction based on multi-task multi-view learning. Paper presented at the Proceedings of the International Joint Conference on Artificial Intelligence
Liu Y, Liang Y, Liu S, Rosenblum DS, Zheng Y (2016) Predicting urban water quality with ubiquitous data. arXiv preprint arXiv:1610.09462
Lokanathan S, Gunaratne RL (2015) Mobile network big data for development: demystifying the uses and challenges. Commun Strateg 97:75–94
Marker P, McNamara K, Wallace L (2002) The significance of information and communication technologies for reducing poverty. DFID, London
Matturdi B, Zhou X, Li S, Lin F (2014) Big Data security and privacy: a review. China Commun 11(14):135–145
Mayer-Schönberger V, Cukier K (2013) Big data: a revolution that will transform how we live, work, and think. Houghton Mifflin Harcourt
McAfee A, Brynjolfsson E, Davenport TH, Patil DJ, Barton D (2012) Big data. The management revolution. Harvard Bus Rev 90(10):61–67
Meade LM, Presley A (2002) R&D project selection using the analytic network process. IEEE Trans Eng Manag 49(1):59–66
Meade L, Sarkis J (1998) Strategic analysis of logistics and supply chain management systems using the analytical network process. Transport Res E-Log 34(3):201–215
Munir AB, Yasin M, Hajar S, Muhammad-Sukki F (2015) Big data: big challenges to privacy and data protection. Int Scholarly Sci Res Innov 9(1)
Nasser T, Tariq RS (2015) Big data challenges. J Comput Eng Inf Technol 4:3. https://doi.org/10.4172/2324 9307: 2
Nazir S, Anwar S, Khan SA, Shahzad S, Ali M, Amin R., … Cosmas J (2014) Software component selection based on quality criteria using the analytic network process. In: Abstract and Applied Analysis, vol 2014. Hindawi Publishing Corporation
Nie L, Zhang L, Yang Y, Wang M, Hong R, Chua TS (2015) Beyond doctors: future health prediction from multimedia and multimodal observations. In: Proceedings of the 23rd ACM international conference on Multimedia. ACM, pp 591–600
Normandeau K (2013) Beyond volume, variety and velocity is the issue of big data veracity. Inside Big Data
Preoţiuc-Pietro D, Liu Y, Hopkins D, Ungar L (2017) Beyond binary labels: political ideology prediction of twitter users in ACL
Proctor RA (1992) Selecting an appropriate strategy: a structured creative decision support method. Mark Intell Plan 10(11):21–24
Pulse, Global (2013) United Nations Global Pulse. 2014–08–15. http://www.un.org/millenniumgoals/pdf/GP%20Backgrounder-General2013_Sept2013.pdf
Saaty TL (1980) The analytic hierarchy process. McGraw-Hill, New York
Saaty TL (2005) Theory and applications of the analytic network process: decision making with benefits, opportunities, costs, and risks. RWS publications
Saaty TL (2008) Decision making with the analytic hierarchy process. Int J Serv Sci 1(1):83–98
Saaty TL, Vargas LG (2013) Decision making with the analytic network process: economic, political, social and technological applications with benefits, opportunities, costs and risks, vol 195. SpringerScience& Business Media
Sadeghi M (2012) Using analytic network process in a group decision-making for supplier selection. Informatica 23(4):621–643
Sagiroglu S, Sinanc D (2013) Big data: a review. In: Collaboration Technologies and Systems (CTS), 2013 International Conference on. IEEE, pp 42–47
Schlichter BR, Danylchenko L (2014) Measuring ICT usage quality for information society building. Gov Inf Q 31(1):170–184
Se-jin K et al (2013) A study on laws for the activation of IT convergence. KLRI
Siraj S, Mikhailov L, Keane JA (2015) PriEsT: an interactive decision support tool to estimate priorities from pairwise comparison judgments. Int Trans Oper Res 22(2):217–235
Song X, Nie L, Zhang L, Akbari M, Chua TS (2015) Multiple social network learning and its application in volunteerism tendency prediction. In: Proceedings of the 38th International ACM SIGIR Conference on Research and Development in Information Retrieval. ACM, pp 213–222
Taslicali AK, Ercan S (2006) The analytic hierarchy & the analytic network processes in multicriteria decision making: a comparative study. Doctoral dissertation, Old Dominion University
Techio LR, Misaghi M (2015) CSRA model–a cloud service risk assessment model
Teltscher S, Magpantay E, Gray V, Olaya D, Vallejo I (2010) Measuring the information society: the ICT development index. Telecommunication Development Bureau, International Telecommunications Union (ITU), Geneva
Tole AA (2013) Big data challenges. Database Syst J 4:31–40
Tran LT, Knight CG, O'neill RV, Smith ER (2004) Integrated environmental assessment of the mid-Atlantic region with analytical network process. Environ Monit Assess 94(1–3):263–277
Triantaphyllou E (2000) Multi-criteria decision making methods. In: Multi-criteria decision making methods: a comparative study. Springer, US, pp 5–21
Wallenius J, Dyer JS, Fishburn PC, Steuer RE, Zionts S, Deb K (2008) Multiple criteria decision making, multiattribute utility theory: recent accomplishments and what lies ahead. Manag Sci 54(7):1336–1349
Ward JS, Barker A (2013) Undefined by data: a survey of big data definitions. arXiv preprint arXiv:1309.5821
Weidner M, Dees J, Sanders P (2013) Fast OLAP query execution in main memory on large data in a cluster. In: Big Data, 2013 I.E. International Conference on. IEEE, pp 518–524
Zhou, X. (2012) Fuzzy analytical network process implementation with matlab. MATLAB–A fundamental tool for scientific computing and engineering applications, vol 3, pp 133–160
Acknowledgments
I would like to thanks, Professor Dr. Zeng Jianqiu and Shahid Latif for their intuitive discussions on Big Data and ANP at the “Triple Play Networking Lab” at School of Economics and Management Sciences, Beijing University of Posts and Telecommunications.
Author information
Authors and Affiliations
Contributions
Zahid Latif proposed and prepared the whole research while the other authors reviewed and gave suggestions to improve the article. All authors have read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflicts of Interest
The authors affirm no conflicts of interest.
Appendices
Appendix 1. Questionnaire Format
-
1.
Factors
Given in Table 3.
-
2.
Direction for questionnaire and example
-
2.1
Question format
-
2.1
The survey has a number of question sets. Each question asks to compare two factors at a time (pairwise comparison). All these factors are drawn from Table 3. The question format is given in Fig. 1.
-
2.2
What to fill?
Fill in empty boxes only and not to fill the 1 or 0.
-
2.3
How to fill?
For each question, we have a number scale from 1 to 9.
In order to make an ultimate decision, how much a selection factor is important in row’ as compared to another factor in column ‘n’.
1/9 means that, ‘m’ is extremely less important than ‘n’; and 9/1 or 9 indicates that, ‘m’ is extremely more important than ‘n’, while 1 means, ‘m’ and ‘n’ are equally important.

Appendix 2. Weighted super Matrix
Appendix 3. Un-weighted super Matrix
Appendix 4. Limit Matrix
Appendix 5
Rights and permissions
About this article
Cite this article
Latif, Z., Lei, W., Latif, S. et al. Big data challenges: Prioritizing by decision-making process using Analytic Network Process technique. Multimed Tools Appl 78, 27127–27153 (2019). https://doi.org/10.1007/s11042-017-5161-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5161-4