Abstract
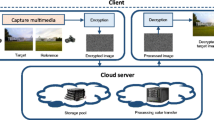
Cloud infrastructures are developed and maintained by third parties and users are always concerned about processing and storing their data over the cloud. Recent technologies such as high definition and 360-degree images/videos require efficient color processing, and current trend towards the cloud computing has initiated a necessity of performing color transfer remotely by untrusted third party servers. Nowadays, this field is emerging fast due to its inherent potential and research work in this direction is highly demanded. To address this necessity, we present a system that addresses the challenge of performing privacy preserving color transfer over third party servers. We use a one-dimensional chaotic logistic map coupled with ramp secret sharing scheme in a manner that secret images can be stored and processed for color transfer in the encrypted domain. Experimental results and security analysis demonstrate effectiveness of the approach against existing techniques of color transfer as well as image encryption.
















Similar content being viewed by others
References
I. Skiljan.irfanview http://www.irfanview.com. Accessed: 2017-04-26
Iitr-tennis court dataset https://sites.google.com/site/amiteshrajput/. Accessed: 2017-05-09
Inria person dataset http://pascal.inrialpes.fr/data/human/. Accessed: 2017-05-11
Al-Otaibi NA, Gutub AA (2014) 2-leyer security system for hiding sensitive text data on personal computers. Lect NoteS Inform Theory 2:151–157
Al-Otaibi NA, Gutub AA (2014) Flexible stego-system for hiding text in images of personal computers based on user security priority. In: International conference on advanced engineering technologies (AET-2014), pp 250–256
Alassaf N, Alkazemi B, Gutub A (2003) Applicable light-weight cryptography to secure medical data in iot systems. Arabia
Alotaibi N, Gutub A, Khan E (2015) Stego-system for hiding text in images of personal computers. In: The 12th learning and technology conference: Wearable tech/wearable learning
Amini A, Jamil N, Ahmad A, Z’aba M (2015) Threat modeling approaches for securing cloud computing. J Appl Sci 15(7):953
Finlayson GD, Mackiewicz M, Hurlbert A (2015) Color correction using root-polynomial regression. IEEE Trans Image Process 24(5):1460–1470
Fu C, Chen JJ, Zou H, Meng WH, Zhan YF, Yu YW (2012) A chaos-based digital image encryption scheme with an improved diffusion strategy. Optics Express 20(3):2363–2378
Gutub AAA et al (2010) Pixel indicator technique for rgb image steganography. Journal of Emerging Technologies in Web Intelligence 2(1):56–64
Gutub AAA, Khan FAA (2012) Hybrid crypto hardware utilizing symmetric-key and public-key cryptosystems. In: International conference on advanced computer science applications and technologies (ACSAT), pp 116–121. IEEE
Gutub A, Ankeer M, Abu-Ghalioun M, Shaheen A, Alvi A (2008) Pixel indicator high capacity technique for rgb image based steganography. In: International conference on advanced computer science applications and technologies (ACSAT)
Hsu CY, Lu CS, Pei SC (2012) Image feature extraction in encrypted domain with privacy-preserving sift. IEEE Trans Image Process 21(11):4593–4607
Khan F, Gutub AAA (2007) Message concealment techniques using image based steganography. IEEEGCC 2007
Lathey A, Atrey PK (2015) Image enhancement in encrypted domain over cloud. ACM Trans Multimed Comput Commun Appl (TOMM) 11(3):38
Lu H, Li Y, Serikawa S (2013) Underwater image enhancement using guided trigonometric bilateral filter and fast automatic color correction. In: 20Th IEEE international conference on image processing (ICIP), pp 3412–3416. IEEE
Ly DS, Beucher S, Bilodeau M (2014) Color correction through region matching leveraged by point correspondences. In: IEEE International conference on image processing (ICIP), pp 640–644 . IEEE
Martin D, Fowlkes C, Tal D, Malik J (2001) A database of human segmented natural images and its application to evaluating segmentation algorithms and measuring ecological statistics. In: 8th IEEE international conference on computer vision, 2001 (ICCV), vol 2, pp 416–423. IEEE
Mohanty M, Ooi WT, Atrey PK (2013) Scale me, crop me, knowme not: Supporting scaling and cropping in secret image sharing. In: IEEE international conference on multimedia and expo (ICME), pp 1–6. IEEE
Nanda H, Cutler R (2001) Practical calibrations for a real-time digital omnidirectional camera. CVPR Technical Sketch 20:1–4. IEEE
Pareek NK, Patidar V, Sud KK (2013) Diffusion–substitution based gray image encryption scheme. Digital signal processing 23(3):894–901
Pitié F, Kokaram AC, Dahyot R (2007) Automated colour grading using colour distribution transfer. Comput Vis Image Underst 107(1):123–137
Rahulamathavan Y, Phan RCW, Chambers JA, Parish DJ (2013) Facial expression recognition in the encrypted domain based on local fisher discriminant analysis. IEEE Trans Affect Comput 4(1):83– 92
Rajput AS, Raman B (2017) Color me, store me, know me not: Supporting image color transfer and storage in encrypted domain over cloud. In: IEEE International conference on multimedia & expo workshops (ICMEW), pp 291–296. IEEE
Reinhard E, Adhikhmin M, Gooch B, Shirley P (2001) Color transfer between images. IEEE Comput Graph Appl 21(5):34–41
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Soares LF, Fernandes DA, Freire MM, Inácio PR (2013) Secure user authentication in cloud computing management interfaces. In: 32nd IEEE international performance computing and communications conference (IPCCC), pp 1–2. IEEE
Tai YW, Jia J, Tang CK (2005) Local color transfer via probabilistic segmentation by expectation-maximization. In: IEEE computer society conference on computer vision and pattern recognition (CVPR), vol 1, pp 747–754. IEEE
Teng L, Wang X (2012) A bit-level image encryption algorithm based on spatiotemporal chaotic system and self-adaptive. Opt Commun 285(20):4048–4054
Thien CC, Lin JC (2002) Secret image sharing. Comput Graph 26(5):765–770
Uyttendaele M, Eden A, Skeliski R (2001) Eliminating ghosting and exposure artifacts in image mosaics. In: IEEE Computer society conference on computer vision and pattern recognition (CVPR), vol 2, pp II–II. IEEE
Wang X, Jin C (2012) Image encryption using game of life permutation and pwlcm chaotic system. Opt Commun 285(4):412–417
Wu Y, Yang G, Jin H, Noonan JP (2012) Image encryption using the two-dimensional logistic chaotic map. Journal of Electronic Imaging 21(1):013,014–1
Xiang Y, Zou B, Li H (2009) Selective color transfer with multi-source images. Pattern Recogn Lett 30(7):682–689
Xu W, Mulligan J (2010) Performance evaluation of color correction approaches for automatic multi-view image and video stitching. In: IEEE conference on computer vision and pattern recognition (CVPR), pp 263–270. IEEE
Yan WQ, Kankanhalli MS (2015) Face search in encrypted domain. In: Pacific-rim symposium on image and video technology, pp 775–790. Springer
Zafar F, Khan A, Malik SUR, Ahmed M, Anjum A, Khan MI, Javed N, Alam M, Jamil F (2017) A survey of cloud computing data integrity schemes: Design challenges, taxonomy and future trends. Computers & Security 65:29–49
Acknowledgements
This work was supported by Information Security Education and Awareness (ISEA) Project (phase II), Deity, Government of INDIA.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
All authors declare that they have no conflicts of interest regarding the publication of this manuscript.
Rights and permissions
About this article
Cite this article
Rajput, A.S., Raman, B. Cloud based image color transfer and storage in encrypted domain. Multimed Tools Appl 77, 21509–21537 (2018). https://doi.org/10.1007/s11042-017-5580-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5580-2