Abstract
It is well-known that blockcipher-based hash functions may be attacked when adopting blockciphers having related-key differential properties. However, all forms of related-key differentials are not always effective to attack them. In this paper we provide the general frameworks for collision and second-preimage attacks on hash functions by using related-key differential properties of instantiated blockciphers, and show their various applications. In the literature, there have been several provably secure blockcipher-based hash functions such as 12 PGV schemes, MDC-2, MJH, Abreast-DM, Tandem-DM, and HIROSE. However, their security cannot be guaranteed when they are instantiated with specific blockciphers. In this paper, we first observe related-key differential properties of some blockciphers such as Even-Mansour (EM), Single-key Even-Mansour (SEM), XPX with a fixed tweak (XPX1111), Chaskey cipher, and LOKI, which are suitable for IoT service platform security. We then present how these properties undermine the security of the aforementioned blockcipher-based hash functions. In our analysis, the collision and second-preimage attacks can be applied to several PGV schemes, MDC-2, MJH instantiated with SEM, XPX1111, Chaskey cipher, to PGV no.5, MJH, HIROSE, Abreast-DM, Tandem-DM instantiated with EM. Furthermore, LOKI-based MDC-2 is vulnerable to the collision attack. We also provide the necessary conditions for related-key differentials of blockciphers in order to attack each of the hash functions. To the best of our knowledge, this study is the first comprehensive analysis of hash functions based on blockciphers having related-key differential properties. Our cryptanalytic results support the well-known claim that blockcipher-based hash functions should avoid adopting blockciphers with related-key differential properties, such as the fixed point property in compression functions. We believe that this study provides a better understanding of the security of blockcipher-based hash functions.






Similar content being viewed by others
Notes
A permutation-based hash function construction has been also presented, in which a small set of permutations is used instead of a blockcipher in the hash functions.
Our cryptanalytic target hash functions can be applied for IoT service platform security, as their base blockciphers can be implemented with limited computing resources.
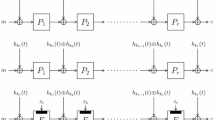
In [17], Kelsey and Schneier proposed a method for constructing (l, 2l + l − 1) expandable messages. In their method, \(|{M_{i}^{a}}|_{bl}\) and \(|{M_{i}^{b}}|_{bl}\) are used as 1 and 2i− 1 + 1, while we use 2 and 2i− 1 + 2 instead. We adopted such numbers (≥ 2) to use our rk-dp s for constructing expandable messages.
References
Andreeva E, Bogdanov A, Dodis Y, Mennink B, Steinberger JP (2013) On the indifferentiability of key-alternating ciphers. In: Advances in Cryptology - Proceedings of CRYPTO’13, LNCS 8042. Springer, pp 531–550
Andreeva E, Bouillaguet C, Dunkelman O, Fouque PA, Hoch J, Kelsey J, Shamir A, Zimmer S (2016) New second-preimage attacks on hash functions. J Cryptol 29(4):657–696
Andreeva E, Bouillaguet C, Dunkelman O, Kelsey J (2009) Herding, second preimage and trojan message attacks beyond merkle-damgård. In: International Workshop on Selected Areas in Cryptography, LNCS 5867. Springer, pp 393–414
Biham E, Shamir A (1991) Differential cryptanalysis of snefru, khafre, redoc-ii, LOKI and lucifer. In: Advances in Cryptology - Proceedings of CRYPTO ’91, LNCS 576. Springer, pp 156–171
Biryukov A, Khovratovich D, Nikolic I (2009) Distinguisher and related-key attack on the full AES-256. In: Advances in Cryptology - Proceedings of CRYPTO ’09, LNCS 5677. Springer, pp 231–249
Black J, Rogaway P, Shrimpton T (2002) Black-box analysis of the block-cipher-based hash-function constructions from pgv. In: Advances in Cryptology - Proceedings of CRYPTO ’02, LNCS 2442. Springer, pp 320–335
Black J, Cochran M, Shrimpton T (2005) On the impossibility of highly-efficient blockcipher-based hash functions. In: Advances in Cryptology - Proceedings of EUROCRYPT ’05, LNCS 3494. Springer, pp 526–541
Brachtl BO, Coppersmith D, Hyden MM, Matyas Jr SM, Meyer CH, Oseas J, Pilpel S, Schilling M (1990) Data authentication using modification detection codes based on a public one way encryption function. US Patent 4,908,861
Brown L, Pieprzyk J, Seberry J (1990) LOKI - A cryptographic primitive for authentication and secrecy applications. In: Proceedings of AUSCRYPT ’90, LNCS 453. Springer, pp 229–236
Dunkelman O, Keller N, Shamir A (2012) Minimalism in cryptography: The even-mansour scheme revisited. In: Advances in Cryptology - Proceedings of EUROCRYPT ’12, LNCS 7237. Springer, pp 336–354
Even S, Mansour Y (1991) A construction of a cipher from a single pseudorandom permutation. In: Proceedings of ASIACRYPT ’91, LNCS 739. Springer, pp 210–224
Hirose S (2006) Some plausible constructions of double-block-length hash functions. In: FSE’06, LNCS 4047. Springer, pp 210–225
Hong D, Koo B, Kim D (2012) Preimage and second-preimage attacks on PGV hashing modes of round-reduced aria, camellia, and serpent. IEICE Trans 95-A (1):372–380
Hong D, Kwon D (2012) Cryptanalysis of double-block-length hash mode MJH. IACR Cryptol ePrint Archive 2012:634. http://eprint.iacr.org/2012/634
Hong D, Kim D, Kwon D, Kim J (2016) Improved preimage attacks on hash modes of 8-round AES-256, vol 75, pp 14,525–14,539
Jiageng C, Hirose S, Kuwakado H, Miyaji A (2016) A collision attack on a double-block-length compression function instantiated with 8-/9-round aes-256. IEICE Trans Fundam Electron Communications and Computer Sciences 99(1):14–21
Kelsey J, Schneier B (2005) Second preimages on n-bit hash functions for much less than 2n work. In: Advances in Cryptology - Proceedings of EUROCRYPT ’05, LNCS 3494. Springer, pp 474–490
Knudsen LR, Mendel F, Rechberger C, Thomsen SS (2009) Cryptanalysis of MDC-2. In: Advances in Cryptology - Proceedings of EUROCRYPT ’09, LNCS 5479. Springer, pp 106–120
Knudsen LR, Rijmen V (2007) Known-key distinguishers for some block ciphers. In: Advances in Cryptology - Proceedings of ASIACRYPT ’07, LNCS 4833. Springer, pp 315–324
Lai X, Massey JL (1992) Hash function based on block ciphers. In: Advances in Cryptology - Proceedings of EUROCRYPT ’92, LNCS 658. Springer, pp 55–70
Lee J, Kwon D (2011) The security of abreast-dm in the ideal cipher model. IEICE Trans 94-A(1):104–109
Lee J, Stam M (2011) MJH: A faster alternative to MDC-2. In: Proceedings of CT-RSA ’11, LNCS 6558. Springer, pp 213–236
Lee J, Stam M, Steinberger JP (2011) The collision security of tandem-dm in the ideal cipher model. In: Advances in Cryptology - Proceedings of CRYPTO ’11, LNCS 6841. Springer, pp 561–577
Mennink B (2016) XPX: generalized tweakable even-mansour with improved security guarantees. In: Advances in Cryptology - Proceedings of CRYPTO ’16, LNCS 9814. Springer, pp 64–94
Mouha N, Mennink B, Herrewege AV, Watanabe D, Preneel B, Verbauwhede I (2014) Chaskey: An efficient MAC algorithm for 32-bit microcontrollers. In: Selected Areas in Cryptography - SAC ’14, LNCS 8781. Springer, pp 306–323
Preneel B, Govaerts R, Vandewalle J (1993) Hash functions based on block ciphers: A synthetic approach. In: Advances in Cryptology - Proceedings of CRYPTO ’93, LNCS 773. Springer, pp 368–378
Rivest R (1992) The md5 message-digest algorithm
Rogaway P, Steinberger JP (2008) Security/efficiency tradeoffs for permutation-based hashing. In: Advances in Cryptology - Proceedings of EUROCRYPT ’08, LNCS 4965. Springer, pp 220–236
Sasaki Y (2011) Meet-in-the-middle preimage attacks on AES hashing modes and an application to whirlpool. In: FSE ’11, LNCS 6733. Springer, pp 378–396
Secure hash standard (shs) (2012) FIPS PUB 180-4
Stam M (2008) Beyond uniformity: Better security/efficiency tradeoffs for compression functions. In: Advances in Cryptology - Proceedings of CRYPTO ’08, LNCS 5157. Springer, pp 397–412
Steil M (2005) 17 mistakes microsoft made in the xbox security system. In: 22nd Chaos Communication Congr
Steinberger JP (2007) The collision intractability of MDC-2 in the ideal-cipher model. In: Advances in Cryptology - Proceedings of EUROCRYPT ’07, LNCS 4515. Springer, pp 34–51
Steinberger JP (2010) Stam’s collision resistance conjecture. In: Advances in Cryptology - Proceedings of EUROCRYPT ’10, LNCS 6110. Springer, pp 597–615
Steinberger JP, Sun X, Yang Z (2012) Stam’s conjecture and threshold phenomena in collision resistance. In: Advances in Cryptology - Proceedings of CRYPTO ’12, LNCS 7417. Springer, pp 384–405
Wei L, Peyrin T, Sokolowski P, Ling S, Pieprzyk J, Wang H (2012) On the (in)security of IDEA in various hashing modes. In: FSE ’12, LNCS 7549. Springer, pp 163–179
Winternitz RS (1984) A secure one-way hash function built from DES. In: Proceedings of the 1984 IEEE Symposium on Security and Privacy. IEEE Computer Society, pp 88–90
Acknowledgments
This work was supported by Institute for Information & communications Technology Promotion(IITP) grant funded by the Korea government(MSIT) (No.2017-0-00520, Development of SCR-Friendly Symmetric Key Cryptosystem and Its Application Modes).
Author information
Authors and Affiliations
Corresponding author
Appendix: Experimental Results: Colliding Message Pairs
Appendix: Experimental Results: Colliding Message Pairs
We implemented our collision attacks on SEM, Chaskey cipher, or XPX1111-based PGV no.1. In our implementations, the f functions in SEM and XPX1111 are set to AES-128 with the key 0x000000000x000000000x000000000x00000000. Moreover, IV is fixed as 0x012345670x89abcdef0xfedcba980x76543210. Table 8 shows examples of our simulations. Given that the attack complexity is negligible, these colliding message pairs are found immediately.
Rights and permissions
About this article
Cite this article
Kim, H., Kim, Dw., Yi, O. et al. Cryptanalysis of hash functions based on blockciphers suitable for IoT service platform security. Multimed Tools Appl 78, 3107–3130 (2019). https://doi.org/10.1007/s11042-018-5630-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5630-4