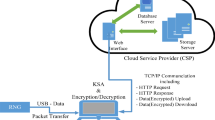
Abstract
In the past few years, various lightweight cryptographic algorithms have been proposed to balance the trade-offs between the requirements of resource constrained IoT devices and the need to securely transmit and protect data. However, it is critical to analyze and evaluate these algorithms to examine their capabilities. This paper provides a thorough investigation of the randomness of ciphertext obtained from Simeck, Kasumi, DES and AES. The design of our randomness analysis is based on five metrics implemented following the guidance of the NIST statistical test suite for cryptographic applications. This analysis also provides performance and power consumption evaluations for the selected cryptographic algorithms using different platforms and measures. Results from the evaluation reveal that lightweight algorithms have competitive randomness levels, lower processing time and lower power consumption when compared to conventional algorithms.
















Similar content being viewed by others
References
197 NF (2009) Advanced Encryption Standard. processing Standards Publication
Abd-Elmonim WG, Ghali NI, Hassanien AE (2011) Abraham A Known-plaintext attack of DES-16 using Particle Swarm Optimization. In: Third World Congress on Nature and Biologically Inspired Computing, pp 12–16. https://doi.org/10.1109/NaBIC.2011.6089410
Adams C, Tavares S (1990) The use of bent sequences to achieve higher-order strict avalanche criterion in S-box design. Queen's University, Ontario
Akgün F, Buluş E (2016) Comparison of encryption algorithms strength used in 3G mobile communication. Trakya University J Eng Sci 17(1):1–11
Aljawarneh S, Yassein MB, Talafha Wa A (2017) A resource-efficient encryption algorithm for multimedia big data. Multimedia Tools and Applications 76(21):22703–22724. https://doi.org/10.1007/s11042-016-4333-y
Amic S, Soyjaudah KMS, Mohabeer H, Ramsawock G (2016) Cryptanalysis of DES-16 using Binary Firefly Algorithm. In: IEEE International Conference on Emerging Technologies and Innovative Business Practices for the Transformation of Societies (EmergiTech), 2016. pp 94–99.https://doi.org/10.1109/EmergiTech.2016.7737318
Amin R, Kumar N, Biswas GP, Iqbal R, Chang V (2018) A light weight authentication protocol for IoT-enabled devices in distributed cloud computing environment. Futur Gener Comput Syst 78(3):1005–1019. https://doi.org/10.1016/j.future.2016.12.028
Antonio T, Angelo L, Francesco B (2014) Information security and threats in mobile appliances. Recent Patents on Computer Science 7(1):3–11. https://doi.org/10.2174/2213275907666140610200010
Bahrami S, Naderi M (2013) Encryption of multimedia content in partial encryption scheme of DCT transform coefficients using a lightweight stream algorithm. Optik - International Journal for Light and Electron Optics 124(18):3693–3700. https://doi.org/10.1016/j.ijleo.2012.11.028
Barahtian O, Cuciuc M, Petcana L, Leordeanu C, Cristea V (2015) Evaluation of Lightweight Block Ciphers for Embedded Systems. In: Bica I, Naccache D, Simion E (eds) Innovative Security Solutions for Information Technology and Communications: 8th International Conference, SECITC 2015, Bucharest, Romania, June 11–12, 2015. Revised Selected Papers. Springer International Publishing, Cham, pp 49–58. https://doi.org/10.1007/978-3-319-27179-8_4
Beaulieu R, Shors D, Smith J, Treatman-Clark S, Weeks B, Wingers L (2015) The SIMON and SPECK lightweight block ciphers. Paper presented at the 52nd Annual Design Automation Conference, San Francisco
Benrhouma O, Hermassi H, Belghith S (2015) Security analysis and improvement of a partial encryption scheme. Multimedia Tools and Applications 74(11):3617–3634. https://doi.org/10.1007/s11042-013-1790-4
Biham E, Biryukov A (1997) An improvement of Davies’ attack on DES. J Cryptology 10(3):195–205. https://doi.org/10.1007/s001459900027
Biham E, Shamir A (1991) Differential cryptanalysis of DES-like cryptosystems. In: Menezes AJ, Vanstone SA (eds) Advances in cryptology-CRYPT0’ 90. Springer, Berlin, pp 2–21. https://doi.org/10.1007/3-540-38424-3_1
Biham E, Shamir A (1991) Differential cryptanalysis of DES-like cryptosystems. J Cryptology 4(1):3–72. https://doi.org/10.1007/BF00630563
Biham E, Biryukov A, Shamir A (2005) Cryptanalysis of skipjack reduced to 31 rounds using impossible differentials. J Cryptology 18(4):291–311. https://doi.org/10.1007/3-540-48910-X_2
Biham E, Dunkelman O, Keller N (2008) A unified approach to related-key attacks. In: International Workshop on Fast Software Encryption, Springer, pp 73–96. https://doi.org/10.1007/978-3-540-71039-4_5
Chen L, Thombre S, Järvinen K, Lohan ES, Alén-Savikko A, Leppäkoski H, Bhuiyan MZH, Bu-Pasha S, Ferrara GN, Honkala S, Lindqvist J, Ruotsalainen L, Korpisaari P, Kuusniemi H (2017) Robustness, security and privacy in location-based Services for Future IoT: a survey. IEEE Access 5:8956–8977. https://doi.org/10.1109/ACCESS.2017.2695525
Chew L, Chew N, Norshahil I, Shah M, Azura N, Abdullah N, Hidayah N, Zawawi A, Rani HA, Zakaria AA (2015) Randomness analysis on Speck family of lightweight block cipher. International Journal of Cryptology Research 5(1):44–60
Daemen J, Rijmen V (1999) AES proposal: Rijndael
Dhall S, Pal SK, Sharma K (2014) New lightweight conditional encryption schemes for multimedia. In: Pant M, Deep K, Nagar A, Bansal JC (eds) Proceedings of the third international conference on soft computing for problem solving, vol 1. Springer India, New Delhi, pp 365–377. https://doi.org/10.1007/978-81-322-1771-8_32
Diffie W, Hellman ME (1977) Special feature exhaustive cryptanalysis of the NBS data encryption standard. Computer 10(6):74–84. https://doi.org/10.1109/C-M.1977.217750
Dinarvand N, Barati H (2017) An efficient and secure RFID authentication protocol using elliptic curve cryptography. Wirel Netw. https://doi.org/10.1007/s11276-017-1565-3
Duta C, Mocanu B-C, Vladescu F-A, Gheorghe L (2014) Randomness evaluation framework of cryptographic algorithms. International Journal on Cryptography and Information Security 4(1):31–49
Dworkin MJ, Barker EB, Nechvatal JR et al (2001) Advanced Encryption Standard (AES). Federal Inf. Process. Stds. (NIST FIPS). https://doi.org/10.6028/NIST.FIPS.197
El Hennawy HMS, Omar AEA, Kholaif SMA (2015) LEA: link encryption algorithm proposed stream cipher algorithm. Ain Shams Engineering Journal 6(1):57–65. https://doi.org/10.1016/j.asej.2014.08.001
Farahani B, Firouzi F, Chang V, Badaroglu M, Constant N, Mankodiya K (2018) Towards fog-driven IoT eHealth: promises and challenges of IoT in medicine and healthcare. Futur Gener Comput Syst 78(2):659–676. https://doi.org/10.1016/j.future.2017.04.036
de Fuentes JM, González-Manzano L, Serna-Olvera J, Veseli F (2017) Assessment of attribute-based credentials for privacy-preserving road traffic services in smart cities. Pers Ubiquit Comput 21(5):869–891. https://doi.org/10.1007/s00779-017-1057-6
Goubin L, Patarin J (1999) DES and differential power analysis the “duplication” method. In: Koç ÇK, Paar C (eds) Cryptographic hardware and embedded systems: first international workshop, CHES’99 Worcester, MA, USA, august 12–13, 1999 springer. Heidelberg, Berlin, pp 158–172. https://doi.org/10.1007/3-540-48059-5_15
Gupta R, Rao UP (2017) A hybrid location privacy solution for mobile LBS. Mob Inf Syst 2017:11. https://doi.org/10.1155/2017/2189646
Gupta R, Rao UP (2017) An exploration to location based service and its privacy preserving techniques: a survey. Wirel Pers Commun 96(2):1973–2007. https://doi.org/10.1007/s11277-017-4284-2
Hossain M, Hasan R, Skjellum A (2017) Securing the internet of things: a meta-study of challenges, approaches, and open problems. In: IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), pp 220–225. https://doi.org/10.1109/ICDCSW.2017.78
Hossain MS, Xu C, Li Y, Pathan ASK, Bilbao J, Zeng W, Saddik AE (2017) Impact of next-generation mobile technologies on IoT-cloud convergence. IEEE Commun Mag 55(1):18–19. https://doi.org/10.1109/MCOM.2017.7823332
Hossain M, Islam SMR, Ali F, Kwak K-S, Hasan R An internet of things-based health prescription assistant and its security system design. Futur Gener Comput Syst. https://doi.org/10.1016/j.future.2017.11.020
Information Resources Management Association (2016) Big data: concepts, methodologies, tools, and applications. IGI Global. https://doi.org/10.4018/978-1-4666-9840-6
Institute ETS (1999) Specification of the 3GPP confidentiality and integrity algorithms; Document 2: Kasumi specification, version 1.0
Institute ETS (1999) ETSI SAGE 3GPP Standard Algorithms Task Force, Security Algorithms Group of Experts (SAGE) Report on the Evaluation of 3GPP Standard Confidentiality and Integrity Algorithms
Institute ETS (2007) Universal Mobile Telecommunications System (UMTS); Specification of the 3GPP confidentiality and integrity algorithms; Document 2: Kasumi specification, 3GPP TS 35.202 version 7.0.0 Release 7
Jenson S (2017) The future IoT: building better Legos. Computer 50(2):68–71. https://doi.org/10.1109/MC.2017.48
Jesse N (2016) Internet of things and big data – the disruption of the value chain and the rise of new software ecosystems. IFAC-PapersOnLine 49(29):275–282. https://doi.org/10.1016/j.ifacol.2016.11.079
Jindal P, Singh B (2017) Optimization of the security-performance tradeoff in RC4 encryption algorithm. Wirel Pers Commun 92(3):1221–1250. https://doi.org/10.1007/s11277-016-3603-3
Kaminsky A, Kurdziel M, Radziszowski S (2010) An overview of cryptanalysis research for the advanced encryption standard. In: Milcom 2010 Military Communications Conference, pp 1310–1316. https://doi.org/10.1109/MILCOM.2010.5680130
Katagi M, Moriai S (2008) Lightweight cryptography for the internet of things. Sony Corporation. Tokyo, Japan, Tech. Rep., 2011. [Online]. Available: http://www.iab.org/wp-content/IABuploads/2011/03/Kaftan.pdf
Kaur G, Saini KS (2017) Securing network communication between motes using hierarchical group key management scheme using threshold cryptography in smart home using internet of things. In: Vishwakarma HR, Akashe S (eds) Computing and network sustainability: proceedings of IRSCNS 2016. Springer, Singapore, pp 201–212. https://doi.org/10.1007/978-981-10-3935-5_21
Kazmi S, Ikram N (2013) Chaos based key expansion function for block ciphers. Multimedia Tools and Applications 66(2):267–281. https://doi.org/10.1007/s11042-011-0767-4
Khan Z, Pervez Z, Abbasi AG (2017) Towards a secure service provisioning framework in a smart city environment. Futur Gener Comput Syst 77(Supplement C):112–135. https://doi.org/10.1016/j.future.2017.06.031
Khovratovich D, Nikolic I (2010) Rotational Cryptanalysis of ARX. In: FSE, Springer, pp 333–346
Kim K (1991) Construction of DES-like S-boxes Based on Boolean Functions Satisfying the SAC. In: Advances in Cryptology—ASIACRYPT'91, Springer, pp 59–72
Kim K, Park S, Lee S (1993) Reconstruction of s2 DES S- boxes and their Immunity to Differential Cryptanalysis. In: Proceedings of the 1993 Korea-Japan Workshop on Information Security and Cryptography, Seoul, Korea, pp 24–26
Kinga Marton AS, Ignat I (2010) Randomness in digital cryptography: a survey. Rom J Inf Sci Technol 13(3):219–240
Knudsen LR (1994) Truncated and higher order differentials. In: International Workshop on Fast Software Encryption, Springer, pp 196–211
Kumar N, Sharma S (2017) Survey analysis on the usage and impact of Whatsapp messenger. Global Journal of Enterprise Information System 8(3):52–57. https://doi.org/10.18311/gjeis/2016/15741
Kumar S, Paar C, Pelzl J, Pfeiffer G, Rupp A, Schimmler M (2006) How to Break DES for Euro 8,980. In: 2nd Workshop on Special-purpose Hardware for Attacking Cryptographic Systems—SHARCS, pp 3–4
Kumar SP, Samson VRR, Sai UB, Rao PLSDM, Eswar KK (2017) Smart health monitoring system of patient through IoT. In: International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), pp 551–556. https://doi.org/10.1109/I-SMAC.2017.8058240
Lawrence E. Bassham I, Rukhin AL, Soto J, Nechvatal JR, Smid ME, Barker EB, Leigh SD, Levenson M, Vangel M, Banks DL, Heckert NA, Dray JF, Vo S (2010) SP 800–22 Rev. 1a. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications. National Institute of Standards & Technology
Lee RB, Shi Z, Yang X (2001) Cryptography efficient permutation instructions for fast software. IEEE Micro 21(6):56–69. https://doi.org/10.1109/40.977759
Li C-T, Lee C-C, Weng C-Y, Wu T-Y, Chen C-M (2017) Cryptanalysis of “an efficient searchable encryption against keyword guessing attacks for shareable electronic medical Records in Cloud-Based System”. In: Kim K, Joukov N (eds) Information science and applications 2017: ICISA 2017. Springer, Singapore, pp 282–289. https://doi.org/10.1007/978-981-10-4154-9_33
Liao D, Sun G, Li H, Yu H, Chang V (2017) The framework and algorithm for preserving user trajectory while using location-based services in IoT-cloud systems. Clust Comput 20(3):2283–2297. https://doi.org/10.1007/s10586-017-0986-1
Liu Y, Tian S, Hu W, Xing C (2012) Design and statistical analysis of a new chaotic block cipher for wireless sensor networks. Commun Nonlinear Sci Numer Simul 17(8):3267–3278
Liu Y, Nie L, Han L, Zhang L, Rosenblum DS (2015) Action2Activity: recognizing complex activities from sensor data. Paper presented at the 24th International Conference on Artificial Intelligence, Buenos Aires, Argentina
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: sensor-based activity recognition. Neurocomputing 181(Supplement C):108–115. https://doi.org/10.1016/j.neucom.2015.08.096
Liu L, Cheng L, Liu Y, Jia Y, Rosenblum DS (2016) Recognizing complex activities by a probabilistic interval-based model. Paper presented at the Thirtieth AAAI Conference on Artificial Intelligence, Phoenix, Arizona
Lot NH, Abdullah NAN, Rani HA (2011) Statistical analysis on KATAN Block Cipher. In: 2011 International Conference on Research and Innovation in Information Systems, 2011. pp 1–6. https://doi.org/10.1109/ICRIIS.2011.6125698
Lu Y, Wei Y, Liu L, Zhong J, Sun L, Liu Y (2017) Towards unsupervised physical activity recognition using smartphone accelerometers. Multimedia Tools and Applications 76(8):10701–10719. https://doi.org/10.1007/s11042-015-3188-y
Matsui M (1994) Linear cryptanalysis method for DES cipher. Paper presented at the workshop on the theory and application of cryptographic techniques on advances in cryptology. Lofthus, Norway
Matsui M (1997) New block encryption algorithm MISTY. In: Biham E (ed) Fast software encryption: 4th international workshop, FSE’97 Haifa, Israel, January 20–22 1997. Springer, Berlin, pp 54–68. https://doi.org/10.1007/BFb0052334
McKay KA, Bassham L, Turan MS, Mouha N (2017) Report on Lightweight Cryptography. National Institute of Standards and Technology
Meng S-H, Huang A-C, Lee C-J, Huang T-J, Dal J-N (2018) Design for Intelligent Control System of Curtain Based on Arduino. In: Pan J-S, Wu T-Y, Zhao Y, Jain LC (eds) Advances in Smart Vehicular Technology, Transportation, Communication and Applications: Proceedings of the First International Conference on Smart Vehicular Technology, Transportation, Communication and Applications, November 6–8, 2017, Kaohsiung, Taiwan. Springer International Publishing, Cham, pp 178–184. https://doi.org/10.1007/978-3-319-70730-3_22
Montag C, Błaszkiewicz K, Sariyska R, Lachmann B, Andone I, Trendafilov B, Eibes M, Markowetz A (2015) Smartphone usage in the 21st century: who is active on WhatsApp? BMC Research Notes 8(1):331. https://doi.org/10.1186/s13104-015-1280-z
Nadeem A, Javed MY (2005) A performance comparison of data encryption algorithms. International Conference on Information and Communication Technologies 27-28:84–89. https://doi.org/10.1109/ICICT.2005.1598556
Perera C, Liu CH, Jayawardena S, Chen M (2014) A survey on internet of things from industrial market perspective. IEEE Access 2:1660–1679. https://doi.org/10.1109/ACCESS.2015.2389854
Rani DJ, Roslin SE (2016) Light weight cryptographic algorithms for medical internet of things (IoT) - a review. In: 2016 Online International Conference on Green Engineering and Technologies (IC-GET), pp 1–6. https://doi.org/10.1109/GET.2016.7916703
Riahi Sfar A, Natalizio E, Challal Y, Chtourou Z (2017) A roadmap for security challenges in the internet of things. Digital Communications and Networks. https://doi.org/10.1016/j.dcan.2017.04.003
Roback; JRNEBBLEBWEBMJDJFE (2001) Report on the Development of the Advanced Encryption Standard (AES). Journal of Research (NIST JRES) 106 No. 3
Rukhin A, Soto J, Nechvatal J, Barker E, Leigh S, Levenson M, Banks D, Heckert A, Dray J, Vo S (2010) Statistical test suite for random and pseudorandom number generators for cryptographic applications. special publication 800-22. National Institute of Standards and Technology (NIST), Gaithersburg
Sadeghi AR, Wachsmann C (2015) Waidner M Security and privacy challenges in industrial Internet of Things. In: 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), 8–12 June. pp 1–6. https://doi.org/10.1145/2744769.2747942
Schneier B, Schneier B (2015) Data Encryption Standard (DES). In: Applied Cryptography, Second Edition. John Wiley & Sons, Inc., pp 265–301. https://doi.org/10.1002/9781119183471.ch12
Sehgal VK, Mehrotra S, Marwah H (2016) Car security using Internet of Things. In: 2016 I.E. 1st International Conference on Power Electronics, Intelligent Control and Energy Systems (ICPEICES), pp 1–5. https://doi.org/10.1109/ICPEICES.2016.7853207
Singh S, Sharma PK, Moon SY, Park JH (2017) Advanced lightweight encryption algorithms for IoT devices: survey, challenges and solutions. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-017-0494-4
Sulistyo B, Rahardjo B, Mahayana D (2009) On applicability of chaos game method for block cipher randomness analysis. In: International Conference on Electrical Engineering and Informatics, pp 258–262. https://doi.org/10.1109/ICEEI.2009.5254777
Sun G, Chang V, Ramachandran M, Sun Z, Li G, Yu H, Liao D (2017) Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J Netw Comput Appl 89(Supplement C):3–13. https://doi.org/10.1016/j.jnca.2016.10.011
Tilborg HCA, Jajodia S (2011) Encyclopedia of cryptography and security. Springer Publishing Company, Incorporated
Tweneboah-Koduah S, Skouby KE, Tadayoni R (2017) Cyber security threats to IoT applications and service domains. Wirel Pers Commun 95(1):169–185. https://doi.org/10.1007/s11277-017-4434-6
Verma OP, Agarwal R, Dafouti D, Tyagi S (2011) Notice of Violation of IEEE Publication Principles Peformance analysis of data encryption algorithms. In: 3rd International Conference on Electronics Computer Technology, 2011. pp 399–403. https://doi.org/10.1109/ICECTECH.2011.5942029
Webster AF, Tavares S (1986) On the design of S-boxes. In: Advances in cryptology, Springer Berlin Heidelberg, pp 523–534
Xu L, Jiang C, Wang J, Yuan J, Ren Y (2014) Information security in big data: privacy and data mining. IEEE Access 2:1149–1176. https://doi.org/10.1109/ACCESS.2014.2362522
Yang G, Zhu B, Suder V, Aagaard MD, Gong G (2015) The Simeck family of lightweight block ciphers. In: Güneysu T, Handschuh H (eds) Cryptographic hardware and embedded systems -- CHES 2015: 17th international workshop, Saint-Malo, France, September 13–16, 2015. Springer, Berlin, pp 307–329. https://doi.org/10.1007/978-3-662-48324-4_16
Yang Y, Liu X, Deng RH, Li Y (2017) Lightweight sharable and traceable secure mobile health system. IEEE Transactions on Dependable and Secure Computing PP 99:1–14. https://doi.org/10.1109/TDSC.2017.2729556
Yang Y, Zheng X, Chang V, Ye S, Tang C (2017) Lattice assumption based fuzzy information retrieval scheme support multi-user for secure multimedia cloud. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-4560-x
Yang Y, Zheng X, Liu X, Zhong S, Chang V (2017) Cross-domain dynamic anonymous authenticated group key management with symptom-matching for e-health social system. Futur Gener Comput Syst. https://doi.org/10.1016/j.future.2017.06.025
Yao X, Chen Z, Tian Y (2015) A lightweight attribute-based encryption scheme for the internet of things. Futur Gener Comput Syst 49(Supplement C):104–112. https://doi.org/10.1016/j.future.2014.10.010
Zhu L, Zhang Z, Xu C (2017) Privacy-preserving meter reading transmission in smart grid. In: Secure and privacy-preserving data communication in internet of things. Springer, Singapore, pp 33–52. https://doi.org/10.1007/978-981-10-3235-6_3
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Qasaimeh, M., Al-Qassas, R.S. & Tedmori, S. Software randomness analysis and evaluation of lightweight ciphers: the prospective for IoT security. Multimed Tools Appl 77, 18415–18449 (2018). https://doi.org/10.1007/s11042-018-5663-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5663-8