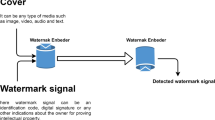
Abstract
Digital image watermarking has become more popular due to its applications in copyright protection and secret communication. Most of the image watermarking algorithms reported till date involve modification of the host contents for embedding a secret data, leading to a reduced robustness and a limited embedding capacity. In the present work, a novel spatial domain watermarking scheme called Pixel Value Search Algorithm (PVSA) is proposed using a linear search operation to achieve high robustness and a theoretically unlimited embedding capacity. In the proposed scheme, secret data are embedded into a host image by mapping their intensity values into row and column locations. Due to this linear mapping of secret data, the host structural content is not altered. In addition, multiple watermarks can be mapped into a single host image using the PVSA technique. The proposed algorithm is verified using MATLAB® simulations and its performance characteristics are assessed using a standard benchmark tool called strimark. Experimental results illustrate the robustness of the PVSA technique against the attacks of Gaussian blurring, Gaussian noise, salt and pepper noise, Poisson noise, speckle noise, mean and median filtering, histogram equalization, image sharpening, intensity transformation, unsharp filtering, JPEG attack, etc. Subsequently an ASIC implementation of the PVSA algorithm is carried out using Verilog HDL and various modules of the Cadence® EDA tool so as to integrate the chip as a watermark co-processor. The ASIC implementation using a 0.18 μm technology at an operating frequency of 100 MHz consumes a power of 326.34 μW for the complete hardware architecture.














Similar content being viewed by others
References
Anderson RJ, Petitcolas FAP (1998) On the limits of steganography. IEEE Sel Areas Commun 16(4):474–481
Celik MU, Sharma G, Tekalp AM, Saber E (2005) Lossless generalized -LSB data embedding. IEEE Trans Image Process 14(2):253–266
Chu WC (2003) DCT Based Image watermarking using subsampling. IEEE Trans Multimed 5(1):34–38
Cox IJ, Killian J, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Craver S, Memon N, Yeo BL, Yeung MM (1998) Resolving rightful ownerships with invisible watermarking techniques: limitations, attacks and implications. IEEE Sel Areas Commun 16(4):573–586
Das S, Maity R, Maity NP (2017) VLSI based pipeline architecture for reversible Image watermarking by difference expansion with high-level synthesis approach. Circuits Syst Signal Process. https://doi.org/10.1007/s0034-017-0609-3
Eskicioglu AM, Delp EJ (2001) An overview of multimedia content protection in consumer electronic devices. Elsevier Signal Process 16(7):681–699
Fates N, Petitcolas FAP (2000) Watermarking scheme evaluation tool. Proc IEEE international symposium on multimedia software engineering. Taipei, Taiwan, 13-Dec. https://doi.org/10.1109/MMSE.2000.897231
Garimella A, Sataynarayanan MVV, Murugesh PS, Niranjan UC (2003) VLSI implementation of online digital watermarking techniques with difference encoding for the 8 bit grayscale images. Proceedings of the International conference on VLSI Design 792–796. https://doi.org/10.1109/ICVD.2003.1183151
Garimella A, Sataynarayanan MVV, Murugesh PS, Niranjan UC (2004) Asic for digital colour image watermarking. Proceedings of 11th IEEE Digital signal processing workshop. 292–295. https://doi.org/10.1109/DSPWS.2004.1437961
Hazra S, Ghosh S, Sayandip D, Rahaman H (2017) FPGA implementation of semifragile reversible watermarking by histogram bin shifting in real time. J Real-Time Image Proc. https://doi.org/10.1007/s1154-017-0672-9
Jayanthi VE (2011) High performance VLSI architecture for block based visible image watermarking. Int J Electron 99(9):1191–1206
Joshi AM, Mishra V, Patrikar RM (2016) FPGA prototyping of video watermarking for ownership verification based on H.264/AVC. Multimed Tools Appl 75(6):3121–3144
Karthigaikumar P, Baskaran K (2011) FPGA and ASIC implementation of robust invisible binary image watermarking algorithm using connectivity preserving criteria. Microelectron J 42(1):82–88
Khodaei M, Faez K (2012) New adaptive stenographic method using least significant bit substitution and pixel-value differencing. IET Image Process 6(6):677–686
Kougianos E, Mohanty SP, Mahapatra RN (2009) Hardware assisted watermarking for multimedia. Int J Comput Electr Eng 35(2):339–358
Kumar C, Singh AK, Kumar P (2017) A recent survey on image watermarking techniques and its application in e-governance. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5222-8
Langelar GC, Setyawan I, Lagendik RL (2000) Watermarking digital image and video data. A state - of - the- art overview. IEEE Signal Process Mag 17(5):20–46
Larijani H, Rad GR (2008) A new spatial domain algorithm for gray scale images watermarking. Proceedings of the International Conference on Computer and Communication Engineering May 13–15, Kuala Lumpur, Malaysia. https://doi.org/10.1109/ICCCE.2008.4580587
Lu W, Sun W, Lu H (2012) Novel robust image watermarking based on subsampling and DWT. Multimed Tools Appl 60(1):31–46
Maity HK, Maity SP (2014) FPGA implementation of reversible watermarking in digital images using reversible contrast mapping. Int J Syst Softw 96(1):93–104
Maity SP, Kundu M, Maity S (2009) Dual purpose FWT domain spread spectrum image watermarking in real time. Int J Comput Electr Eng 35(2):415–433
Marvel LM, Boncelet CG, Retter CT (1999) Spread spectrum image steganography. IEEE Trans Image Process 8(8):1075–1083
Mathai NJ, Kundur D, Sheikholeslami A (2003) Hardware implementation perspectives of digital video watermarking algorithms. IEEE Trans Signal Process 51(4):925–938
Minh T, Tanaka K (2015) Comparison of watermarking schemes using linear and nonlinear feature matching. Proceedings of the Int. Conf. on knowledge and Systems Engineering Ho Chi Minh City Vietnam Oct 8–10. https://doi.org/10.1109/KSE.2015.67
Miyazaki A, Sangyo K (2005) An improved correlation based watermarking method for images using a nonlinear programming algorithm. Proceedings of international conference on Non Linear Signal and Image Processing NSIP Abstracts IEEE Eurasip, Sapporo. https://doi.org/10.1109/NSIP.2005.15002212
Mohanty SP (2009) A secure digital camera architecture for integrated real time digital rights management. J Syst Archit 55(10–12):468–480
Mohanty SP, Ranganathan N, Namballa RK (2003) VLSI implementation of digital watermarking algorithms toward the development of a secure JPEG encoder. Proceedings of IEEE Workshop Signal Processing Systems 183–188. https://doi.org/10.1109/SIPS.2003.1235666
Mohanty SP, Ranganathan N, Namballa RK (2005) A VLSI architecture for visible watermarking in a secure still digital camera (S2DC) design. IEEE Trans Very Large Scale Integr (TVLSI) Syst 13(8):1002–1012
Mohanty SP, Ranganathan N, Balakrishnan K (2006) A dual voltage-frequency VLSI chip for image watermarking in DCT domain. IEEE Trans Circuits Syst II, Express Briefs 53(5):394–398
Mohanty SP, Kougnios E, Ranganathan N (2007) VLSI architecture and chip for combined invisible robust and fragile watermarking. IET Comput Digit Tech 1(5):600–611
Nayak MR, Joyashree B, Sarkar S, Sarkar SK (2017) Hardware implementation of a novel watermarking algorithm based on phase congruency and singular value decomposition technique. Int J Electron Commun (AEU) 71:1–8
Petitcolas FAP (2000) Watermarking schemes evaluation. IEEE Signal Process Mag 17(5):58–64
Petticolas FAP, Anderson RJ, Kuhn MG (1999) Information hiding – a survey. Proc IEEE Spec Issue Prot Multimed Content 87(7):1062–1078
Roy SD, Lin X, Shoshan Y, Fish A (2013) Hardware implementation of a digital watermarking system for video authentication. IEEE Trans Circuits Syst Video Technol 23(2):289–300
Sakthivel SM, Ravi Sankar A (2015) A real time watermarking of grayscale images without altering its content. Proceedings of the Int. Conf. on VLSI Systems, Architecture, Technology, and Applications, Bangalore, India, Jan. 8–10. https://doi.org/10.1109/VLSI-SATA.2015.7050469
Sakthivel SM, Ravi Sankar A (2016) Real time watermarking of grayscale images using integer DWT transform. Proceedings of the Int. Conf. on VLSI Systems, Architecture, Technology, and Applications, Bangalore, India Jan. 8–10. https://doi.org/10.1109/VLSI-SATA.2016.7593056
Shet KS, Aswath AR, Hanumanatharaju MC, Gao XZ (2016) Design and development of reconfigurable architectures for LSB/multi-bit image steganography system. Multimed Tools Appl 76(11):1–23
Singh AK (2017) Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimed Tools Appl 76(6):8881–8900
Tao H, Chongmin L, Zain JM, Abdalla AN (2014) Robust image watermarking theories and techniques: a review. J Appl Res Technol 12(1):122–138
Wong PW, Memon N (2001) Secret and public key image watermarking schemes for image authentication and ownership verification. IEEE Trans Image Process 10(10):1593–1601
Wong PHW, Au OC, Yeung YM (2003) A novel blind watermarking technique for images. IEEE Trans Circuits Syst Video Technol 13(8):813–830
Wu M, Liu B (2003) Data hiding in image and video: part I- fundamental issues and solutions. IEEE Trans Image Process 12(6):685–695
Zear A, Singh AK, Kumar P (2016) A proposed secure multiple watermarking technique based on DWT DCT and SVD for application in medicine. Multimed Tools Appl. https://doi.org/10.1007/s11042-016-03862-8
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sakthivel, S.M., Ravi Sankar, A. An ASIC based invisible watermarking of grayscale images using pixel value search algorithm (PVSA). Multimed Tools Appl 77, 26793–26819 (2018). https://doi.org/10.1007/s11042-018-5889-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5889-5