Abstract
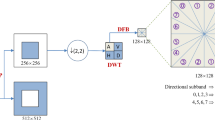
A novel imperceptible digital watermarking scheme in multiple transform domains is presented, where the cover image is dealt with by discrete wavelet transform (DWT), discrete cosine transform (DCT) and discrete fractional random transform (DFRNT), while the watermark image is scrambled by Arnold transform and logistic map. First the watermark is scrambled by the Arnold transform, then the row and the column of the resulting watermark are scrambled by the Logistic map, respectively. In addition, four sub-band images are generated from the host image by the two-dimensional discrete wavelet transform. The low-frequency sub-band images are divided into 8 × 8 small matrices, and a coefficient matrix is produced by performing the discrete cosine transform on each matrix. An intermediate matrix with the same size as the watermark image is constructed by the intermediate frequency coefficients. Then the discrete fractional random transformation is performed on the intermediate frequency coefficient matrix and the scrambled watermark is embedded into the discrete fractional random transformation domain. Compared with the previous schemes, the proposed digital watermarking scheme has stronger imperceptibility and robustness.











Similar content being viewed by others
References
Ali M, Chang WA (2014) An optimized watermarking technique based on self-adaptive DE in DWT-SVD transform domain. Signal Process 94(1):545–556
Ali M, Chang WA, Siarry P (2014) Differential evolution algorithm for the selection of optimal scaling factors in image watermarking. Eng Appl Artif Intell 31(31):15–26
Alsmirat MA, Al-Alem F, Al-Ayyoub M, Jararweh, Y, Gupta, B (2018) Impact of digital fingerprint image quality on the fingerprint recognition accuracy. Multimed Tools Appl, (4):1–40
Benrhouma O, Hermassi H, Abd El-Latif AA, Belghith S (2016) Chaotic watermark for blind forgery detection in images. Multimed Tools Appl 75(14):1–24
Chen X, Huang X, Li J, Ma J, Lou W, Wong DS (2014) New algorithms for secure outsourcing of large-scale systems of linear equations. IEEE Trans Info Forensics Sec 10(1):69–78
Choudhary R, Parmar G (2017) A robust image watermarking technique using 2-level discrete wavelet transform (DWT). International conference on communication control and intelligent systems, IEEE: 120–124
Das C, Panigrahi S, Sharma VK, Mahapatra KK (2014) A novel blind robust image watermarking in DCT domain using inter-block coefficient correlation. AEU - Int J Electron Commun 68(3):244–253. https://doi.org/10.1016/j.aeue.2013.08.018
Esgandari R, Student MS, Khalili M (2015) A robust image watermarking scheme based on discrete wavelet transforms. Int Conf Knowledge-Based Eng Innov, IEEE: 988–992
Fazli S, Moeini M (2016) A robust image watermarking method based on DWT, DCT, and SVD using a new technique for correction of main geometric attacks. Optik - Int J Light Electron Optics 127(2):964–972. https://doi.org/10.1016/j.ijleo.2015.09.205
Fridrich J, Kodovsky J (2012) Rich models for Steganalysis of digital images. IEEE Trans Info\ Forensics Sec 7(3):868–882. https://doi.org/10.1109/TIFS.2012.2190402
Guo Q, Liu ZJ, Liu ST (2008) Robustness analysis of image watermarking based on discrete fractional random transform. Opt Eng 47(5):057003
Halima NB, Hosam O (2015) Embedding image ROI watermark into median DCT coefficients. Int Rev Comput Softw 10(6):643
Hu HT, Hsu LY (2015) Robust, transparent and high-capacity audio watermarking in DCT domain. Signal Process 109(C:226–235
Huang Z, Liu S, Mao X, Chen K, Li J (2017) Insight of the protection for data security under selective opening attacks. Inf Sci 412–413:223–241
Khan A, Siddiqa A, Munib S, Malik SA (2014) A recent survey of reversible watermarking techniques. Inf Sci 279(279):251–272
Lai CC, Tsai CC (2010) Digital image watermarking using discrete wavelet transform and singular value decomposition. IEEE Trans Instrum Meas 59(11):3060–3063. https://doi.org/10.1109/TIM.2010.2066770
Li J, Li J, Chen X, Jia C, Lou W (2015) Identity-based encryption with outsourced revocation in cloud computing. IEEE Trans Comput 64(2):425–437. https://doi.org/10.1109/TC.2013.208
Li J, Li YK, Chen X, Lee PPC, Lou W (2015) A hybrid cloud approach for secure authorized deduplication. Parallel Distrib Syst IEEE Trans 26(5):1206–1216
Li P, Li J, Huang Z, Li T, Gao CZ, Yiu SM (2017) Multi-key privacy-preserving deep learning in cloud computing. Futur Gener Comput Syst 74(C:76–85
Liao X, Li K, Yin J (2016) Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed Tools Appl: 1–15, DOI: https://doi.org/10.13287/j.1001-9332.201609.038
Liu ZJ, Ahmad MA, Liu ST (2008) A discrete fractional angular transform. Opt Commun 281(6):1424–1429. https://doi.org/10.1016/j.optcom.2007.11.012
Luo H, Yu FX, Huang ZL, Lu ZM (2011) Blind image watermarking based on discrete fractional random transform and subsampling. Optik - Int J Light Electron Optics 122(4):311–316. https://doi.org/10.1016/j.ijleo.2009.12.018
Makbol NM, Khoo BE, Rassem TH (2016) Block-based discrete wavelet transform-singular value decomposition image watermarking scheme using human visual system characteristics. IET Image Process 10(1):34–52. https://doi.org/10.1049/iet-ipr.2014.0965
Mastan Vali SK, Naga Kishore KL, Prathibha G Robust image watermarking using Tetrolet transform. Int Conf Elect, Electron, Signals, Commun Optim 2015, 2015:1–5
Parah SA, Sheikh JA, Ahad F, Loan NA, Bhat GM (2017) Information hiding in medical images: a robust medical image watermarking system for E-healthcare. Multimed Tools Appl 76(8):10599–10633. https://doi.org/10.1007/s11042-015-3127-y
Rajawat M, Tomar DS (2015) A secure watermarking and tampering detection technique on RGB image using 2 level DWT. Fifth Int Conf Commun Syst Netw Technol, IEEE: 638–642
Roy S, Pal AK (2017) A blind DCT based color watermarking algorithm for embedding multiple watermarks. AEU - Int J Electron Commun 72:149–161. https://doi.org/10.1016/j.aeue.2016.12.003
Singh AK (2017) Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimed Tools Appl 76:1–18
Singh D, Singh SK (2015) DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76:1–25
Singh AK, Dave M, Mohan A (2014) Hybrid technique for robust and imperceptible image watermarking in DWT–DCT–SVD domain. Natl Acad Sci Lett 37(4):351–358. https://doi.org/10.1007/s40009-014-0241-8
Singh AK, Kumar B, Dave M, Mohan A (2015) Multiple watermarking on medical images using selective discrete wavelet transform coefficients. J Med Imaging Health Info 5(3):607–614(8). https://doi.org/10.1166/jmihi.2015.1432
Tang LL, Huang CT, Pan JS, Liu CY (2013) Dual watermarking algorithm based on the fractional Fourier transform. Multimed Tools Appl 74(12):1–17
Thind DK, Jindal S (2015) A semi blind DWT-SVD video watermarking. Proc Comput Sci 46:1661–1667. https://doi.org/10.1016/j.procs.2015.02.104
Wang B, Ding J, Wen Q, Liao X, Liu C (2009) An image watermarking algorithm based on DWT DCT and SVD. IEEE Int Conf Netw Infrastruct Digit Content, IC-NIDC IEEE: 1034–1038
Xie Y, Tan H, Wang K (2016) A novel color image hologram watermarking algorithm based on QDFT-DWT. Contrl Decision Conf IEEE: 4349–4354, DOI: https://doi.org/10.13287/j.1001-9332.201609.013
Ye X, Chen X, Deng M, Wang Y (2015) A SIFT-based DWT-SVD blind watermark method against geometrical attacks. International congress on image and signal processing, IEEE: 323–329
Yu C, Li J, Li X, Ren X, Gupta BB (2018) Four-image encryption scheme based on quaternion fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77(4):4585–4608. https://doi.org/10.1007/s11042-017-4637-6
Zear A, Singh AK, Kumar P (2016) A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed Tools Appl: 1–20
Zhang C, Wang J, Wang X (2008) Digital image watermarking algorithm with double encryption by Arnold transform and logistic. Int Conf Netw Comput Adv Info Manag, IEEE, pp 329–334, DOI: https://doi.org/10.3824/stembook.1.53.1
Zhang X, Ren Y, Shen L, Qian Z, Feng G (2014) Compressing encrypted images with auxiliary information. IEEE Trans Multimed 16(5):1327–1336. https://doi.org/10.1109/TMM.2014.2315974
Zhou NR, Dong TJ, Wu JH (2010) Novel image encryption algorithm based on multiple-parameter discrete fractional random transform. Opt Commun 283(15):3037–3042. https://doi.org/10.1016/j.optcom.2010.03.064
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61462061 and 61561033), the China Scholarship Council (Grant No. 201606825042), the Department of Human Resources and Social security of Jiangxi Province, the Major Academic Discipline and Technical Leader of Jiangxi Province (Grant No. 20162BCB22011), and the Natural Science Foundation of Jiangxi Province (Grant No. 20171BAB202002).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhou, N.R., Hou, W.M.X., Wen, R.H. et al. Imperceptible digital watermarking scheme in multiple transform domains. Multimed Tools Appl 77, 30251–30267 (2018). https://doi.org/10.1007/s11042-018-6128-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6128-9