Abstract
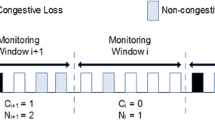
In order to reflect the network transmission quality, some network state feedback mechanisms are provided in the network protocol. In the RTP, the jitter of the packet transmission delay is fed back through the jitter field in the RTCP packet. This feedback value is a very important reference data when the covert timing channel is established. However, the sending frequency of the RTCP packet is low and the feedback value of the RTCP packet are only the jitter value of the last RTP packet associated with this RTCP packet when it is sent. Therefore, the jitter feedback mechanism in the existing RTCP protocol has the problem of lack of feedback on the network state during the period between two RTCP data packets. As a result, the feedback value is highly susceptible to extreme values, which prevents it from providing an accurate numerical reference for establishing covert channels. Therefore, in this paper, a buffer was established between the last RTCP packet and the current RTCP packet. And we choose to set the interval is n RTP packets and record the corresponding position jitter value in the buffer. The data in the buffer is averaged, and the mean value is weighted and averaged with the jitter value of the current RTCP packet as a new jitter feedback value. The effect of the extreme value on the feedback value is reduced, thereby it contribute to the improvement of the feedback energy for the state of the network. In addition, the bit error rate generated by establishing a simple covert timing channel for data transmission under different network conditions is compared with the change of two jitter feedback values. It is verified that there is a positive correlation between the feedback value of the new feedback mode and the error rate. through the comparison It is verified that the new feedback method can provide a more accurate reference for the establishment of covert channels.







Similar content being viewed by others
References
Al-Ayyoub M, AlzuBi S, Jararweh Y, Shehab MA, Gupta B (2016) Accelerating 3d medical volume segmentation using gpus. Multimed Tools Appl 77(4):4939–4958. https://doi.org/10.1007/s11042-016-4218-0
Andreadis A, Rizzuto S, Zambon R (2016) A cross-layer jitter-based tcp for wireless networks. Eurasip J Wireless Commun Network 2016(1):191. https://doi.org/10.1186/s13638-016-0695-0
Archibald R, Ghosal D (2012) A covert timing channel based on fountain codes. In: IEEE International conference on trust, security and privacy in computing and communications, pp 970–977. https://doi.org/10.1109/TrustCom.2012.21
Atawneh S, Almomani A, Bazar HA, Sumari P, Gupta B (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in dwt domain. Multimed Tools Appl 76 (18):18,451–18,472. https://doi.org/10.1007/s11042-016-3930-0
Biswas AK, Ghosal D, Nagaraja S (2017) A survey of timing channels and countermeasures, 50. https://doi.org/10.1145/3023872
Cabuk S, Brodley CE, Shields C (2004) Ip covert timing channels: design and detection. In: Proceedings of the 11th ACM conference on computer and communications security, pp 178–187. https://doi.org/10.1145/1030083.1030108
Carle G, Biersack EW (1997) Survey of error recovery techniques for ip-based audio-visual multicast applications. IEEE Netw 11(6):24–36. https://doi.org/10.1109/65.642357
Chang X, Yang Y (2017) Semisupervised feature analysis by mining correlations among multiple tasks. IEEE Trans Neural Netw Learn Syst 28 (10):2294–2305. https://doi.org/10.1109/TNNLS.2016.2582746
Chang X, Nie F, Wang S, Yang Y, Zhou X, Zhang C (2014) Compound rank-k projections for bilinear analysis. IEEE Trans Neural Netw Learn Syst 27 (7):1502–1513. https://doi.org/10.1109/TNNLS.2015.2441735
Chang X, Nie F, Yang Y, Zhang C, Huang H (2016) Convex sparse pca for unsupervised feature learning. Acm Trans Knowl Discov Data 11(1):3:1–3,16. https://doi.org/10.1145/2910585
Chang X, Ma Z, Lin M, Yang Y, Hauptmann AG (2017) Feature interaction augmented sparse learning for fast kinect motion detection. IEEE Trans Image Process 26 (8):3911–3920. https://doi.org/10.1109/TIP.2017.2708506
Chang X, Ma Z, Yi Y, Zeng Z, Hauptmann AG (2017) Bi-level semantic representation analysis for multimedia event detection. IEEE Trans Cybern 47(5):1180–1197. https://doi.org/10.1109/TCYB.2016.2539546
Chang X, Yu YL, Yang Y, Xing EP (2017) Semantic pooling for complex event analysis in untrimmed videos. IEEE Trans Pattern Anal Mach Intell 39 (8):1617–1632. https://doi.org/10.1109/TPAMI.2016.2608901
Chen Z, Peng L, Gao C, Yang B, Chen Y, Li J (2017) Flexible neural trees based early stage identification for ip traffic. Soft Comput 21(8):2035–2046. https://doi.org/10.1007/s00500-015-1902-3
Denby L, Landwehr JM, Mallows CL, Meloche J, Tuck J, Xi B, Michailidis G, Nair VN (2007) Statistical aspects of the analysis of data networks. Technometrics 49(3):318–334. https://doi.org/10.1198/004017007000000290
Gianvecchio S, Wang H, Wijesekera D, Jajodia S (2008) Model-based covert timing channels: automated modeling and evasion. In: International Symposium on recent advances in intrusion detection, pp 211–230
Guan Z, Li J, Wu L, Zhang Y, Wu J, Du X (2017) Achieving efficient and secure data acquisition for cloud-supported internet of things in smart grid. IEEE Internet Things J 4(6):1934–1944. https://doi.org/10.1109/JIOT.2017.2690522
Guan Z, Li J, Zhu L, Zhang Z, Du X, Guizani M (2017) Towards delay-tolerant flexible data access control for smart grid with renewable energy resources. IEEE Trans Indus Inform 13(6):3216–3225. https://doi.org/10.1109/TII.2017.2706760
Hastyo WJ, Kang CG (2014) Lte network emulator for volte service. Nmr Biomed 22(2):191–198
He B, Yan S, Zhou X, Lau VKN (2017) On covert communication with noise uncertainty. IEEE Commun Lett 21(4):941–944. https://doi.org/10.1109/LCOMM.2016.2647716
Huang Z, Liu S, Mao X, Chen K, Li J (2017) Insight of the protection for data security under selective opening attacks. Inform Sci 412-413:223–241. https://doi.org/10.1016/2017.05.031
Imputato P, Avallone S (2018) An analysis of the impact of network device buffers on packet schedulers through experiments and simulations. Simul Model Pract Theory 80:1–18. https://doi.org/10.1016/2017.09.008
Jararweh Y, Al-Ayyoub M, Fakirah M, Alawneh L, Gupta B (2017) Improving the performance of the needleman-wunsch algorithm using parallelization and vectorization techniques. Multimed Tools Appl 3:1–17. https://doi.org/10.1007/s11042-017-5092-0
Jouihri Y, Guennoun Z, Chagh Y, Zahi D (2017) Towards successful volte and vowifi deployment: network function virtualization solutions benefits and challenges. Telecommun Syst 64(3):467–478. https://doi.org/10.1007/s11235-016-0186-y
Jung TJ, Seo KD (2016) A client-driven media synchronization mechanism for rtp packet-based video streaming. J Real-Time Image Proc 12 (2):455–464. https://doi.org/10.1007/s11554-015-0497-3
Kumar R, Ganguly S, Izmailov R, Dan R (2006) Performance optimization of voip using an overlay network. J Non Cryst Solids 144(2):247–252
Li J, Li J, Chen X, Jia C, Lou W (2015) Identity-based encryption with outsourced revocation in cloud computing. IEEE Trans Comput 64(2):425–437. https://doi.org/10.1109/TC.2013.208
Li J, Zhang Y, Chen X, Xiang Y (2017) Preserving privacy with probabilistic indistinguishability in weighted social networks. IEEE Trans Parallel Distrib Syst 28(5):1417–1429. https://doi.org/10.1109/TPDS.2016.2615020
Li J, Zhang Y, Chen X, Xiang Y, Li J, Zhang Y, Chen X, Xiang Y (2017) Secure attribute-based data sharing for resource-limited users in cloud computing. Comput Secur 72:1–12. https://doi.org/10.1016/2017.08.007
Li P, Li J, Huang Z, Gao CZ, Chen WB, Chen K (2017) Privacy-preserving outsourced classification in cloud computing. Clust Comput, 1–10. https://doi.org/10.1007/s10586-017-0849-9
Qi W, Ding W, Wang X, Jiang Y, Xu Y, Wang J, Lu K (2018) Construction and mitigation of user-behavior-based covert channels on smartphones. IEEE Trans Mob Comput 17(1):44–57. https://doi.org/10.1109/TMC.2017.2696945
Qiu L, Zhang Y, Wang F, Kyung M, Mahajan HR (1985) Trusted computer system evaluation criteria. In: National Computer security center
Rezaei F, Hempel M, Sharif H (2017) Towards a reliable detection of covert timing channels over real-time network traffic. IEEE Trans Depend Secur Comput 14(3):249–264. https://doi.org/10.1109/TDSC.2017.2656078
Schulzrinne H (1995) Internet services: from electronic mail to real-time multimedia. Springer, Berlin, pp 21–34
Schulzrinne H, Casner S, Frederick R, Jacobson V (1996) Rtp: a transport protocol for real-time applications. Ietf Rfc 2(2):459C482
Shen J, Gui Z, Ji S, Shen J, Tan H, Tang Y (2018) Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. Journal of Network and Computer Applications. https://doi.org/10.1016/j.jnca.2018.01.003
Sun L, Li Z, Yan Q, Srisa-An W, Pan Y (2017) Sigpid: significant permission identification for android malware detection. In: International Conference on malicious and unwanted software, pp 1–8. https://doi.org/10.1109/MALWARE.2016.7888730
Szpyrka M (2013) Fast and flexible modelling of real-time systems with rtcp-nets. Comput Sci 6(5):81
Wang YH, Chow TH (2016) Applying patent-based fuzzy quality function deployment to explore prospective volte technologies. Int J Fuzzy Syst 18(3):424–435
Wu Z, Xu Z, Wang H (2015) Whispers in the hyper-space: high-bandwidth and reliable covert channel attacks inside the cloud. IEEE/ACM Trans Netw 23(2):603–614. https://doi.org/10.1109/TNET.2014.2304439
Xue Y, Tan YA, Liang C, Zhang C, Zheng J (2018) An optimized data hiding scheme for deflate codes. Soft Comput 22(13):4445–4455. https://doi.org/10.1007/s00500-017-2651-2
Zhang X, Tan YA, Xue Y, Zhang Q, Li Y, Zhang C, Zheng J (2017) Cryptographic key protection against frost for mobile devices. Cluster Comput 20(3):2393–2402. https://doi.org/10.1007/s10586-016-0721-3
Zhang X, Tan YA, Zhang C, Xue Y, Li Y, Zheng J (2018) A code protection scheme by process memory relocation for android devices. Multimed Tools Appl 77(9):11137–11157. https://doi.org/10.1007/s11042-017-5363-9
Zhu H, Tan YA, Zhang X, Zhu L, Zhang C, Zheng J (2017) A round-optimal lattice-based blind signature scheme for cloud services. Futur Gener Comput Syst 73:106–114. https://doi.org/10.1016/2017.01.031
Zhu R, Zhang B, Mao J, Zhang Q, Tan YA (2017) A methodology for determining the image base of arm-based industrial control system firmware. Int J Crit Infrastruct Prot 16:26–35. https://doi.org/10.1016/2016.12.002
Zhu H, Tan YA, Yu X, Zhang XY, Zhu QL, Li Y (2018) An identity-based proxy signature on ntru lattice. Chinese J Electron 27(2):297–303(6). https://doi.org/10.1049/2017.09.008
Zkik K, Orhanou G, Hajji SE (2017) Secure mobile multi cloud architecture for authentication and data storage IGI global. https://doi.org/10.4018/IJCAC.2017040105
Acknowledgements
This paper was supported by the National Natural Science Foundation of China (No.U1636213).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhang, Q., Gong, H., Zhang, X. et al. A sensitive network jitter measurement for covert timing channels over interactive traffic. Multimed Tools Appl 78, 3493–3509 (2019). https://doi.org/10.1007/s11042-018-6281-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6281-1