Abstract
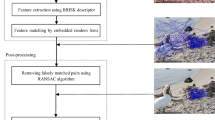
Copy-move (region duplication) is one of the most common types of image forgeries, in which at least one part of an image is copied and pasted onto another area of the same image. The main aims of the copy-move forgery are to overemphasize a concept or conceal objects by duplicating some regions. Keypoint based copy-move forgery detection (CMFD) method extracts image feature points and employs local image features to identify duplicated regions, which exhibits remarkable detection performance with respect to memory requirement, computational cost, and robustness. However, they usually do not work well when the objects are hidden in smooth background areas. Also, the detection and localization accuracy always be lowered because of poor local image feature computation. In this paper, we present a novel approach for the detection and localization of copy-move forgeries, which is based on color invariance SIFER (Scale-invariant feature detector with error resilience) and FQRHFMs (Fast quaternion radial harmonic Fourier moments). Firstly, the original forgery image is segmented into nonoverlapping and nearly uniform superpixel blocks, and the stable keypoints are extracted adaptively from each superpixel block by incorporating the superpixel contents and color invariance SIFER. Secondly, a set of connected Delaunay triangles is constructed using the extracted image keypoints, and suitable local image feature for each Delaunay triangle is computed by using FQRHFMs and gradient entropy. Thirdly, the local image features and coherency sensitive hashing (CSH) are utilized to match quickly the Delaunay triangles. Finally, the falsely matched Delaunay triangles are removed by employing dense linear fitting (DLF), and the duplicated regions are localized using optimized zero mean normalized cross-correlation (ZNCC) measure. We conduct extensive experiments to evaluate the performance of the proposed copy-move forgery detection scheme, in which encouraging results validate the effectiveness of the proposed technique.


















Similar content being viewed by others
References
Abdel-Hakim AE, Farag AACSIFT (2006) A SIFT descriptor with color invariant characteristics[C]//computer vision and pattern recognition. 2006 IEEE Computer Society Conference on IEEE 2:1978–1983
Achanta R, Shaji A, Smith K et al (2012) SLIC superpixels compared to state-of-the-art superpixel methods[J]. IEEE Trans Pattern Anal Mach Intell 34(11):2274–2282
Amerini I, Ballan L, Caldelli R et al (2011) A SIFT-based forensic method for copy–move attack detection and transformation recovery[J]. IEEE Transactions on Information Forensics and Security 6(3):1099–1110
Amerini I, Ballan L, Caldelli R et al (2013) Copy-move forgery detection and localization by means of robust clustering with J-linkage[J]. Signal Process Image Commun 28(6):659–669
Ardizzone E, Bruno A, Mazzola G (2015) Copy–move forgery detection by matching triangles of keypoints[J]. IEEE Transactions on Information Forensics and Security 10(10):2084–2094
Aymaz S, Aymaz Ş, Ulutaş G (2016) Detection of copy move forgery using Legendre Moments[C]//Signal Processing and Communication Application Conference (SIU), 2016 24th. IEEE, 2016: 1125–1128
Bo X, Junwen W, Guangjie L, et al. (2010) Image copy-move forgery detection based on SURF[C]//Multimedia information networking and security (MINES), 2010 international conference on. IEEE, 889–892
Bravo-Solorio S, Nandi AK (2011) Exposing duplicated regions affected by reflection, rotation and scaling[C]//Acoustics, Speech and Signal Processing (ICASSP), 2011 IEEE International Conference on. IEEE, 2011: 1880–1883
Bravo-Solorio S, Nandi AK (2011) Automated detection and localisation of duplicated regions affected by reflection, rotation and scaling in image forensics[J]. Signal Process 91(8):1759–1770
Cao M (2015) A new Delaunay triangulation algorithm based on constrained maximum circumscribed circle[J]. Wuhan University Journal of Natural Sciences 20(4):313–317
Cao Y, Gao T, Fan L et al (2012) A robust detection algorithm for copy-move forgery in digital images.[J]. Forensic Sci Int 214(1–3):33–43
Chambers J, Yan W, Garhwal A et al (2015) Currency security and forensics: a survey[J]. Multimedia Tools and Applications 74(11):4013–4043
Christlein V, Riess C, Jordan J et al (2012) An evaluation of popular copy-move forgery detection approaches[J]. IEEE Transactions on information forensics and security 7(6):1841–1854
Chun-peng W, Xing-yuan W, Zhi-qiu X (2016) Geometrically invariant image watermarking based on fast radial harmonic Fourier moments[J]. Signal Process Image Commun 45:10–23
Cozzolino D, Poggi G, Verdoliva L (2014) Copy-move forgery detection based on patchmatch[C]//Image Processing (ICIP), 2014 IEEE International Conference on. IEEE, 2014: 5312–5316
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copy–move forgery detection[J]. IEEE Transactions on Information Forensics and Security 10(11):2284–2297
Davarzani R, Mozaffari S, Yaghmaie K (2016) Perceptual image hashing using center-symmetric local binary patterns[J]. Multimedia Tools and Applications 75(8):4639–4667
Emam M, Han Q, Niu X (2016) PCET based copy-move forgery detection in images under geometric transforms[J]. Multimedia Tools & Applications 75(18):11513–11527
Gong J, Guo J (2016) Image copy-move forgery detection using SURF in opponent color space[J]. Transactions of Tianjin University 22(2):151–157
Hu H, Zhang Y, Shao C et al (2014) Orthogonal moments based on exponent functions: exponent-Fourier moments[J]. Pattern Recogn 47(8):2596–2606
Isaac MM, Wilscy M (2015) Copy-Move forgery detection based on Harris Corner points and BRISK[C]//Proceedings of the Third International Symposium on Women in Computing and Informatics. ACM, 2015: 394–399
Korman S, Avidan S (2016) Coherency sensitive hashing[J]. IEEE Trans Pattern Anal Mach Intell 38(6):1099–1112
Li L, Li S, Zhu H et al (2014) Detecting copy-move forgery under affine transforms for image forensics[J]. Computers & Electrical Engineering 40(6):1951–1962
Li C, Ma Q, Xiao L, et al (2016) An Image Copy Move Forgery Detection Method Using QDCT[C]//Proceedings of the International Conference on Internet Multimedia Computing and Service. ACM, 2016: 5–8
Lin C, Li Y, Xu G et al (2017) Optimizing ZNCC calculation in binocular stereo matching[J]. Signal Process Image Commun 52:64–73
Liu MY, Tuzel O, Ramalingam S et al (2014) Entropy-rate clustering: cluster analysis via maximizing a submodular function subject to a matroid constraint[J]. IEEE Trans Pattern Anal Mach Intell 36(1):99–112
Liu Y, Nie L, Han L, Zhang L, Rosenblum DS (2015) Action2activity: recognizing complex activities from sensor data. Proceedings of the 24th International Joint Conference on Artificial Intelligence (IJCAI 2015) 1617–1623
Liu Y, Zhang L, Nie L, Yan Y, Rosenblum DS (2016) Fortune teller: predicting your career path. Proceedings of the Thirtieth AAAI Conference on Artificial Intelligence (AAAI-16), 2016: 201–207
Mainali P, Lafruit G, Yang Q et al (2013) SIFER: scale-invariant feature detector with error resilience[J]. Int J Comput Vis 104(2):172–197
Oommen R S, Jayamohan M, Sruthy S (2016) Scale invariant detection of copy-move forgery using fractal dimension and singular values[M]//Advances in Signal Processing and Intelligent Recognition Systems. Springer, Cham, 2016: 559–570
Pan X, Lyu S (2010) Region duplication detection using image feature matching[J]. IEEE Transactions on Information Forensics and Security 5(4):857–867
Pun CM, Yuan XC, Bi XL (2015) Image forgery detection using adaptive oversegmentation and feature point matching[J]. IEEE Transactions on Information Forensics and Security 10(8):1705–1716
Ren H, Ping Z, Bo W et al (2003) Multidistortion-invariant image recognition with radial harmonic Fourier moments[J]. JOSA A 20(4):631–637
Ryu SJ, Kirchner M, Lee MJ et al (2013) Rotation invariant localization of duplicated image regions based on Zernike moments[J]. IEEE Transactions on Information Forensics and Security 8(8):1355–1370
Thirunavukkarasu V, Kumar J S, Chae G S, et al (2017) Non-intrusive Forensic Detection Method Using DSWT with Reduced Feature Set for Copy-Move Image Tampering[J]. Wireless Personal Communications, 2017:1–19
Üstübi̇oğlu B, Ayas S, Doğan H, et al (2015) Image forgery detection based on Colour SIFT[C]//Signal Processing and Communications Applications Conference (SIU), 2015 23th. IEEE, 2015: 1741–1744
Wang J, Liu G, Li H et al (2009) Detection of image region duplication forgery using model with circle block[C]//multimedia information networking and security, 2009. MINES'09. International conference on. IEEE 1:25–29
Warif NBA, Wahab AWA, Idris MYI et al (2016) Copy-move forgery detection: survey, challenges and future directions[J]. Journal of Network & Computer Applications 75:259–278
Wo Y, Yang K, Han G et al (2016) Copy–move forgery detection based on multi-radius PCET[J]. IET Image Process 11(2):99–108
Xiang-yang W, Wei-yi L, Hong-ying Y et al (2015) Invariant quaternion radial harmonic Fourier moments for color image retrieval[J]. Opt Laser Technol 66:78–88
Yang B, Sun X, Guo H, et al (2017) A copy-move forgery detection method based on CMFD-SIFT[J]. Multimedia Tools and Applications, 2017: 1–19
Zhao J, Zhao W (2013) Passive Forensics for Region Duplication Image Forgery Based on Harris Feature Points and Local Binary Patterns[J]. Mathematical Problems in Engineering, (2013–12-29), 2013, 2013(4):1–12
Zhao F, Shi W, Qin B, et al (2016) Analysis of SIFT Method Based on Swarm Intelligent Algorithms for Copy-Move Forgery Detection[C]//Security, Privacy, and Anonymity in Computation, Communication, and Storage: 9th International Conference, SpaCCS 2016, Zhangjiajie, China, November 16–18, 2016, Proceedings 9. Springer International Publishing, 2016: 478–490
Zheng J, Liu Y, Ren J et al (2016) Fusion of block and keypoints based approaches for effective copy-move image forgery detection[J]. Multidim Syst Sign Process 27(4):989–1005
Zhu Y, Shen X, Chen H (2016) Copy-move forgery detection based on scaled ORB[J]. Multimedia Tools & Applications 75(6):3221–3233
Funding
This work was supported by the National Natural Science Foundation of China under Grant No. 61472171, 61272416, &61701212, Project Funded by China Postdoctoral Science Foundation No. 2017 M621135, and the Natural Science Foundation of Liaoning Province of China under Grant No. 201602463.
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, Xy., Jiao, Lx., Wang, Xb. et al. Copy-move forgery detection based on compact color content descriptor and Delaunay triangle matching. Multimed Tools Appl 78, 2311–2344 (2019). https://doi.org/10.1007/s11042-018-6354-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6354-1