Abstract
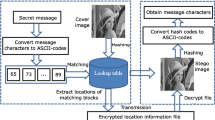
In traditional information hiding methods, the secret information is embedded into the carriers, which will inevitably leave traces of modification on the carriers. In those methods, the modified images can be easily detected by some steganalysis algorithm and thus the security can not be guaranteed. To address this problem, the concept of coverless information hiding is proposed. However, general coverless information hiding method has a lower information hiding capacity. In this paper, we propose a novel coverless information hiding method based on the average pixel values of sub-images. We generate hash sequences by a hashing algorithm and realize the secret information hiding through mapping relationship. In the first place, we build a dictionary and a hash array. Then we map the dictionary and the hash array through mapping relationship. Furthermore, we build a multi-level index structure for retrieving the stego-images efficiently. The experimental results and analysis show that our method has a good performance in the capacity of information hiding, the security, the robustness to image attacks and the hiding success rate based on different image databases.









Similar content being viewed by others
References
Cao Y, Zhou Z, Sun X, Gao C (2018) Coverless information hiding based on the molecular structure images of material. CMC: Comput Mater Continua 54(2):197–207
Chang CC, Kieu TD, Chou YC (2009) Reversible information hiding for VQ indices based on locally adaptive coding[J]. J Vis Commun Image Represent 20(1):57–64
Cheddad A, Condell J, Curran K et al (2010) Review: digital image steganography: survey and analysis of current methods[J]. Signal Process 90(3):727–752
Chen WY (2007) Color image steganography scheme using set partitioning in hierarchical trees coding, digital Fourier transform and adaptive phase modulation[J]. Appl Math Comput 185(1):432–448
Cox IJ, Miller ML (2002) The First 50 Years of Electronic Watermarking. J Appl Sign Proc (2): 126–132
Guo L, Ni J, Su W et al (2015) Using statistical image model for JPEG steganography: uniform embedding revisited[J]. IEEE Trans Info Forensic Sec 10(12):2669–2680
Hirohisa H (2002) A data embedding method using BPCS principle with new complexity measures[J]
Johnson NF, Jajodia S (1998) Exploring steganography: seeing the unseen[J]. Computer 31(2):26–34
Kawaguchi E (2005) BPCS-Steganography – Principle and Applications[C]// International Conference on Knowledge-Based and Intelligent Information and Engineering Systems. Springer Berlin Heidelberg 289–299
Ker AD (2004) Improved detection of LSB steganography in grayscale images[C]// International Conference on Information Hiding. Springer-Verlag 97–115
Ker AD (2005) Steganalysis of LSB matching in grayscale images[J]. IEEE Sign Proc Lett 12(6):441–444
Li X, Wang J (2007) A steganographic method based upon JPEG and particle swarm optimization algorithm. Inf Sci 177(15):3099–3109
Li Z, Chen X, Pan X et al (2009) Lossless data hiding scheme based on adjacent pixel difference[J]. IEEE 1(1):588–592
Lin W, Horng S, Kao T (2008) An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Trans Multimed 10(5):746–757
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited[J]. IEEE Trans Info Forensic Sec 5(2):201–214
Ma Y, Luo X, Li X, et al. (2018) Selection of Rich Model Steganalysis Features Based on Decision Rough Set 伪-Positive Region Reduction[J]. IEEE Trans Circuits Syst Video Technol (99):1–1
Mckeon RT (2007) Strange fourier steganography in movies[C]// IEEE International Conference on Electro/information Technology. IEEE 178–182
Meng R, Steven G, Wang J, Sun X (2018) A fusion Steganographic algorithm based on faster R-CNN. CMC: Comput Mater Continua 55(1):1–16
Mielikainen J (2006) LSB matching revisited[J]. IEEE Sign Proc Lett 13(5):285–287
Pevny T, Fridrich J (2013) Merging Markov and DCT features for multi-class JPEG steganalysis. Proc SPIE - Int Soc Opt Eng 3:650503–650503
Ren X, Zheng Y, Zhao Y et al (2018) Drusen segmentation from retinal images via supervised feature learning. IEEE Acces 6:2952–2961
Wan W, Liu J, Sun J, et al. (2013) Logarithmic spread-transform dither modulation watermarking based on perceptual model[C]//Image Processing (ICIP), 2013 20th IEEE International Conference on. IEEE 4522–4526
Wan W, Liu J, Sun J et al (2015) Logarithmic STDM watermarking using visual saliency-based JND model[J]. Electron Lett 51(10):758–760
Wang J, Li T, Shi YQ et al (2017) Forensics feature analysis in quaternion wavelet domain for distinguishing photographic images and computer graphics[J]. Multimed Tools Appl 76(22):23721–23737
Wu HC, Wu NI, Tsai CS et al (2005) Image steganographic scheme based on pixel-value differencing and LSB replacement methods[J]. Vision, Image Sign Proc IEE Proc 152(5):611–615
Xia Z, Wang X, Sun X et al (2014) Steganalysis of least significant bit matching using multi-order differences[J]. Sec Commun Netw 7(8):1283–1291
Xia Z, Wang X, Sun X et al (2016) Steganalysis of LSB matching using differences between nonadjacent pixels[J]. Multimed Tools Appl 75(4):1947–1962
Yang C, Weng C, Wang S (2008) Adaptive data hiding in edge areas of images with spatial LSB domain systems. IEEE Trans Info Forensic Sec 3(3):488–497
Yuan C, Xia Z, Sun X (2017) Coverless Image Steganography Based on SIFT and BOF[J]. Internet J Technol 18
Yuan Z, Guan Z, Feng H (2017) An improved information hiding algorithm based on image[C]// IEEE, International Conference on Software Engineering Research, Management and Applications. IEEE 169–172
Zhang J, Shen J, Wang L et al. (2016) Coverless Text Information Hiding Method Based on the Word Rank Map[M]// Cloud Computing and Security. Springer International Publishing 145–155
Zhang Y, Qin C, Zhang W, et al. (2018) On the Fault-tolerant Performance for a Class of Robust Image Steganography[J]. Signal Processing
Zheng S, Wang L, Ling B (2017) Coverless Information Hiding Based on Robust Image Hashing. Int Conf Cloud Comput Sec 536–547
Zhou Z, Sun H, Harit R, et al. (2015) Coverless Image Steganography Without Embedding[C]// International Conference on Cloud Computing and Security. Springer, Cham 123–132
Zhou Q, Qiu Y, Li L, Lu J et al (2018) Steganography using reversible texture synthesis based on seeded region growing and LSB. CMC: Comput Mater Continua 55(1):151–163
Acknowledgements
This work is supported by the Natural Science Foundation of China (U1736122), the Natural Science Foundation for Distinguished Young Scholars of Shandong Province (JQ201718) and Shandong Provincial Key Research and Development Plan (2017CXGC1504).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zou, L., Sun, J., Gao, M. et al. A novel coverless information hiding method based on the average pixel value of the sub-images. Multimed Tools Appl 78, 7965–7980 (2019). https://doi.org/10.1007/s11042-018-6444-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6444-0