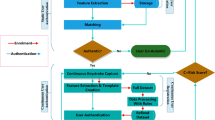
Abstract
Providing fixed re-authentication attempts to the user in case of password mismatch is a very old concept. But as password based authentication mechanisms are prone to many security attacks, user’s biometric properties along with passwords are highly in use for user authentication these days. It will be more secure and convenient if re-authentication influenced by the biometric behavior of the user is applied in the authentication system. It is a challenging task to identify a genuine user using behavioral biometric due to its low repeatability and wide variation. So, to increase the efficiency and robustness of the authentication system in case of score mismatch, the clustering of user’s behavior and assigning different re-authentication attempt to different cluster is needed. In this paper, we have proposed a transparent fixed text, keystroke based user authentication framework, which will enhance the security of traditional password based authentication mechanism. A new classification algorithm and dynamic attempt allocation algorithm have been proposed which will make the authentication system smart enough to provide the genuine user a fare authentication attempt.






Similar content being viewed by others
References
Ahmed A, Traore I (2007) A new biometric technology based on mouse dynamics. IEEE Trans Dependable Secure Comput 4:165e79
Azevedo GLFBG, Cavalcanti GDC, Edson CB, Filho C (2007) An approach to feature selection for keystroke dynamics systems based on PSO and feature weighting. In: Evolutionary Computation, 2007. CEC IEEE Congress on, pp 3577-3584. IEEE
Balagani KS, Phoha VIRV, Ray A, Phoha S (2011) On the discriminability of keystroke feature vectors used in fixed text keystroke authentication. Pattern Recogn Lett 32(7):1070–1080
Bhattacharyya D, Ranjan R, Alisherov F, Choi M (2009) Biometric authentic: a review. Int J Serv Sci Technol 2:13e28
Chandrasekar V, Suresh Kumar S, Maheswari T (2016) Authentication based on keystroke dynamics using stochastic diffusion algorithm. Stoch Anal Appl 34(1):155–164
Cho S, Hwang S (2006) Artificial rhythms and cues for keystroke dynamics based authentication. In: International conference on biometrics. Springer, Berlin, pp 626–632
Danielsson P-E (1980) Euclidean distance mapping. Comput Graphics Image Process 14(3):227–248
Davoudi H, Kabir E (2009) A new distance measure for free text keystroke authentication. In: Computer Conference CSICC 2009. 14th International CSI, pp. 570–575. IEEE
Garcia JD (1986) Personal identification apparatus. U.S. Patent 4,621,334 issued November 4
Giot R, El-Abed M, Hemery B, Rosenberger C (2011) Unconstrained keystroke dynamics authentication with shared secret. Comput Secur 30(6):427–445
Gong L, Pan J, Liu B, Zhao S (2013) A novel one-time password mutual authentication scheme on sharing renewed finite random sub-passwords. J Comput Syst Sci 79(1):122–130
Hartigan JA, Wong MA (1979) Algorithm AS 136: A k-means clustering algorithm. J R Stat Soc Ser C Appl Stat 28(1):100–108
Hempstalk K, Frank E, Witten IH (2008) One-class classification by combining density and class probability estimation. In: Joint european conference on machine learning and knowledge discovery in databases. Springer, Berlin, pp 505–519
Ho J, Kang D-K (2018) One-class nave Bayes with duration feature ranking for accurate user authentication using keystroke dynamics. Appl Intell 48(6):1547–1564
Hocquet S, Ramel J-Y, Cardot H (2005) Fusion of methods for keystroke dynamic authentication. In: IEEE workshop on automatic identification advanced technologies 4th, pp 224-229. IEEE
Hocquet S, Ramel J-Y, Cardot H (2007) User classification for keystroke dynamics authentication. Advances in biometrics, pp 531–539
Hong L, Jain AK (1998) Integrating faces and fingerprints for personal identification. IEEE Trans Pattern Anal Mach Intell 20(12):1295–1307
Huang Y, Huang Z, Zhao H, Lai X (2013) A new one-time password method. IERI Procedia 4:32–37
Im S, Park H, Kim Y, Han S, Kim S, Kang C, Chung C (2001) A biometric identification system by extracting hand vein patterns, journal of the korean physical society. Korean Publ 38(3):268–272
Jain AK, Ross A, Prabhakar S (2004) An introduction to biometric recognition. IEEE Trans Circuits Syst Video Technol 14(1):4–20
Koakowska A (2018) Usefulness of keystroke dynamics features in user authentication and emotion recognition. In: Human-Computer Systems Interaction. Springer, Cham, pp 42–52
Kukula E, Elliott S (2001) Implementation of Hand Geometry at Purdue University’s Recreational Center: An Analysis of User Perspectives and System Performance. In: Proc. of 35th annual international carnahan conference on security technology, UK, pp 83–88
Kumar A, Wong DC, Shen HC, Jain AK (2003) Personal Verification using Palmprint and Hand Geometry Biometric. In: Proc. of 4th international conference on audio- and video-based biometric person authentication, Guildford, UK, pp 668–678
Lee N-Y, Chiu Y-C (2005) Improved remote authentication scheme with smart card. Computer Standards and Interfaces 27(2):177–180
Liew K-M, Shen H, See S, Cai W, Fan P, Horiguchi S (eds) (2004) Parallel and distributed computing: Applications and technologies: 5th international conference, PDCAT 2004, vol 3320. Springer, Singapore. Proceedings
Marcolin F, Vezzetti E (2017) Novel descriptors for geometrical 3D face analysis. Multimed Tools Appl 76(12):13805–13834
Mariño C, Penedo MG, Penas M, Carreira MJ, Gonzalez F (2006) Personal authentication using digital retinal images. Pattern Anal Applic 9(1):21
Matsumoto T, Hoshino H, Yamada K, Hasino S (2002) Impact of artificial gummy fingers on fingerprint systems. In Proc SPIE 4677:275–289
Monrose F, Rubin AD (2000) Keystroke dynamics as a biometric for authentication. Futur Gener Comput Syst 16(4):351–359
Prabhakar S, Pankanti S, Jain AK (2003) Biometric recognition: Security and privacy concerns. IEEE Secur Priv 99(2):33–42
Prakash M, Viju P, Infant A, Shobana J (2010) Eliminating vulnerable attacks using one time password and passtext analytical study of blended schema. Universal J Comput Sci Eng Technol 1(2):133–140
Revett K (2009) A bioinformatics based approach to user authentication via keystroke dynamics. Int J Control Autom Syst 7(1):7–15
Rybnik M, Tabedzki M, Saeed K (2008) A keystroke dynamics based system for user identification. In: Computer information systems and industrial management applications CISIM’08. 7th, pp 225–230. IEEE
Sanchez-Reillo R, Sanchez-Avila C, Gonzales-Marcos A (2000) Biometric identification through hand geometry measurements. IEEE Trans Pattern Anal Mach Intell 22(10):1168–1171
Shen C, Guan X, Cai J (2010) A hypo-optimum feature selection strategy for mouse dynamics in continuous identity authentication and monitoring, pp 349e53 [IEEE International Conference on Information Theory and Information Security]
Shimshon T, Moskovitch R, Rokach L, Elovici Y (2010) Clustering di-graphs for continuously verifying users according to their typing patterns. In: Electrical and Electronics Engineers in Israel (IEEEI) IEEE 26th Convention of, pp. 000445-000449. IEEE
Singh S, Arya KV (2011) Key classification: a new approach in free text keystroke authentication system. In: 2011 3rd pacific-asia conference on circuits, communications and system (PACCS), pp 1–5. IEEE
Song R (2010) Advanced smart card based password authentication protocol. Computer Standards and Interfaces 32(5):321–325
Stockton GR, Lisowski W, Press JS, Shapiro N (1980) Authentication by keystroke timing: Stockton Some preliminary results. No. RAND-R-2526-NSF RAND CORP SANTA MONICA CA
Vezzetti E, Marcolin F, Tornincasa S, Ulrich L, Dagnes N (2017) 3D geometry-based automatic landmark localization in presence of facial occlusions. Multimed Tools Appl 77:1–29
Visumathi J, Jayarin JP (2015) “C”. J Appl Secur Res 10(3):375–384
Wan M, Lai Z, Yang G, Yang Z, Zhang F, Zheng H (2017) Local graph embedding based on maximum margin criterion via fuzzy set. Fuzzy Set Syst 318:120–131
Wan M, Li M, Yang G, Gai S, Jin Z (2014) Feature extraction using two-dimensional maximum embedding difference. Inform Sci 274:55–69
Wan M, Yang G, Gai S, Yang Z (2017) Two-dimensional discriminant locality preserving projections (2DDLPP) and its application to feature extraction via fuzzy set. Multimed Tools Appl 76(1):355–371
Xu J, Zhu W-T, Feng D-G (2009) An improved smart card based password Authentication scheme with provable security. Computer Standards and Interfaces 31 (4):723–728
Yu E, Cho S (2003) Novelty detection approach for keystroke dynamics identity verification. In: International conference on intelligent data engineering and automated learning, pp 1016–1023. Springer, Berlin
Zheng N, Paloski A, Wang H (2011) An efficient user verification system via mouse movements, pp 1e12 [ACM Conference on Computer and Communications Security]
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Neha, Chatterjee, K. Biometric re-authentication: an approach towards achieving transparency in user authentication. Multimed Tools Appl 78, 6679–6700 (2019). https://doi.org/10.1007/s11042-018-6448-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6448-9