Abstract
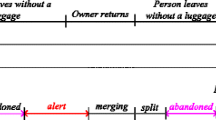
Intelligent Visual Surveillance is an important and challenging research field of image processing and computer vision. To prevent the ecological and economical losses from bomb blasting, an intelligent visual surveillance is required to keep an eye on public areas, infrastructures and discriminate an unattended object left among multiple objects at public places. An unattended object without its owner since a long time at public place is considered as an abandoned object. Identification of an abandoned object on real-time can prevent the terrorists attack through an automated video surveillance system. In recent decade, a good number of publications have been presented in the field of intelligent visual surveillance to identify the abandoned or removed objects. Furthermore, few surveys can be seen in the literature for the various human activity recognition but none of them focused deeply on abandoned or removed object detection in a review. In this paper, we present the state-of-the-art which demonstrates the overall progress of abandoned or removed object detection from the surveillance videos in the last decade. We include a brief introduction of the abandoned object detection with its issues and challenges. To acknowledge to the new researchers of this field, core technologies, and frequently used general steps to recognize abandoned or removed objects have been discussed in the literature such as foreground extraction, static object detection based on non-tracking or tracking approaches, feature extraction, classification and activity analysis to recognize abandoned object. The objective of this paper is to provide the literature review in the field of abandoned or removed object recognition from visual surveillance systems with its general framework to the researchers of this field.




Similar content being viewed by others
References
Aggarwal JK, Ryoo MS (2011) Human activity analysis: a review. ACM Comput Surveys (CSUR) 43(3):16
Arsic D, Hofmann M, Schuller B, Rigoll G (2007) Multi-camera person tracking and left luggage detection applying homographic transformation. In: Proceeding Tenth IEEE International Workshop on Performance Evaluation of Tracking and Surveillance, PETS
Auvinet E, Grossmann E, Rougier C, Dahmane M, Meunier J (2006) Left-luggage detection using homographies and simple heuristics. In: Proc. 9th IEEE International Workshop on Performance Evaluation in Tracking and Surveillance (PETS06), pp. 51Citeseer
Bangare PS, Uke NJ, Bangare SL (2012) Implementation of abandoned object detection in real time environment. Int J Comput Appl 57(12)
Beyan C, Yigit A, Temizel A (2011) Fusion of thermal-and visible-band video for abandoned object detection. J Electron Imaging 20(3):033,001–033,001
Beynon MD, Van Hook DJ, Seibert M, Peacock A, Dudgeon D (2003) Detecting abandoned packages in a multi-camera video surveillance system. In: Advanced Video and Signal Based Surveillance, 2003. Proceedings. IEEE Conference on, 221–228. IEEE
Bhargava M, Chen CC, Ryoo MS, Aggarwal JK (2009) Detection of object abandonment using temporal logic. Mach Vis Appl 20(5):271–281
Bird N, Atev S, Caramelli N, Martin R, Masoud O, Papanikolopoulos N (2006) Real time, online detection of abandoned objects in public areas. In: Robotics and Automation, 2006. ICRA 2006. Proceedings 2006 IEEE International Conference on, pp. 3775-3780.IEEE
Bouwmans T (2014) Traditional and recent approaches in background modeling for foreground detection: an overview. Comput Sci Rev 11:31–66
Breiman L (2001) Random forests. Mach Learn 45(1):5–32
Calderara S, Vezzani R, Prati A, Cucchiara R (2005) Entry edge of field of view for multicamera tracking in distributed video surveillance. In: Advanced Video and Signal Based Surveillance, 2005. AVSS 2005. IEEE Conference on. 93–98. IEEE
Candamo J, Shreve M, Goldgof DB, Sapper DB, Kasturi R (2010) Understanding transit scenes: a survey on human behavior-recognition algorithms. Intel Trans Syst, IEEE Trans 11(1):206–224
Cheng S, Luo X, Bhandarkar SM (2007) A multiscale parametric background model for stationary foreground object detection. In: Motion and Video Computing, 2007. WMVC'07. IEEE Workshop on. 18–18. IEEE
Chitra M, Geetha MK, Menaka L et al (2013) Occlusion and abandoned object detection for surveillance applications. Int J Comput Appl Technol Res 2(6):708 meta
Chuang CH, Hsieh JW, Tsai LW, Ju PS, Fan KC (2008) Suspicious object detection using fuzzy-color histogram. In: Circuits and Systems, 2008. ISCAS 2008. IEEE International Symposium on. 3546–3549. IEEE
Chuang CH, Hsieh JW, Tsai LW, Chen SY, Fan KC (2009) Carried object detection using ratio histogram and its application to suspicious event analysis. Circ Syst Video Technol, IEEE Trans 19(6):911–916
Collazos A, Fernandez-Lopez D, Montemayor AS, Pantrigo JJ, Delgado ML (2013) Abandoned object detection on controlled scenes using kinect. In: Natural and Artificial Computation in Engineering and Medical Applications, pp. 169–178. Springer
Cortes C, Vapnik V (1995) Support-vector networks. Mach Learn 20(3):273–297
Cucchiara R, Grana C, Piccardi M, Prati A (2003) Detecting moving objects, ghosts, and shadows in video streams. Patt Anal Mach Intel, IEEE Trans 25(10):1337–1342
Denman S, Chandran V, Sridharan S (2008) Abandoned object detection using multi-layer motion detection. In: Proceedings of International Conference on Signal Processing and Communication Systems 2007, pp. 439-448. DSP for Communication Systems
Elgammal A, Harwood D, Davis L (2000) Non-parametric model for background subtraction. In: Computer VisionECCV 2000, pp. 751-767. Springer
Ellingsen K (2008) Salient event-detection in video surveillance scenarios. In: Proceedings of the 1st ACM workshop on Analysis and retrieval of events/actions and workflows in video streams, pp. 57-64. ACM
Evangelio RH, Sikora T (2010) Static object detection based on a dual background model and a finite-state machine. EURASIP J Image Video Proc 2011(1):858,502
Evangelio, R.H., Senst, T., Sikora, T. (2011) Detection of static objects for the task of video surveillance. In: Applications of Computer Vision (WACV), 2011 IEEE Workshop on, pp. 534-540. IEEE
Fan Q, Pankanti S (2011) Modeling of temporarily static objects for robust abandoned object detection in urban surveillance. In: Advanced Video and Signal-Based Surveillance (AVSS), 2011 8th IEEE International Conference on. 36–41. IEEE
Fan Q, Pankanti S (2012) Robust foreground and abandonment analysis for large-scale abandoned object detection in complex surveillance videos. In: Advanced Video and Signal-Based Surveillance (AVSS), 2012 IEEE Ninth International Conference on, pp. 58-63. IEEE
Fan, Q., Gabbur, P., Pankanti, S. (2013) Relative attributes for large-scale abandoned object detection. In: Computer Vision (ICCV), 2013 IEEE International Conference on, pp. 2736-2743. IEEE
Femi PS, Thaiyalnayaki K (2013) Detection of abandoned and stolen objects in videos using mixture of gaussians. International Journal of Computer Applications 70(10)
Fernandez-Caballero A, Castillo JC, Rodriguez-Sanchez JM (2012) Human activity monitoring by local and global finite state machines. Expert Syst Appl 39(8):6982–6993
Ferrando S, Gera G, Regazzoni C (2006) Classication of unattended and stolen objects in video-surveillance system. In: Video and Signal Based Surveillance, 2006. AVSS'06. IEEE International Conference on, pp. 21-21. IEEE
Ferryman J, Hogg D, Sochman J, Behera A, Rodriguez-Serrano JA, Worgan S, Li L, Leung V, Evans M, Cornic P et al (2013) Robust abandoned object detection integrating wide area visual surveillance and social context. Pattern Recogn Lett 34(7):789–798
Foggia P, Greco A, Saggese A, Vento M (2015) A method for detecting long term left baggage based on heat map
Foresti GL, Marcenaro L, Regazzoni CS (2002) Automatic detection and indexing of videoevent shots for surveillance applications. Multimed, IEEE Trans 4(4):459–471
Foresti GL, Mahonen P, Regazzoni CS (2012) Multimedia video-based surveillance systems: Requirements, Issues and Solutions, vol. 573. Springer Science & Business Media
Foucher S, Lalonde M, Gagnon L (2011) A system for airport surveillance: detection of people running, abandoned objects, and pointing gestures. In: SPIE Defense, Security, and Sensing, pp. 805,610-805,610. International Society for Optics and Photonics
Gouaillier V, Fleurant A (2009) Intelligent video surveillance: Promises and challenges. Technological and commercial intelligence report, CRIM and Techn^opole Defence and Security 456-468
Guler S, Farrow MK (2006) Abandoned object detection in crowded places. In: Proc. of PETS, pp. 18-23. Citeseer
Guler S, Silverstein J, Pushee IH et al. (2007) Stationary objects in multiple object tracking. In: Advanced Video and Signal Based Surveillance, 2007. AVSS 2007. IEEE Conference on, pp. 248-253. IEEE
Haritaoglu I, Cutler R, Harwood D, Davis LS (1999) Backpack: Detection of people carrying objects using silhouettes. In: Computer Vision, 1999. The Proceedings of the Seventh IEEE International Conference on, vol. 1, pp. 102-107. IEEE
Haritaoglu I, Harwood D, Davis LS (2000) W 4: real-time surveillance of people and their activities. Patt Anal Mach Intel, IEEE Trans 22(8):809–830
Hoferlin M, Hoferlin B, Weiskopf D, Heidemann G (2015) Uncertainty-aware video visual analytics of tracked moving objects. J Spatial Inform Sci 2:87–117
Hu, M.K. (1962) Visual pattern recognition by moment invariants. information Theory, IRE Transactions on 8(2), 179-187
Hu W, Tan T, Wang L, Maybank S (2004) A survey on visual surveillance of object motion and behaviors. Systems, Man, and Cybernetics, Part C: Appl Rev, IEEE Trans 34(3):334–352
Image. URL https://www.boardofstudies.nsw.edu.au/bosstats/images/2011/2011-crowds-8-lg:jpg
Image (Accessed on 01 June, 2016). URL https://www.123rf.com/stockphoto/exhibitioncrowd:html
Isard M, Blake A (1998) Condensation conditional density propagation for visual tracking. Int J Comput Vis 29(1):5–28
Jalal AS, Singh V (2012) The state-of-the-art in visual object tracking. Informatica 36(3)
Javed O, Shah M (2002) Tracking and object classification for automated surveillance. In: Computer Vision ECCV 2002, pp. 343–357. Springer
Joglekar UA, Awari SB, Deshmukh SB, Kadam DM, Awari RB (2014) An abandoned object detection system using background segmentation. In: International Journal of Engineering Research and Technology, vol. 3. ESRSA Publications
Kalman RE (1960) A new approach to linear filtering and prediction problems. J Fluids Eng 82(1):35–45
Khan S, Shah M (2003) Consistent labeling of tracked objects in multiple cameras with overlapping fields of view. Patt Anal Mach Intel, IEEE Trans 25(10):1355–1360
Khan SM, Shah M (2006) A multiview approach to tracking people in crowded scenes using a planar homography constraint. In: Computer Vision ECCV 2006, pp. 133-146. Springer
Kim J, Kim D (2014) Static region classication using hierarchical finite state machine. In: Image Processing (ICIP), 2014 IEEE International Conference on, pp. 2358{2362. IEEE
Kitagawa G (1987) Non-gaussian statespace modeling of nonstationary time series. J Am Stat Assoc 82(400):1032–1041
Kong H, Audibert JY, Ponce J (2010) Detecting abandoned objects with a moving camera. Image Proc, IEEE Trans 19(8):2201–2210
Krahnstoever N, Tu P, Sebastian T, Perera A, Collins R (2006) Multi-view detection and tracking of travelers and luggage in mass transit environments. In: In Proc. Ninth IEEE International Workshop on Performance Evaluation of Tracking and Surveillance (PETS), vol. 258
Lavee G, Khan L, Thuraisingham B (2005) A framework for a video analysis tool for suspicious event detection. 79–84
Lavee G, Khan L, Thuraisingham B (2007) A framework for a video analysis tool for suspicious event detection. Multimed Tools Appl 35(1):109–123
Li L, Luo R, Ma R, Huang W, Leman K (2006) Evaluation of an ivs system for abandoned object detection on pets 2006 datasets. In: Proceedings of the 9th IEEE International Workshop on Performance Evaluation in Tracking and Surveillance (PETS'06), pp. 91-Citeseer
Li Q, Mao Y, Wang Z, Xiang W (2009) Robust real-time detection of abandoned and removed objects. In: Image and Graphics, 2009. ICIG'09. Fifth International Conference on, pp. 156-161. IEEE
Li X, Zhang C, Zhang D (2010) Abandoned objects detection using double illumination invariant foreground masks. In: Pattern Recognition (ICPR), 2010 20th International Conference on, pp. 436-439. IEEE
Liao HH, Chang JY, Chen LG (2008) A localized approach to abandoned luggage detection with foreground-mask sampling. In: Advanced Video and Signal Based Surveillance, 2008. AVSS'08. IEEE Fifth International Conference on, pp. 132-139. IEEE
Lin K, Chen SC, Chen CS, Lin DT, Hung YP (2014) Left-luggage detection from finite state-machine analysis in static-camera videos. In: 2014 22nd International Conference on Pattern Recognition (ICPR), pp. 4600-4605. IEEE
Lin K, Chen SC, Chen CS, Lin DT, Hung YP (2015) Abandoned object detection via temporal consistency modeling and back-tracing verification for visual surveillance. Info Forensics Sec, IEEE Trans 10(7):1359–1370
Lo B, Velastin S (2001) Automatic congestion detection system for underground platforms. In: Intelligent Multimedia, Video and Speech Processing, 2001. Proceedings of 2001 International Symposium on, pp. 158-161. IEEE
Lu S, Zhang J, Feng D (2006) A knowledge-based approach for detecting unattended packages in surveillance video. In: Video and Signal Based Surveillance, 2006. AVSS'06. IEEE International Conference on, pp. 110-110. IEEE
Lu S, Zhang J, Feng D (2007) An efficient method for detecting ghost and left objects in surveillance video. In: Advanced Video and Signal Based Surveillance, 2007. AVSS 2007. IEEE Conference on, pp. 540-545. IEEE
Lu S, Zhang J, Feng DD (2007) Detecting unattended packages through human activity recognition and object association. Pattern Recogn 40(8):2173–2184
Lv F, Song X, Wu B, Singh VK, Nevatia R (2006) Left luggage detection using Bayesian inference. In: Proc. of IEEE Int. Workshop on Performance Evaluation of Tracking and Surveillance, pp. 83-90. Citeseer
Maddalena L, Petrosino A (2013) Stopped object detection by learning foreground model in videos. Neural Netwo Learn Syst, IEEE Trans 24(5):723–735
Mahin FS, Islam MN, Schaefer G, Ahad MAR (2015) A simple approach for abandoned object detection. In: Proceedings of the International Conference on Image Processing, Computer Vision, and Pattern Recognition (IPCV), p. 427. The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp)
Martinez-del Rincon J, Herrero-Jaraba JE, Gomez JR, Orrite-Urunuela C (2006) Automatic left luggage detection and tracking using multi-camera ukf. In: Proceedings of the 9th IEEE International Workshop on Performance Evaluation in Tracking and Surveillance (PETS'06), pp. 59-66
Mathew R, Yu Z, Zhang J (2005) Detecting new stable objects in surveillance video. In: Multimedia Signal Processing, 2005 IEEE 7th Workshop on, pp. 1-4. IEEE
McHugh JM, Konrad J, Saligrama V, Jodoin PM (2009) Foreground-adaptive background subtraction. Sign Proc Lett, IEEE 16(5):390–393
Miguel JCS, Martinez JM (2008) Robust unattended and stolen object detection by fusing simple algorithms. In: Advanced Video and Signal Based Surveillance, 2008. AVSS'08. IEEE Fifth International Conference on, pp. 18-25. IEEE
Mittal A, Davis L (2001) Unified multi-camera detection and tracking using region-matching. In: Multi-Object Tracking, 2001. Proceedings. 2001 IEEE Workshop on, pp. 3-10. IEEE
Mukherjee D, Wu QJ, Nguyen TM (2014) Gaussian mixture model with advanced distance measure based on support weights and histogram of gradients for background suppression. IEEE Trans Ind Inform 10(2):1086–1096
Nam Y (2015) Real-time abandoned and stolen object detection based on spatio-temporal features in crowded scenes. Multimedia Tools and Applications pp. 1-26
Otoom AF, Gunes H, Piccardi M (2008) Feature extraction techniques for abandoned object classification in video surveillance. In: 2008 15th IEEE International Conference on Image Processing, pp. 1368-1371. IEEE
Pan J, Fan Q, Pankanti S (2011) Robust abandoned object detection using region-level analysis. In: Image Processing (ICIP), 2011 18th IEEE International Conference on, pp. 3597-3600. IEEE
Pavithradevi MK, Scholar P (2014) Detection of suspicious activities in public areas using staged matching technique. IJAICT 1
Pets 2001 benchmark data, (2001). URL http://www.cvg.rdg.ac.uk/PETS2001/
Pets 2007 benchmark data (2007). URL http://www.cvg.rdg.ac.uk/PETS2006/data.html
Piccardi, M. (2004) Background subtraction techniques: a review. In: Systems, man and cybernetics, 2004 IEEE international conference on, vol. 4, pp. 3099-3104. IEEE
Popoola OP, Wang K (2012) Video-based abnormal human behavior recognitiona review. Systems, Man, and Cybernetics, Part C: Appl Rev, IEEE Trans 42(6):865–878
Poppe R (2010) A survey on vision-based human action recognition. Image Vis Comput 28(6):976–990
Porikli F (2007) Detection of temporarily static regions by processing video at different frame rates. In: Advanced Video and Signal Based Surveillance, 2007. AVSS 2007. IEEE Conferenceon, pp. 236-241. IEEE
Porikli, F., Yin, Z. (2007) Temporally static region detection in multi-camera systems. In: Proc. 10th IEEE Int. Workshop on Performance evaluation of tracking and surveillance: PETS, pp. 79-86
Porikli, F., Ivanov, Y., Haga, T. (2008) Robust abandoned object detection using dual foregrounds. EURASIP Journal on Advances in Signal Processing 2008, 30
Prabhakar G, Ramasubramanian B (2012) An efficient approach for real time tracking of intruder and abandoned object in video surveillance system. Int J Comput Appl 54(17):22–27
Regazzoni CS, Fabri G, Vernazza G (1998) Advanced video-based surveillance systems, vol. 488. Springer Science & Business Media
Sacchi C, Regazzoni CS (2000) A distributed surveillance system for detection of abandoned objects in unmanned railway environments. Vehicular Technol, IEEE Trans 49(5):2013–2026
Sajith, K., Nair, K.R. (2013) Abandoned or removed objects detection from surveillance video using codebook. In: International Journal of Engineering Research and Technology, vol. 2. ESRSA Publications
SanMiguel JC, Martinez JM (2012) A semantic-based probabilistic approach for real-time video event recognition. Comput Vis Image Underst 116(9):937–952
SanMiguel J, Caro L, Martinez J (2012) Pixel-based colour contrast for abandoned and stolen object discrimination in video surveillance. Electron Lett 48(2):86–87
Singh VK, Atrey PK, Kankanhalli MS (2008) Coopetitive multi-camera surveillance using model predictive control. Mach Vis Appl 19(5-6):375–393
Singh, R., Vishwakarma, S., Agrawal, A., Tiwari, M. (2010) Unusual activity detection for video surveillance. In: Proceedings of the First International Conference on Intelligent Interactive Technologies and Multimedia, pp. 297-305. ACM
Smith KC, Quelhas P, Gatica-Perez D (2006) Detecting abandoned luggage items in a public space. Tech. rep., IDIAP
Spengler M, Schiele B (2003) Automatic detection and tracking of abandoned objects. In: Proceedings of the Joint IEEE International Workshop on Visual Surveillance and Performance Evaluation of Tracking and Surveillance. Citeseer
Stauffer C, Grimson WEL (1999) Adaptive background mixture models for real-time tracking. In: Computer Vision and Pattern Recognition, 1999. IEEE Computer Society Conference on, vol. 2. IEEE
Stringa E, Regazzoni CS (1998) Content-based retrieval and real time detection from video sequences acquired by surveillance systems. In: Image Processing, 1998. ICIP98. Proceedings. 1998 International Conference on, pp. 138-142. IEEE
Stringa E, Regazzoni CS (2000) Real-time video-shot detection for scene surveillance applications. Image Proc, IEEE Trans 9(1):69–79
Szwoch G (2016) Extraction of stable foreground image regions for unattended luggage detection. Multimed Tools Appl 75(2):761–786
Tejas Naren TN, Shankar Siddharth KA, Venkat Krishnan S, Sanjeevi LR (2014) Abandoned object detection for automated video surveillance using hadoop. International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering 3(3). http://www.ijareeie.com/upload/2014/apr14-specialissue3/21_R22.pdf
Tian Y, Feris RS, Liu H, Hampapur A, Sun MT (2011) Robust detection of abandoned and removed objects in complex surveillance videos. Systems, Man, and Cybernetics, Part C: Appl Rev, IEEE Trans 41(5):565–576
Tian Y, Senior A, Lu M (2012) Robust and efficient foreground analysis in complex surveillance videos. Mach Vis Appl 23(5):967–983
Tripathi RK, Jalal AS (2014) A framework for suspicious object detection from surveillance video. Int J Mach Intel Sensory Sign Proc 1(3):251–266
Tripathi RK, Jalal AS, Bhatnagar C (2013) A framework for abandoned object detection from video surveillance. In: Computer Vision, Pattern Recognition, Image Processing and Graphics (NCVPRIPG), 2013 Fourth National Conference on, pp. 1-4. IEEE
Tsai RY (1986) An efficient and accurate camera calibration technique for 3d machine vision. In: Proc. IEEE Conf. on Computer Vision and Pattern Recognition, 1986
Vezzani R, Cucchiara R (2010) Video surveillance online repository (visor): an integrated framework. Multimed Tools Appl 50(2):359–380
Wan EA, Van Der Merwe R (2000) The unscented kalman filter for nonlinear estimation. In: Adaptive Systems for Signal Processing, Communications, and Control Symposium 2000. AS-SPCC. The IEEE 2000, pp. 153-158. IEEE
Webb GI (2000) Multiboosting: a technique for combining boosting and wagging. Mach Learn 40(2):159–196
Witten I, Frank E (2000) Data mining: Practical machine learning tools with java implementations. MODELO MATEMATICO PARAMETRICO DE ESTIMACION PARA PROYECTOS DE DATA MINING IDMCOMOf
Wren CR, Azarbayejani A, Darrell T, Pentland AP (1997) Pfinder: real-time tracking of the human body. Patt Anal Mach Intel, IEEE Trans 19(7):780–785
Yadav P, Jahagirdar A (2015) A static object detection in image sequences by self organizing background subtraction
Yang Z, Rothkrantz L (2011) Surveillance system using abandoned object detection. In: Proceedings of the 12th International Conference on Computer Systems and Technologies, pp. 380-386. ACM
Yang T, Pan Q, Li SZ, Li J (2004) Multiple layer based background maintenance in complex environment. In: Image and Graphics (ICIG'04), Third International Conference on, pp. 112-115. IEEE
Yilmaz A, Javed O, Shah M (2006) Object tracking: a survey. A Comput Surveys (CSUR) 38(4):13
Yue, Z., Zhou, S.K., Chellappa, R. (2004) Robust two-camera tracking using homography. In: Acoustics, Speech, and Signal Processing, 2004. Proceedings.(ICASSP'04). IEEE International Conference on, vol. 3, pp. iii −1. IEEE
Zeng Y, Lan J, Ran B, Gao J, Zou J (2015) A novel abandoned object detection system based on three-dimensional image information. Sensors 15(3):6885–6904
Zhou Y, Benois-Pineau J, Nicolas H (2010) Multi-object particle filter tracking with automatic event analysis. In: Proceedings of the first ACM international workshop on Analysis and retrieval of tracked events and motion in imagery streams, pp. 21-26. ACM
Ziaeefard M, Bergevin R (2015) Semantic human activity recognition: a literature review. Pattern Recogn 8(48):2329–2345
Zin TT, Tin P, Toriu T, Hama H (2012) A novel probabilistic video analysis for stationary object detection in video surveillance systems. IAENG Int J Comput Sci 39(3):295–306
Zin TT, Tin P, Toriu T, Hama H (2012) A probability-based model for detecting abandoned objects in video surveillance systems. In: Proceedings of the World Congress on Engineering, 2
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tripathi, R.K., Jalal, A.S. & Agrawal, S.C. Abandoned or removed object detection from visual surveillance: a review. Multimed Tools Appl 78, 7585–7620 (2019). https://doi.org/10.1007/s11042-018-6472-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6472-9