Abstract
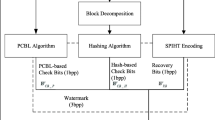
In this paper, we present a method for detecting and restoring tampered information in natural and text images. To take the detection ability, invisibility, and recovery quality into account for both natural and text images, this work generates the authentication watermark for each 4 × 4 block by a hash function and a variable capacity recovery watermark for each 2 × 2 block by allocating more bits to the textural blocks and fewer bits to the smooth ones. The authentication watermark and the recovery one are embedded in the original image by adopting different strategies based on a secret key. The multi-stage neighbor detection strategy is designed to locate the tampered image blocks accurately. The proposed scheme outperforms in invisibility, with detecting tampered locations and recovery of the tampered regions. The simulation results show that the proposed scheme achieves better recovery quality and invisibility for natural and text images due to a variable-capacity recovery watermark and superior localization. Further, the proposed method computationally is less expensive compared with the existing works.




















Similar content being viewed by others
References
Atallah MJ, Raskin V, Hempelmann CF, Karahan M, Sion R, Topkara U, Triezenberg KE (2002) Natural language watermarking and tamperproofing. In: International workshop on information hiding, pp 196–212
Benrhouma O, Hermassi H, Belghith S (2015) Tamper detection and self-recovery scheme by dwt watermarking. Nonlinear Dyn 79(3):1817–1833
Betancourth GP (2012) Fragile watermarking scheme for image authentication. In: 2012 5th international conference on human system interactions (HSI), pp 168–174
Brassil JT, Low S, Maxemchuk NF (1999) Copyright protection for the electronic distribution of text documents. Proc IEEE 87(7):1181–1196
Chang CC, Hu YS, Lu TC (2006) A watermarking-based image ownership and tampering authentication scheme. Pattern Recogn Lett 27(5):439–446
Dadkhah S, Manaf AA, Hori Y, Hassanien AE, Sadeghi S (2014) An effective svd-based image tampering detection and self-recovery using active watermarking. Signal Process Image Commun 29(10):1197–1210
Fridrich J, Goljan M (1999) Images with self-correcting capabilities. In: Proceedings of 1999 international conference on image processing, 1999. ICIP 99, vol 3, pp 792–796
Fridrich J, Goljan M, Memon ND (2002) Cryptanalysis of the yeung-mintzer fragile watermarking technique. J Electron Imaging 11(2):262–275
Han SH, Chu CH (2010) Content-based image authentication: current status, issues, and challenges. Int J Inf Secur 9(1):19–32
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Multimed Tools Appl 39(1):1–46
He HJ, Zhang JS, Chen F (2009) Adjacent-block based statistical detection method for self-embedding watermarking techniques. Signal Process 89(8):1557–1566
He HJ, Zhang JS, Tai HM (2009) Self-recovery fragile watermarking using block-neighborhood tampering characterization. In: International workshop on information hiding, pp 132–145
Hu YC, Choo KKR, Chen WL (2017) Tamper detection and image recovery for btc-compressed images. Multimed Tools Appl 76(14):15435–15463
Huazheng X, Xingming S, Chengliang T (2006) A new fragile watermarking scheme for text documents authentication. Wuhan Univ J Nat Sci 11(6):1661–1666
Ji P, Qin C, Tang Z (2016) Fragile watermarking with self-recovery capability via absolute moment block truncation coding. In: International conference on cloud computing and security, pp 104–113
Kurniawan F, Khalil MS, Khan MK, Alginahi YM (2014) Dwt+ lsb-based fragile watermarking method for digital quran images. In: 2014 international symposium on biometrics and security technologies (ISBAST), pp 290–297
Lee TY, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 41(11):3497–3506
Li C, Wang Y, Ma B, Zhang Z (2011) A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure. Comput Electr Eng 37 (6):927–940
Lin PL, Hsieh CK, Huang PW (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recognit 38(12):2519–2529
Lin CC, Huang Y, Tai WL (2017) A novel hybrid image authentication scheme based on absolute moment block truncation coding. Multimed Tools Appl 76 (1):463–488
Liu Y, Nie L, Han L, Zhang L, Rosenblum DS (2015) Action2activity: recognizing complex activities from sensor data. In: IJCAI, vol 2015, pp 1617–1623
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: sensor-based activity recognition. Neurocomputing 181:108–115
Liu Y, Zhang L, Nie L, Yan Y, Rosenblum DS (2016) Fortune teller: predicting your career path. In: AAAI, vol 2016, pp 201–207
Liu Y, Zheng Y, Liang Y, Liu S, Rosenblum DS (2016) Urban water quality prediction based on multi-task multi-view learning
Niu D, Wang H, Cheng M, Zhou L (2015) Self-embedding watermarking scheme based on mds codes. In: International workshop on digital watermarking, pp 250–258
Nyeem H, Boles W, Boyd C (2016) Modelling attacks on self-authentication watermarking. Multimed Tools Appl 75(23):15849–15880
Olanrewaju RF, Fajingbesi FE, Ishak NAB (2016) Watermarking in protecting and validating the integrity of digital information: a case study of the holy scripture. In: 2016 6th international conference on information and communication technology for the Muslim World (ICT4M), pp 222–227
Piper A, Safavi-Naini R (2013) Scalable fragile watermarking for image authentication. IET Inf Secur 7(4):300–311
Puhan NB, Ho AT (2005) Restoration in secure text document image authentication using erasable watermarks. In: International conference on computational and information science, pp 661–668
Qian Z, Feng G, Zhang X, Wang S (2011) Image self-embedding with high-quality restoration capability. Digital Signal Process 21(2):278–286
Qin C, Chang CC, Chen KN (2013) Adaptive self-recovery for tampered images based on vq indexing and inpainting. Signal Process 93(4):933–946
Qin C, Wang H, Zhang X, Sun X (2016) Self-embedding fragile watermarking based on reference-data interleaving and adaptive selection of embedding mode. Inf Sci 373:233–250
Rosales-Roldan L, Cedillo-Hernandez M, Nakano-Miyatake M, Perez-Meana H, Kurkoski B (2013) Watermarking-based image authentication with recovery capability using halftoning technique. Signal Process Image Commun 28(1):69–83
Shi H, Wang X, Li M, Bai J, Feng B (2017) Secure variable-capacity self-recovery watermarking scheme. Multimed Tools Appl 76(5):6941–6972
Singh D, Singh SK (2017) Dct based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76(1):953–977
Singh P, Agarwal S (2016) An efficient fragile watermarking scheme with multilevel tamper detection and recovery based on dynamic domain selection. Multimed Tools Appl 75(14):8165–8194
Sreenivas K, Prasad VK (2018) Fragile watermarking schemes for image authentication: a survey. Int J Mach Learn Cybern 9(7):1193–1218
Tong X, Liu Y, Zhang M, Chen Y (2013) A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process Image Commun 28(3):301–308
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13 (4):600–612
Wang X, Zhang D, Guo X (2013) A novel image recovery method based on discrete cosine transform and matched blocks. Nonlinear Dyn 73(3):1945–1954
Wang H, Ho AT, Li S (2014) A novel image restoration scheme based on structured side information and its application to image watermarking. Signal Process Image Commun 29(7):773–787
Yang CW, Shen JJ (2010) Recover the tampered image based on vq indexing. Signal Process 90(1): 331–343
Zhang X, Qian Z, Ren Y, Feng G (2011) Watermarking with flexible self-recovery quality based on compressive sensing and compositive reconstruction. IEEE Trans Inf Forensics Secur 6(4):1223–1232
Zhang X, Wang S, Qian Z, Feng G (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495
Zhang X, Wang S, Qian Z, Feng G (2011) Self-embedding watermark with flexible restoration quality. Multimed Tools Appl 54(2):385–395
Zhang J, Zhang Q, Lv H (2013) A novel image tamper localization and recovery algorithm based on watermarking technology. Optik-Int J Light Elect Opt 124 (23):6367–6371
Acknowledgements
This work is supported by National Natural Science Foundation of China (NSFC) Under grants (61872303,61461047), and Technology Innovation Talent Program of Science & Technology Department of Sichuan Province(2018RZ0143).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hemida, O., Huo, Y., He, H. et al. A restorable fragile watermarking scheme with superior localization for both natural and text images. Multimed Tools Appl 78, 12373–12403 (2019). https://doi.org/10.1007/s11042-018-6664-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6664-3