Abstract
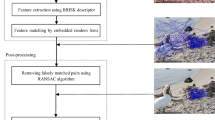
Copy move has become a simple and effective operation for image forgeries due to the advancement of image editing software, which is still challenging to be detected. In this paper, a novel method is proposed for copy move forgery detection based on Keypoint and Patch Match. Local Intensity Order Pattern (LIOP), a robust keypoint descriptor, is combined with SIFT to obtain reliable keypoints. After using g2NN to match the extracted keypoints, a new matched keypoint pair description model and a density grid-based filtering strategy are applied to removing the redundancy matched keypoint pairs. Finally an enhanced patch match approach is utilized to examine the matched keypoint pairs to accurately determine the existence of forgery. Compared with the state-of-the-art methods, the proposed method can detect copy move region more precisely according to the experimental result, even when detected objects are distorted by some processing such as rotation, scaling, JPEG compression and additional noise.












Similar content being viewed by others
References
Amerini I, Ballan L, Caldelli R, Bimbo AD, Serra G (2011) A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Trans Inf Forens Secur 6(3):1099–1110
Amerini I, Ballan L, Caldelli R, Bimbo AD, Tongo LD, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Process: Image Commun 28(6):659–669
Ardizzone E, Bruno A, Mazzola G (2015) Copy-move forgery detection by matching triangles of keypoints. IEEE Trans Inf Forens Secur 10:2084–2094
Barnes C, Shechtman E, Finkelstein A, Goldman DB (2009) PatchMatch: a randomized correspondence algorithm for structural image editing. ACM Trans Graph Proc SIGGRAPH 28(3):1–11
Bay H, Ess A, Tuytelaars T, Gool LV (2006) SURF: speeded up robust features. In: European conference on computer vision, pp 404–417
Bayram S, Sencar HT, Memon N (2009) An efficient and robust method for detecting copy-move forgery. In: IEEE International conference on acoustics, speech and signal processing, pp 1053–1056
Beis JS, Lowe DG (1997) Shape indexing using approximate nearest-neighbour search in high-dimensional spaces. In: International conference on computer vision and pattern recognition, pp 1000–1006
Bedi G, Venayagamoorthy G, Singh R, Brooks R, Wang K-C (2018) Review of internet of things (iot) in electric power and energy systems. IEEE Internet Things J PP:1–1. https://doi.org/10.1109/JIOT.2018.2802704
Cao G, Zhao Y, Ni R, Li X (2014) Contrast enhancement-based forensics in digital images. IEEE Trans Inf Forens Secur 9(3):515–525. https://doi.org/10.1109/TIFS.2014.2300937
Chen L, Lu W, Ni J, Sun W, Huang J (2013) Region duplication detection based on harris corner points and step sector statistics. J Vis Commun Image Represent 24(3):244–254
Chen J, Wei L, Fang Y, Liu X, Yeung Y, Xue Y (2018) Binary image steganalysis based on local texture pattern. J Vis Commun Image Represent 55:149–156
Chen J, Lu W, Yeung Y, Xue Y, Liu X, Lin C, Yue Z (2018) Binary image steganalysis based on distortion level co-occurrence matrix. Cmc-Comput Mater Continua 55(2):201–211
Chen X, Weng J, Lu W, Xu J (2018) Multi-gait recognition based on attribute discovery. IEEE Trans Pattern Anal Mach Intell 40(7):1697–1710
Chen X, Weng J, Lu W, Xu J, Weng J (2018) Deep manifold learning combined with convolutional neural networks for action recognition. IEEE Trans Neural Netw 29:3938–3952
Christlein V, Riess C, Jordan J, Riess C, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inf Forens Secur 7(6):1841–1854
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copy move forgery detection. IEEE Trans Inf Forens Secur 10(11):2284–2297
Emam M, Qi H, Zhang H (2018) Two-stage keypoint detection scheme for region duplication forgery detection in digital images. J Forensic Sci 63(1):102–111
Fan B, Wu F, Hu Z (2011) Aggregating gradient distributions into intensity orders: a novel local image descriptor. In: CVPR 2011, vol 1, pp 2377–2384
Fan Y, Li J, Wei L, Jian W (2017) Copy-move forgery detection based on hybrid features. Eng Appl Artif Intel 59:73–83
Feng B, Lu W, Sun W (2015) Secure binary image steganography based on minimizing the distortion on the texture. IEEE Trans Inf Forens Secur 10(2):243–255
Feng B, Lu W, Sun W (2015) Binary image steganalysis based on pixel mesh Markov transition matrix. J Vis Commun Image Represent 26:284–295
Feng B, Lu W, Sun W (2015) Novel steganographic method based on generalized k-distance n-dimensional pixel matching. Multimed Tools Appl 74(21):9623–9646
Fridrich J, Soukal D, Lukáš J (2003) Detection of copy-move forgery in digital images. In: Digital forensic research workshop, Cleveland, pp 19–23
Hu C, Xu Z, Liu Y, Mei L, Chen L, Luo X (2014) Semantic link network-based model for organizing multimedia big data. IEEE Trans Emerging Topics Comput 2(3):376–387
Huang Y, Lu W, Sun W, Long D (2011) Improved DCT-based detection of copy-move forgery in images. Forensic Sci Int 206(1-3):178–184
Huang X, Liu Z, Lu W, Liu H, Xiang S (2019) Fast and effective copy-move detection of digital audio based on auto segment. Int J Digital Crime Forensics (IJDCF) 11(2):47–62
Khotanzad A, Hong YH (1990) Invariant image recognition by zernike moments. IEEE Trans Pattern Anal Mach Intell 12(5):489–497
Kim HS, Lee H-K (2003) Invariant image watermark using zernike moments. IEEE Trans Circ Syst Video Technol 13(8):766–775
Kumar S (2015) A fast keypoint based hybrid method for copy move forgery detection. Int J Comput Digit Syst 4(2):91–99
Lee J-C (2015) Copy-move image forgery detection based on gabor magnitude. J Vis Commun Image Represent 31(Supplement C):320–334
Li J, Lu W (2016) Blind image motion deblurring with l 0 -regularized priors. J Vis Commun Image Represent 40:14–23
Li G, Wu Q, Tu D, Sun S (2007) A sorted neighborhood approach for detecting duplicated regions in image forgeries based on DWT and SVD. In: IEEE International conference on multimedia and expo, pp 1750–1753
Li L, Li S, Zhu H, Chu S-C, Roddick JF, Pan J-S (2013) An efficient scheme for detecting copy-move forged images by local binary patterns. J Inf Hiding Multimed Signal Process 4(1):46–56
Li X, Zhang W, Gui X, Yang B (2013) A novel reversible data hiding scheme based on two-dimensional difference-histogram modification. IEEE Trans Inf Forens Secur 8(7):1091–1100
Li L, Li S, Zhu H, Wu X (2014) Detecting copy-move forgery under affine transforms for image forensics. Comput Electr Eng 40(6):1951–1962
Li J, Li X, Bin Y, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forens Secur 10(3):507–518
Li J, Fan Y, Wei L, Wei S (2017) Keypoint-based copy-move detection scheme by adopting mscrs and improved feature matching. Multimed Tools Appl 76 (20):20483–20497
Li J, Lu W, Weng J, Mao Y, Li G (2018) Double jpeg compression detection based on block statistics. Multimed Tools Appl 77(24):31895–31910
Lin C, Lu W, Huang X, Liu K, Sun W, Lin H, Tan Z (2018) Copy-move forgery detection using combined features and transitive matching. Multimedia Tools and Applications
Lin C, Lu W, Sun W, Zeng J, Xu T, Lai J-H (2018) Region duplication detection based on image segmentation and keypoint contexts. Multimed Tools Appl 77(11):14241–14258
Liu Z, Lu W (2017) Fast copy-move detection of digital audio. In: 2017 IEEE Second international conference on data science in cyberspace (DSC), vol 1. IEEE, pp 625–629
Liu X, Lu W, Zhang Q, Huang J, Shi Y (2019) Downscaling factor estimation on pre-jpeg compressed images. IEEE Trans Circ Syst Video Technol PP (99):1–1. https://doi.org/10.1109/TCSVT.2019.2893353
Liu X, Lu W, Liu W, Luo S, Liang Y, Li M (2019) Image deblocking detection based on a convolutional neural network. IEEE Access 7:26432–26439. https://doi.org/10.1109/ACCESS.2019.2901020
Lowe DG (1999) Object recognition from local scale-invariant features. In: IEEE International conference on computer vision, vol 2, pp 1150–1157
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Lu W, He L, Yeung Y, Xue Y, Liu H, Feng B (2018) Secure binary image steganography based on fused distortion measurement. IEEE Trans Circ Syst Video Technol, 1–1. https://doi.org/10.1109/TCSVT.2018.2852702
Luo X, Song X, Li X, Zhang W, Lu J, Yang C, Liu F (2016) Steganalysis of hugo steganography based on parameter recognition of syndrome-trellis-codes. Multimed Tools Appl 75(21):13557–13583
Ma Y, Luo X, Li X, Bao Z, Zhang Y (2019) Selection of rich model steganalysis features based on decision rough set α -positive region reduction. IEEE Trans Circ Syst Vid Technol 29 (2):336–350. https://doi.org/10.1109/TCSVT.2018.2799243
Mahdian B, Saic S (2007) Detection of copy-move forgery using a method based on blur moment invariants. Forensic Sci Int 171(2):180–189
Muhammad K, Ahmad J, Farman H, Jan Z, Sajjad M, Baik SW (2015) A secure method for color image steganography using gray-level modification and multi-level encryption. KSII Trans Internet Inf Syst 9(5):1938–1962
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2016) A novel magic lsb substitution method (m-lsb-sm) using multi-level encryption and achromatic component of an image. Multimed Tools Appl 75(22):1–27
Muhammad K, Sajjad M, Baik SW (2016) Dual-level security based cyclic18 steganographic method and its application for secure transmission of keyframes during wireless capsule endoscopy. J Med Syst 40(5):1–16
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2017) Cisska-lsb: color image steganography using stego key-directed adaptive lsb substitution method. Multimed Tools Appl 76(6):8597–8626
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2018) Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst 86:951–960
Pan X, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inf Forens Secur 5(4):857–867
Popescu AC, Farid H (2004) Exposing digital forgeries by detecting duplicated image regions, Tech. rep., Dartmouth College, Computer Science
Pun C-M, Yuan X-C, Bi X-L (2015) Image forgery detection using adaptive oversegmentation and feature points matching. IEEE Trans Inf Forens Secur 10(8):1705–1716
Ryu SJ, Lee MJ, Lee HK (2010) Detection of copy-rotate-move forgery using zernike moments. In: International conference on information hiding, vol 6387, pp 51–65
Ryu S-J, Kirchner M, Lee M-J, Lee H-K (2013) Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Trans Inf Forens Secur 8(8):1355–1370
Shivakumar BL, Baboo SS (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues 8(4):199–205
Silva E, Carvalho T, Ferreira A, Rocha A (2015) Going deeper into copy-move forgery detection: exploring image telltales via multi-scale analysis and voting processes. J Vis Commun Image Represent 29(Supplement C):16–32
Teh CH, Chin RT (1988) On image analysis by the methods of moments. IEEE Trans Pattern Anal Mach Intell 10(4):496–513
Toldo R, Fusiello A (2008) Robust multiple structures estimation with J-Linkage. In: European conference on computer vision, pp 537–547
Wang Z, Fan B, Wu F (2011) Local intensity order pattern for feature description. In: International conference on computer vision, pp 603–610
Wang J, Li T, Shi Y, Lian S, Ye J (2017) Forensics feature analysis in quaternion wavelet domain for distinguishing photographic images and computer graphics. Multimed Tools Appl 76(22):23721–23737
Wang R, Lu W, Li J, Xiang S, Zhao X, Wang J (2018) Digital image splicing detection based on markov features in QDCT and QWT domain. Int J Digit Crime Forens (IJDCF) 10(4):90–107
Wang XY, Jiao LX, Wang XB, Yang HY, Niu PP (2019) Copy-move forgery detection based on compact color content descriptor and delaunay triangle matching. Multimed Tools Appl 78(2):2311–2344
Warif NBA, Wahab AWA, Idris MYI, Salleh R, Othman F (2017) Sift-symmetry: a robust detection method for copy-move forgery with reflection attack. J Vis Commun Image Represent 46(Supplement C):219–232
Weng S, Yao Z, Pan JS, Ni R (2008) Reversible watermarking based on invariability and adjustment on pixel pairs. IEEE Signal Process Lett 15(20):721–724
Xiao H, Lu W, Li R, Zhong N, Yeung Y, Chen J, Xue F, Sun W (2019) Defocus blur detection based on multiscale svd fusion in gradient domain. J Vis Commun Image Represent 59:52–61
Xiaolong L, Bin Y, Tieyong Z (2011) Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans Image Process Publ IEEE Signal Process Soc 20(12):3524–3533
Xiaolong L, Bin L, Bin Y, Tieyong Z (2013) General framework to histogram-shifting-based reversible data hiding. IEEE Trans Image Process 22 (6):2181–2191
Xin Y, Liao S, Pawlak M (2004) A multibit geometrically robust image watermark based on zernike moments. In: Proceedings of the 17th international conference on pattern recognition, 2004. ICPR 2004., vol 4, pp 861–864
Xin L, Li K, Yin J (2016) Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed Tools Appl 76(20):1–15
Xin L, Zheng Q, Ding L (2017) Data embedding in digital images using critical functions. Signal Processing Image Commun 58:146–156
Xin L, Guo S, Yin J, Wang H, Xiong L, Sangaiah AK (2018) New cubic reference table based image steganography. Multimed Tools Appl 77(8):10033–10050
Xinpeng Z, Shuozhong W (2006) Efficient steganographic embedding by exploiting modification direction. IEEE Commun Lett 10(11):781–783
Xinpeng Z, Shuozhong W, Zhenxing Q, Guorui F (2011) Reference sharing mechanism for watermark self-embedding. IEEE Trans Image Process 20(2):485–495
Xue Y, Liu W, Lu W, Yeung Y, Liu X, Liu H (2018) Efficient halftone image steganography based on dispersion degree optimization. J Real-Time Image Proc, 1–9
Yang F, Li J, Lu W, Weng J (2017) Copy-move forgery detection based on hybrid features. Eng Appl Artif Intel 59(Supplement C):73–83
Yi Z, Qin C, Zhang W, Liu F, Luo X (2018) On the fault-tolerant performance for a class of robust image steganography. Signal Process 146:99–111
Zhang Q, Lu W, Weng J (2016) Joint image splicing detection in dct and contourlet transform domain. J Vis Commun Image Represent 40:449–458
Zhang F, Lu W, Liu H, Xue F (2018) Natural image deblurring based on l0-regularization and kernel shape optimization. Multimed Tools Appl 77 (20):26239–26257
Zhang Q, Lu W, Wang R, Li G (2018) Digital image splicing detection based on Markov features in block dwt domain. Multimed Tools Appl 77(23):31239–31260
Zhenxing Q, Xinpeng Z, Shuozhong W (2014) Reversible data hiding in encrypted jpeg bitstream. IEEE Trans Multimed 16(5):1486–1491
Acknowledgments
This work is supported by the National Natural Science Foundation of China (No. U1736118), the Key Areas R&D Program of Guangdong (No. 2019B010136002), the Key Scientific Research Program of Guangzhou (No. 201804020068), the Natural Science Foundation of Guangdong (No. 2016A030313350), the Special Funds for Science and Technology Development of Guangdong (No. 2016KZ010103), Shanghai Minsheng Science and Technology Support Program (17DZ1205500), Shanghai Sailing Program (17YF1420000), the Fundamental Research Funds for the Central Universities (No. 16lgjc83 and No. 17lgjc45).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, K., Lu, W., Lin, C. et al. Copy move forgery detection based on keypoint and patch match. Multimed Tools Appl 78, 31387–31413 (2019). https://doi.org/10.1007/s11042-019-07930-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-07930-5